Why I harp, harass, cajole, and harp some more.

Some years ago I posted this on Facebook:
Just had to break the news to a friend that the photos on the hard drive that failed — the contents of which we WERE able to recover, thanks to some hard disk utilities — turned out to be encrypted by ransomware (CryptoWall), and we had no way to decrypt them. And no, they didn’t have a recent backup. (And yes, there were some VERY important photos on there. I’m hoping they’ll recover some at least from friends and family with whom they shared ’em.)
This is why, folks. This is why I harp and harp and harp on backing up. Seriously. Sh*t happens. Sometimes it’s benign, and sometimes it’s downright heartbreaking. PLEASE back up.
I want to share what happened and explain how this could have been close to a non-event.
Become a Patron of Ask Leo! and go ad-free!

A story of data loss
After repairing a friend’s hard disk failure, I discovered files on it were encrypted by CryptoWall ransomware. Despite recovering the drive contents, decryption was impossible, and there were no backups. Regular backups are critical to avoid data loss and heartache.
Hard drive failure
I got a call from a friend standing at a local office supply store’s computer service desk. He was a tad befuddled at the terms and dollar amounts the technician was throwing at him.
- The hard drive had had some kind of physical failure — probably a bad sector or area.
- The technicians had installed a replacement hard drive into my friend’s computer.
- The technicians were unable to back up the faulty drive with their normal tools.
- The faulty drive contained important information my friend wanted to recover.
- The next step for this particular computer service organization was to send it out to data recovery; costs were quoted from $200 to $1600.
My friend’s question was simple: did he need this, or was he being taken for a ride? He put the technician on the phone.
The bottom line was that, no, he probably wasn’t being taken for a ride, and that yes, the situation was serious. They’d just gone beyond what the in-store technician could do; hence the need to send it out.
He brought the machine to me instead.
Hard-drive recovery
At the time, my go-to tool of choice for bad sectors on a hard drive was SpinRite, so that’s where I started. I hooked the faulty drive up to one of my spare systems and let it work.
Unfortunately, SpinRite hasn’t been updated in years — which is really sad, as it’s a great tool when it works. It didn’t work for me in this case. Be it the BIOS on the machine, the SATA interface, or the sheer size of the one-terabyte drive, SpinRite would only go so far before crashing.
I Googled SpinRite alternatives, and while there weren’t any, I came up with something close: MHDD.
MHDD’s basic difference from SpinRite is that when it finds a bad sector, it “remaps” it, taking it out of use and replacing it with one of the spare sectors that hard disks have for exactly this purpose. Note, however, that it doesn’t recover the data in that bad sector. SpinRite will first work long and hard, if need be, to recover the data in that sector, often recovering and repairing it, so no remap is needed.
I let MHDD do its thing, after which I could use Macrium Reflect to take a complete image backup of the faulty drive and restore that image to the replacement drive in my friend’s machine.
All seemed well, and I sent the machine home.
Later that day, I got an email. My friend wanted to know why he couldn’t open his pictures.
Cryptowall
When he tried to open an image, my friend got an error message.
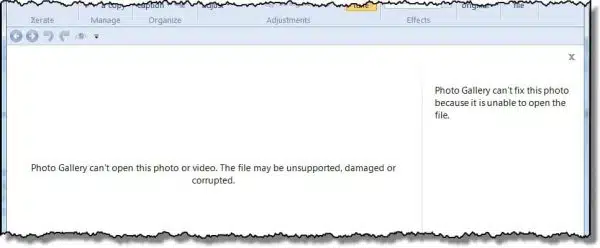
Since I’d kept a copy of the backup image “just in case”,1 I restored it to a hastily created partition on one of my own machines and started looking around.
What I found was not pretty.
The images weren’t images anymore. They had the same names and the “.jpg” extension, but their contents didn’t look like jpg image data at all. In fact, the contents looked more like random data. Almost as if the files had been… encrypted.
And then I found this:
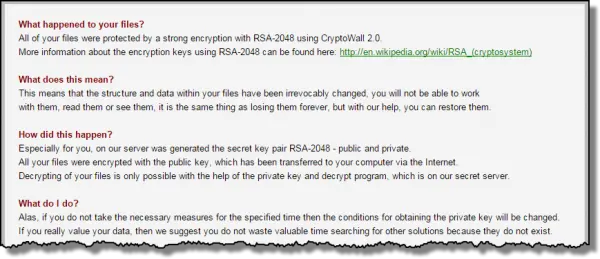
At some point, this machine had become infected with the CryptoWall ransomware: software that encrypts all your important files and then displays a ransom note instructing you how to pay to get the decryption key to access your files again.
