While there’s no such thing as zero risk, you can take steps to minimize it.

In a previous article, I discussed the fundamental nature of our computer’s operating system: its absolute power to see and potentially expose anything we do. We frequently assume, often without actually thinking about it, that the OS is trustworthy.
That may or may not be true.
When it comes to the operating system, our options are limited. There’s really no choice: in order to use our device, we must use an operating system of some sort.
When it comes to the applications we install on our computers, we have both more choice and more risk.
Become a Patron of Ask Leo! and go ad-free!

Avoiding application risk
- Only install what you need.
- Install only reputable software from well-known sources.
- Download only from the vendor’s own download site or using their explicit instructions.
Every application adds direct risk
Every application you download and install on a device — be it your desktop or laptop computer, a tablet, or a smartphone — is an opportunity for your security and privacy to be compromised.
We regularly give applications much broader permissions to operate on our information than they need. In Windows, most programs can read any file whether they need to or not. For example, that desktop chess game you just downloaded has complete access to the financial spreadsheets stored elsewhere on your computer.
On the other end of the spectrum, some operating systems allow us to control permissions at a per-application level. For example, when installing an app on an Android-based device, you’ll often be presented with a list of things to which the new application requires access.
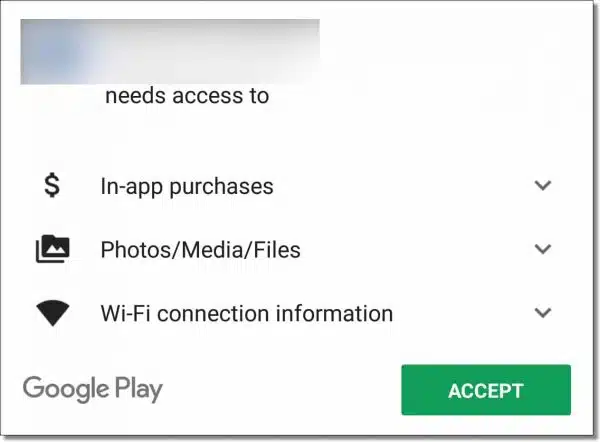
If we want the application at all, we must grant it all the permissions it requests. And that’s exactly what most people, including myself, do: zip through the list of permissions requested as if it was a license agreement, and accept it all.
Any application we install could be malicious. It could be explicitly malicious — meaning malware — or it could be less obviously malicious, such as sharing more information with third parties than we realize, thus violating our assumptions of privacy.
As we’ll see in a moment, as long as we take appropriate care, we can be relatively safe.
Every application adds indirect risk
Even the best-intentioned application includes risk, even if indirectly.
The program could have bugs. It could have errors or omissions that could be leveraged by other malicious software. It could “leak” our information unintentionally in ways third parties can intercept and collect.
Again, none of these risks are included purposefully, but rather as a side effect of oversight, poor design, poor coding, or other unintentional accidents.
All software has bugs. Thus, all software comes with some risk that those bugs, once discovered, could be used by others for unintended actions.
It all comes back to trust
You and I can’t be expected to understand all the details and nuances of software design and marketing. It’s too complex and ever-changing.
Instead, we rely on third parties. Or more correctly, we rely on our trust of third parties to either do the right thing or act as a resource to let us know when the right thing isn’t happening.
This is why I so strongly warn against using download sites. The third parties involved — the download sites themselves — have a poor track record of providing software that can be trusted. Instead, I recommend you locate the original vendor of the software you’re looking for and download directly from the source.
Assuming, of course, you trust them.
I discuss ways of developing and evaluating trust in What Does It Mean for a Source to be “Reputable”? The advice there applies equally here. When it comes to the software you install on your machine — any software — you must weigh the benefits against the risks and make sure you trust the source.
Rule of thumb: don’t install what you don’t need
The most secure software of all is the software that isn’t on your machine. If it’s not there, it can’t harm you.
I’m sure you know someone who constantly downloads and installs software on their machine. Be it a bevy of anti-malware tools to the latest games, their machine eventually becomes unstable — or worse, their online accounts get hacked as a result of malware accompanying all those downloads.
All for things they didn’t really need.
Don’t be that person. 
Think carefully before installing any software on your computer or other device. Even the most trustworthy and reputable software comes with side effects of some sort, and in the worst case, as we’ve seen, there’s a risk of more malicious intent as well.
Make sure you need it. Make sure you trust the author. Make sure you get it from a source you trust.
And when in doubt, don’t install it. You’re safer that way.
Do this
All this sounds pretty daunting and perhaps even a little overwhelming. You might be wondering if anything’s ever safe.
The good news is that for the most part, the software you get from reputable sources is generally not malicious and is generally well behaved. There are bad actors out there, of course, but keeping these basic rules of thumb in mind will generally keep you safe.
- Only install what you need.
- Install only reputable software from well-known sources.
- Download only from the vendor’s own download site or using their explicit instructions.
If you’re at all concerned about security and privacy — and you should be — it’s important to keep these rules in mind.
You’ll have a much safer and more confident experience.
Speaking of confidence, subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.





