It could mean the difference between recovering your data or losing it forever.

In some pre-configured Windows Pro or Home editions, BitLocker may encrypt the system drive without your knowledge.
Unfortunately, when encryption is on by default, you’re not prompted to save the recovery key. You need to find it and save it before you need it.

Finding your BitLocker recovery key
You can find your BitLocker Recovery key:
- When you enable BitLocker yourself.
- In your Microsoft account online.
- By copying it from the “Manage BitLocker” interface.
- Via the “manage-bde” command-line tool.
Regardless of how you get it, save it somewhere safe.
Traditional BitLocker setup
If you explicitly turn on BitLocker full-disk encryption, at some point in the process, you’ll be encouraged to save the recovery key.
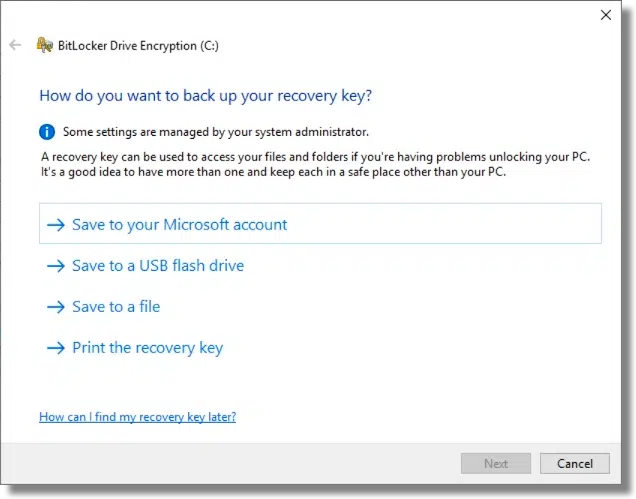
It’s important to take one or more of these options. The recovery key is your way back in should you lose the ability to sign in to Windows or should you ever need to move the drive to a different machine.
It’s important to keep the recovery key somewhere safe to avoid losing access to everything on that drive should something go wrong.
Great. But what if you didn’t take this path?
Help keep it going by becoming a Patron.
BitLocker on by default
There are a few ways that BitLocker could be enabled by default. Who knew?
That has several implications.
- You may be using BitLocker right now and not even realize it.
- Your hard drive is more protected than you thought, whether or not you think you need that extra protection.
- You probably didn’t walk through the process of turning on BitLocker, and thus weren’t prompted to save your recovery key.
The last point is the most concerning. Without a recovery key, you could lose everything on the drive. Let’s explore three ways to find and save it.
The quick way: using your Microsoft account
Visit this URL and sign in, if needed, to your account.
https://account.microsoft.com/devices/recoverykey
This page lists all the BitLocker keys associated with the Microsoft account used to set up your computer(s), or the account that was in use when BitLocker was turned on.
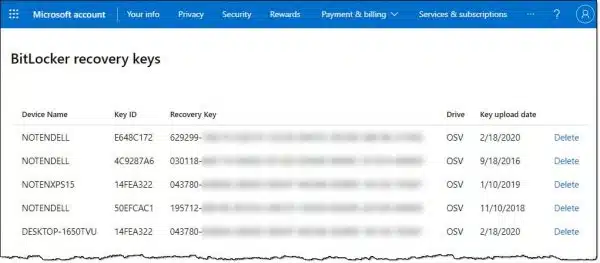
Above is the list shown in my personal Microsoft account. There are a couple of interesting things to note.
- One machine is listed multiple times. Each likely represents a reinstall of Windows and a re-creation of the BitLocker encryption. Technically, I probably don’t need the older ones, but there’s no reason not to leave them there.
- One machine’s name is incorrect. This implies that the key was saved before I changed the name of the machine from its auto-generated default to my NOTEN-based naming scheme.
If you see keys listed here, back up this information to an additional location for safety. Take a screenshot of the page and save the image in a safe place, for example.
This is great, particularly if you suddenly need a recovery key for a drive you didn’t realize BitLocker has encrypted.
My question, though, is how do I know if these recovery keys are up to date? Like my machine listed twice above, how do I know of if the keys listed are current, or that I haven’t somehow created a new key?