My friend had never seen that ransom note. That means either the encryption process hadn’t been completed when he’d last turned off the machine, or the virus had attached itself to the machine while at the service center. (Timestamps on the files showed that the malware had arrived prior to the service center touching the machine.)
Either way:
- The encryption appeared to be unrelated to the hard disk failure. (It’s possible that the encryption process caused the hard disk to stumble into a previously unused bad sector, but there was no real direct cause and effect at play here.)
- The hard disk recovery was a success, but the prognosis for this new situation was even worse.
Recovery efforts
BleepingComputer.com has a good page on CryptoWall, including common approaches to recovery. Unfortunately, none of them worked2.
- Restore from a backup: There was no recent backup. Some files were available on a months-old backup, but that didn’t help with recently created, updated (or encrypted) files.
- File Recovery Software: The process of recovering the original drive to another drive invalidated anything that file recovery tools could use. (Though the original “failed” drive remains unaltered in my basement and may be used as a last resort at some point.)
- Shadow Volume Copies: The process of recovering the drive to the new one invalidated anything that file recovery tools might use. The original drive may have the files, but the chances are slim since CryptoWall intentionally deletes them.
- Restore DropBox Folders: Dropbox wasn’t being used.
In short, and as of this writing and update, we were SOL: severely out of luck. The files that were encrypted remain encrypted with little chance of direct recovery.
Which leads to the moral of this story.
What could have been
Bad stuff happens. It just does. You cannot avoid it all the time.
Hard disks die without notice or warning. In fact, they can die so suddenly and so completely that all data stored on them can be instantly and irretrievably lost forever. Nothing malicious is required — they just die. Most failures aren’t instantaneous or irretrievable, but they can be.
And, of course, malware happens. It shouldn’t. In a perfect world, we’d never invite it in, and if we did, our perfect anti-malware tools would protect us 100% of the time. Neither the world, our computer, our security software, nor even ourselves are perfect. Stuff happens, as it did to my friend in a double dose: ransomware and a failed hard drive.
You can’t avoid it.
But you can prepare for it.
This makes situations like my friend’s so frustrating. Here’s what could have been:
- Hard disk dies.
- Replace it.
- Restore the previous day’s image backup.
- Get on with your life.
And/or:
- Machine is infected with malware; all files on it are encrypted and a ransom is demanded.
- Restore the machine from the previous day’s backup.3
- Get on with your life.
- Learn from the experience: don’t repeat whatever caused the infection.
THIS IS WHY I harp and harp and harp on backing up.
It hurts me to see data loss — particularly important data like irreplaceable family photos, as was the case here.
Do this
If it’s in only one place, it’s not backed up. If that’s true for anything you consider even the slightest bit important, start backing up, please.
I don’t care how you do it or what tools you use (as long as they work, of course); just make sure you’re doing it.
Podcast audio
Footnotes & References
1: I’m kinda paranoid that way. 🙂
2: Still the case over 10 years later.
3: There’s a debate about whether the external drive should remain connected in case backups get encrypted. That’s a red herring, in my opinion. Having it connected and backups automated is significantly more important. There are several solutions. I discuss it here: Should I Disconnect My Backup Drive When I’m Not Backing Up?





Thanks for the article. Wow, as if guarding against the possibility of HDD hardware failure wasn’t worrisome enough. Is CryptoPrevent enough defense against these CryptoWall extortion rackets (apart from making backups, I mean)?
Here’s an article on Cryptoprevent. You’ll find a lively discussion on the topic!
https://askleo.com/why-havent-you-mentioned-cryptoprevent/
CryptoPrevent protects against CryptoLocker. The problem is, you’d still have to worry about any similar ransomware or malware which CryptoPrevent doesn’t prevent. I don’t know if it helps against CryptoWall or not.
Why haven’t you mentioned CryptoPrevent?
My understanding is that it does help against CryptoWall – BleepingComputer mentions it specifically.
One thing I don’t think you mentioned is that shouldn’t you disconnect the backup drive after taking the backup? Isn’t malware smart enough to encrypt the backup drive as well as the primary drive if it is connected?
Leo has a few article on that:
https://askleo.com/is-it-safe-to-leave-my-external-backup-drive-connected/
https://askleo.com/will-malware-infect-the-backups-on-my-connected-backup-drives-as-well/
Leo wrote an article on that. Bottom line: He leaves his plugged in.
Is it safe to leave my external backup drive connected?
Leo is the expert no doubt, but with these Crypto situations people report that it also targeted their external drives. From everything I’ve read you want to make a backup and disconnect that drive so it doesn’t become a casualty. Yes we should all be doing things so it never happens in the first place (safe surfing is #1) but in today’s world that’s not always possible as sometimes even experienced users get nailed… drive by infections, injection, a app that you may not have updated being exploited, etc.