I have a question which isen’t directly connected to this topic
How could I send my question?
Here’s a link to ask a question. Please use the search box on any Ask Leo! page to search for your answer first.
Use the search function first to see if it’s already answered here. There are over four thousand answers already posted.
I rely on people I trust like yourself, Bob Rankin, and a few others to recommend software that might be of use to me. I very rarely just search for software on the internet, precisely because of the potential problems that you identify. And I also accept that very occasionally even you might recommend something problematic – but that hasn’t happened yet, probably because of the care that you take before recommending anything!!
Leo – keep up the good work, and thanks.
When a programmer updates because of a bug, he rewrites a small part of the program, often inducing other problems.
Great article. Hope everyone follows your advise.
Dave
as it is closed have to put here
http://ask-leo.com/what_difference_does_multipleoverwrite_delete_really_make.html
Bleachbit says one pass as good as 50
https://www.bleachbit.org/forum/bbs-simple-overwrite-not-explained-anywhere-why-why-no-standardised-erasing-patterns-ensure-tr
you must think people have nothing to do only go around in circles looking to ask. google is easier
Commenting has been terminated on the older format articles which are on ask-leo.com. That is due to the way comments are being handled through Word Press which doesn’t support comments from the older articles. Gradually, relevant articles are being converted to the new format and comments are being reopened for those articles.
The enjoyment I get from having a PC, is downloading and trying out all sorts of new (to me) programs. I always have up-to-date backups. I think Leo may have mentioned backups a couple times. 😉
Sometimes, at the senior center, someone will ask me questions I can’t answer right away, so I make notes, go home and try the program they had questions about, and come back with answers. I keep two Windows machines, because most of the people in class use Windows.
My point is, being careful is great, but being afraid to install anything detracts from your ability to use your PC and the internet.
I know that’s not what Leo is saying, but I also know that that is how some of the people in class will take it. …And, of course, most people in class read AskLeo regularly. 🙂
I had thought ninite was a safe website to download from. Have used it for years with no problems. Thanks for another excellent article. In the interest of economy I have allowed a sentence ending in a preposition. My apologies.
Chris.
Ninite isn’t a website, per se, but rather a tool you run on your PC. If I understand correctly it, in turn, downloads from the various original manufacturer’s sites.
Unfortunately, not installing what you don’t need is not feasible for an advanced user. I call an advanced user one who is always trying to learn, to discover new ways to do things, and therefore to try new software.
How can you do this, if you don’t leave new software installed ? If you find, right after using it once, that it’s crap, then of course it’s easy to uninstall it right away. (I use Revo Uninstaller, and always monitor installs.)
But that’s not the way it works with most programs. You need to use them over a period of time to really find out if you like them. Unless you’re systematically running tests, as opposed to using the program when you happen to need it, you’ll necessarily forget most of them.
Yes, downloading software can be risky. The problem is you won’t know if you need or can use a software until you install it and test it. Many applications over promise and under deliver. Often you cannot be sure if you’re downloading a trial version or a fully functional application. Going to “reputable” websites may not seem safer either because if you go to a page with a download there may be 10 big buttons saying “Download”. These are injected ads and the reputable site may not have control over them. Try to download the offline or zip version of the application, or at least the full application executable, as opposed to an installation stub. Typically a stub will be a very small file, whereas a full application will be much larger. No matter what you download, scan it with a couple of malware scanners. Best bet is Malwarebytes. If you get a zip or exe file you can further examine it using 7Zip to see what’s inside without going through an installation process. If you’re still not sure about the software, then install it within a sandbox application (e.g. Sandboxie).
I use both Windows and GNU/Linux. I trust Microsoft enough (so far) to use their OS. I can say the same, albeit for different reasons about the developers of the two GNU Linux distributions I use. Since Windows and GNU/Linux are different paradigms (OSs), I’ll start with Windows:
In Windows, following installation, I remove anything I don’t want that’s possible starting with Microsoft ToDo and a few others because I have no use for them. Next I add the apps/services I want such as LibreOffice and Core-temp, a utility that displays the CPU temperature in the system tray. I also install a few games from the Microsoft Store.
I have a collection of ‘routines’ I perform on a weekly, monthly, semi-annual, and annual basis. One of my monthly routines is to go over my list of installed apps (yes, I keep a list, and when I install a new app, I update my list to include it) to determine if I still need/want them. If I no longer use an app, this is when I remove it from my computer and my list. This way, I only keep the software I use and remove what I don’t.
In my GNU/Linux distributions, I use a somewhat similar approach, but I have very few (if any) apps/services installed that are not included with the distribution or available for installation from its repositories. Following installation of the distribution, I go over the installed apps in the software manager to remove anything I don’t want/need and install anything I do. I’ve found a OneDrive client on GitHub. Initially, I had to build and install it from source (very bothersome to update) but recently I’m finding it in my two chosen distributions repositories. That’s a good thing because now the OneDrive client is updated along with all the other software I have installed in those distributions. I don’t have to keep a list of installed software because the software manager does that for me (it has an ‘Installed’ category). The software manager also regularly checks for updates for all the apps installed from the distribution’s repositories. The list of available software for each of both distributions is extensive enough that I usually have no need to go elsewhere.
In both OSs I keep only the software I want/need, and review what’s installed monthly to keep my computer as lean, mean, and stable as possible. When I must/want to download any software from the Internet for any reason (including experimentation) in either OS, I vet it as carefully as I can. I do a few Internet searches for “[app-name] sucks” and a few similar searches to see if there are any posts indicating malware or other issues. In Windows, I scan the download for malware using Microsoft Defender. In GNU/Linux, I install the software in a VM (after creating a snapshot for potential restoration) of my OS to check it out before installing it on bare metal.
These are a few of the things I do to keep my computers as safe from malware and any other threats as possible. No software threat mitigation routine is perfect, but one that is well though out and regularly executed is much better than nothing at all. I hope this helps others.
My2Cents,
Ernie