I don’t.
Windows File Explorer: back up your recovery key
Windows File Explorer is sure to have the current recovery key. Right-click on the drive and look at the options in the resulting pop-up.
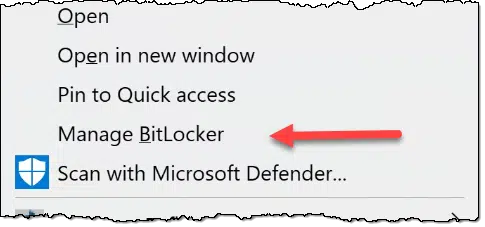
If the menu includes “Turn on BitLocker”, then BitLocker is not enabled for this drive. There’s nothing you need to do. (If the menu has no BitLocker option at all, then you probably have the Home version of Windows without explicit BitLocker support. See below.)
If, however, there’s an option to “Manage BitLocker”, click on that.
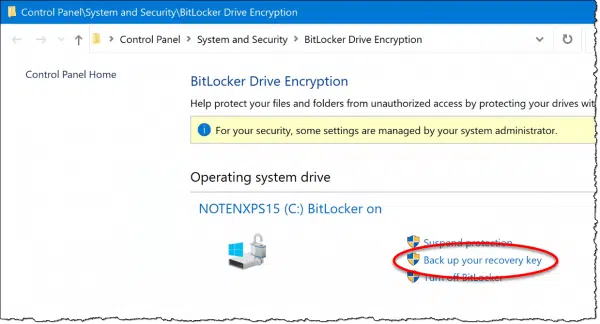
Click on Back up your recovery key, and you’ll have options to do exactly that. My suggestion is that you back up the key to both your Microsoft account (to be listed online, as shown above) and in some other form. Once you have that other form, store it somewhere safe where you can find it if needed.
The Command Prompt: Windows Home or Pro
Third option: if the drive is currently accessible, you can see the recovery key via the Windows Command Prompt. This is useful if you don’t use a Microsoft account, you’re running Home Edition, or if your machine isn’t shown in your account online.
In an administrative Command Prompt or PowerShell, run:
manage-bde -protectors -get C:
Replace “C:” with the drive letter of interest. If the drive is encrypted, it’ll display something like this:
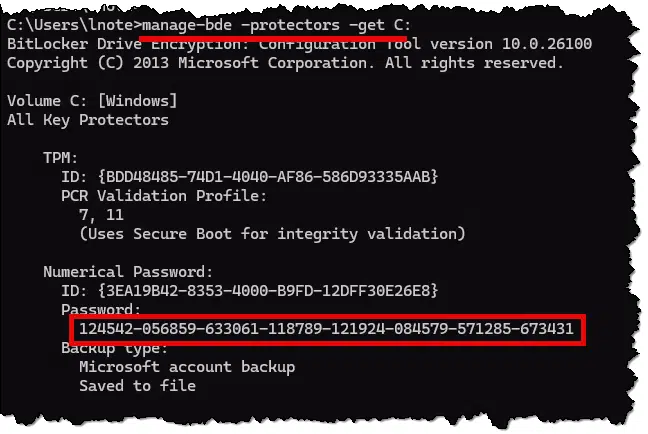
The “Password” shown under “Numerical Password” is your BitLocker recovery key. Save that somewhere. Again, you can take a screenshot and save the image, or you can select the text on the screen and copy/paste it into a simple Notepad document to be saved somewhere.
You may get the message, “No key protectors found.”
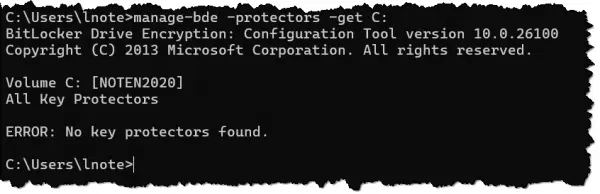
This means the drive is not BitLocker encrypted, so there’s no recovery key to save.
Do this
Whole-disk encryption is a valuable approach to securing data, particularly on laptops and other mobile devices. BitLocker is a fine solution for Windows, but it’s important to make sure you have those recovery keys available should you ever need them. Particularly since BitLocker might be turned on without your knowledge, it’s doubly important to check.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.