Sorry to hear about your friend’s hard disk issue. Fortunately, you were able to spare him the data recovery expense for repairing the bad sectors. As for the Cryptolocker/Cryptowall, he basically has two options: 1) Pay the ransom or 2) Wait it out. The servers for the first variant of Cryptolocker were eventually seized and the corresponding private keys (needed to decrypt) were publicly released for free. If I were your friend, I would keep the image you created until I was able to recover the encrypted data. Good luck.
Actually I’ve kept that image (and the original drive, actually). I’m hoping that, as you say, eventually the crypto keys will be discovered.
And the only way this will happen is if someone can infiltrate the place where these keys are stored on the bad guys end no? Short of that or a miracle people will be waiting a very long time.
Is it possible that the MHDD tool you downloaded and run on the hard drive was the delivery path for cryptowall?
I don’t believe so.
Try: https://www.decryptcryptolocker.com :
“FireEye and Fox-IT have partnered to provide free keys designed to unlock systems infected by CryptoLocker”.
All you have to do is upload an affected file and “This portal will then email you a master decryption key along with a download link to our recovery program that can be used together with the master decryption key to repair all encrypted files on your system”.
Hope you get your photos back!
That’s for CryptoLocker, not CryptoWall … yet.
I Have since loaded and continue to use a cryptoware blocking program that was distributed as free ware by foolishit.
What about HDD Regenerator? I’ve seen mention of it’s use before. Do you have any experience with it?
I’m not familiar with it.
I’ve taken Leo’s warnings and backup advice to heart. Using Macrium Reflect, I make a full image backup monthly and daily image backups. Macrium Reflect has a feature called Image Guard which only allows opening or viewing backup files through Macrium Reflect. I can’t use another program to do so.
I use OneDrive and have my Documents, Music, and Pictures folders located in the OneDrive folder. OneDrive is set to keep copies of my files on my hard drive (Files on Demand is turned off) as well as on the Microsoft servers. When I started using Cryptomator to protect sensitive files in my OneDrive folder, I found out that OneDrive will raise alarms about the encryption process taking place and offers to help restore the files.
Between Image Guard and OneDrive, I believe I’m covered in the event of a ransomware attack. I take extra steps to make an image backup of our computers on hard drives separate from the regular backup drives and copy my files to other external drives each month. All of those drives are kept in a safe location.
I hope to not ever find myself in the situation Leo described and believe I won’t be with the actions I’ve taken. It takes a little time and effort to set everything up initially, but little time to keep it up. If a hard drive fails, it can be easily replaced.
Correction on how backup: Monthly full image and daily incremental backups.
Image Guard doesn’t allow only opening or viewing backup files through Macrium Reflect. Macrium Reflect and all system image backup do that because they are saved in a proprietary format. Image Guard does something much more secure. It allows only Macrium Reflect to access those files, so they can’t be deleted by any program other than Macrium Reflect. By not allowing deletion, Ransomware can’t encrypt the backup and delete the original.
Doesn’t chkdsk /r work similarly to MHDD? It tries to recover the content of a sector and remaps another unused sector to replace the bad sector. Or does MHDD do more?
Can ramsomware corrupt OneDrive files?
Yes. This is why you should also be backing up. (And depending on your plan, OneDrive has a recover-from-ransomware feature).
Yes and no. It synchronizes the encrypted files, but it backs up the original files before replacing them with the encrypted ones in its Recycle Bin. I wouldn’t count on it working perfectly, so you should use a system image backup, preferably using Macrium Reflect with Image Guard which prevents your backup files from being altered or deleted.
I currently use Macrium Reflect to create, and keep four weekly full system images, and six differential images per week (on my desktop), keeping twenty-four (six for each of the four full system images), so I keep four image sets, but that may change when I see what MSFT decides to do with the 2024 or 2025 major Windows 11 updates.
If they do as I fear/suspect they will, I’ll be dropping Windows (and Macrium Reflect) altogether, and become a GNU/Linux-only computer user. As part of my preparation for that eventuality, I’ve found a GUI front end for Clonezilla, named Rescuezilla. It’s a live mini-GNU/Linux distribution with the Rescuezilla software launched by default at boot time. I’m using it to generate a full system image of my main system drive on my primary laptop PC monthly. My external disk drive has enough storage space to store about nine or ten full system images of my entire 1TB system drive (contains both Windows 11, and Garuda KDE-Lite GNU/Linux).
In my GNU/Linux installation, I’m syncing my ~/Documents, and ~/Pictures directories to MEGA.io, using their desktop utility (MEGAsync). This way, any time a file on my system changes, it is immediately synced to the cloud.
I am also experimenting with Clonezilla, and rsync. Additionally, I’m still looking for a good disk imaging utility I can use as I do Macrium Reflect.
Ernie (Oldster)