I’m just a bit horrified by the intricacies around Bitlocker. My status is Bitlocker is not turned on. I believe my PC is fully able to meet the hardware requirements of TPM >1.2 (2.0), UEFI, Secure Boot, PCR7, Device Encrption Support, etc. I admit that a check of SYSINFO shows that elevation must occur before the status of PCR7 and Device Encryption can be viewed but I’m not going down that road just to find out.
What is horrifying is that OEMs would cavalierly set Bitlocker on and, I suspect given the suspect state of the art of typical system set up instructions, perhaps not fully cover the ins/outs of Bitlocker Recovery Key. I just read elsewhere that a windows update can change the Bitlocker status and Recovery Key. How’s that for a kick in the pants!?
I’m not anti-encryption and use it for password systems and selected files/folders but who is minding the store for the unsuspecting user? I think computers are getting more and more “weasely” every day. My apologies to actual weasels.
Hi there!
I am looking for any informations that could help me recovered the Bitlocker key when the computer is already locked by bitlocker. None of our microsoft accounts has a recovery key and, of curse, as we didn’t know that we have this on the computer we never trying to save a recovery key.
What could be done?
Nothing that I’m aware of. That’s kind of the point of Bitlocker: to prevent unauthorized access. Hopefully you have an image backup of the computer. Failing that I know of no way in.
Hi Leo, Great video. I have a question. I’ve been doing almost exactly what you say i.e. saving my BitLocker keys to my Microsoft account. Recently I had to remove BitLocker for a backup program to work and set up BitLocker again. After windows re-install, the generated BitLocker key couldn’t be saved to my MS account even though I was logged in to my MS account and OneDrive was working. It just said something about not able to save to my MS account.
Later I tried again and the Manage Bit Locker app didn’t show “Save to Microsoft Account” anymore but got changed to “Save to your Azure AD Account”. Now I don’t even know what that is. All these machines are my home computers. They are not work computers.
I’ve since printed out the keys to PDF and kept the files.
Also I google Azure AD and tried to log in even though I don’t have an account. Maybe MS just changed the name of its services but no luck too.
What is going on and how can I fix this? By that I mean I want to have my BL keys saved to my MS account again. Thanks.
Daniel
I have heard a few rumors of issues on the Microsoft side, but I can’t say with any certainty exactly what’s going on.
My advice: DO NOT rely on (only) your Microsoft account to save the keys. Save them elsewhere, in your control, as well.
“Rumors on the Microsoft side” sounds deliberately vague. Can you provide keywords or links to articles so I can understand the source of the problem better? I have never simply relied on just my MS account for bitlocker keys. That’s a bad way to go. I just want them on my MS account as A source.
Sorry, I don’t have a source. It was something I came across a few weeks ago where people were seeing terminology relating to Azure accounts when all they really had was their plain old Microsoft accounts, and I didn’t save the link or anything. Azure may be the technology behind some of it, but it’s not supposed to be exposed that way. As I said, I believe it’s a transient issue that Microsoft should be fixing. If I’m wrong I expect we’ll be seeing more about it.
BTW, you should have a “notify when comment is replied” feature. I don’t see it. cheer.s
I looked into it some time ago, and it caused much more chaos than it was worth I’m afraid.
I just had this problem this morning for the first time with my Win 11 Dell, and for some reason it also forgot it’s WiFi connection, while all other WiFi devices were working fine.
Thanks so much for this! I was greeted a week ago by a BitLocker “Enter Recovery Key to get going again” screen and didn’t have any clue I had BitLocker on. After some panic, fortunately after a reboot I was fine. But after your video I found my recovery key – in both ways that you suggested – and printed it out. Keep up the good work!
This issue makes backing up one’s computer even more important. I use the paid version of Macrium Reflect and the backup drives do not have Bitlocker turned on. On occasion, I have had to restore my C:\ drive, which normally has Bitlocker turned on. Macrium Reflect will disable Bitlocker when restoring and when the image is restored I have to turn on Bitlocker again, which generates a new key that then gets saved to my Microsoft account, printed, and saved to a USB flash drive.
I would imagine that other backup programs can do the same.
If one gets locked out of a Bitlocker encrypted drive the only option is to format the drive to remove the encryption. This can also be done during the reinstalling Windows process.
Turn it off!!
If you don’t have the recipe for Coca-Cola on your hard drive, turn off bit-locker!
Again and again I’ve been asked by poor, innocent, clueless people to help them with their computer, and login difficulties are sometimes totally insurmountable when bit-locker rears it’s ugly head.
A system image backup backs the files up unencrypted. I would never go out of my house with an unencrypted laptop. Tell the people you help to perform regular system image backups and daily incremental backups.
When I set up my Windows 11 Home computer, I don’t recall any screen or pop up about BitLocker and the codes needed to regain access. Did I miss something? This article was very helpful and I saved the codes on an external drive and printed them out.
No, and that’s the problem. You can have bitlocker enabled and never even know it.
I was running Windows 10 Home Edition, OEM on a Lenovo all in one.
Now I know that Bitlocker is not available on Home Editions, (other encryptions are) but my computer one morning told me I was Bitlocked!
Fortunately, the keys were on my Microsoft account so I was able to gain access and recover.
However, every reboot I had to unlock it, and there was no way to turn it off because being Home Edition, it wasn’t supposed to be possible.
After much Googling, and people telling me I must be mistaken, I bought a Windows 10 Pro code online, upgraded to Pro, and thus gained access to “Turn off Bitlocker”.
Have you ever heard of this happening?
Much of the discussion was on internal drives. What about external drives (SSDs and older ones) as they are used for data storage with frequent storage of large files (i.e. Photoshop images)? What about drives used for backups?
In an unrelated question, with Bill Gates mostly out of the Microsoft picture, has industry and user confidence in the company improved? decreased? about the same? Company founders are usually noted for their innovative ideas and less for their marketing and business acumen.
Thanks,
External SSDs are poor backup media for several reasons.
1. They cost much more than magnetic hard drives
2. They have a shorter write cycle.
3. HDDs last longer when left unused.
4. SSDs are more vulnerable to overheating.
5. They are faster but I don’t see that as a major advantage for backups.
With respect to Bill: the company’s behavior I think has done more to harm its reputation than anything else. They’re still as innovative as they always were (a combo of true innovation and acquisition — not new at all), but the things they’re doing with it all is pissing more and more people off.
And many (MANY) people continue to blame Bill, even though he’s not involved directly any more and hasn’t been for some time.
I just woke up with a Bitlocker key request screen on my laptop, I wondered what it is about since I never came across it anywhere or heard of it only after popping up just like that.
I have tried to find it and done all the goggle search and unfortunately when I go into my Microsoft account on Devices its saying no Devices showing/registered something like that.
I’ve tried all options given to troubleshoot not working am only left to see if I can reset with another computer if that works .
Im completely locked out!
Frank S
I typed at a command prompt manage-bde etc as you said. Apparently my C drive is not encrypted. I put a linux iso on a ventoy usb and ran linux from the usb. But when I tried to access the notebook’s windows 11 C: drive it said “A passphrase is need to access encrypted data on Micro_2450…(512 Gb Disk). What ca I do?
I discovered today that bitlocker was turned on my reburbished laptop running Windows11 Home. I did not think it was. Your video was excellent and I was able to access and save the encryption key. Thank you so much for creating this video.
Dear Leo,
I wish this finds you well.
Happy New Year!
I got a broken notebook that the owner does not want to repair because it is not worthed. So I remove the NVME Sata SSD put it on a NVME enclosure and connected via USB on my Windows 11, here it comes the bitlocker warning. The owner of the notebook does not have any idea what a bitlocker means, I assume it was turned on by itself. Question:
How do we get the bitlocker key from an SSD that is not in the original computer but on another system instead?
I like your channel, the videos are very well done.
thank you
Prisco Fazio
You can format the drive, you won’t be able to crack it, otherwise Bitlocker would be useless. Even if you could crack it, it’s someone else’s data which would be useless to you, and even dangerous if they have illegal content.
You can try the technique outlined in the article you commented on: sign in to the Microsoft account and see if it’s been saved online.