Just the backbone of securing the internet, that’s all.
In recent months, I’ve published a few articles on both new and old technologies that rely on something called public key cryptography or public key encryption.
Honestly, you don’t need to understand public key cryptography other than to realize it’s a key component of keeping you safe online.
On the other hand, since it is so ubiquitous and the phrase comes up more and more often, it might be interesting to understand how it works and how it keeps you safe as you visit your bank, download your email, or even just view this webpage.
Let’s dive into what public key cryptography is, why it’s useful, and how it’s being used.

Public key cryptography
Public key (or asymmetric) cryptography uses a pair of encryption keys. Data encrypted by one can only be decrypted by the other. This enables everything from identity verification to secure data transfer. Public key cryptography is the basis for security online.
This is a conceptual overview. Many details have been simplified, glossed over, or even tweaked ever so slightly in order to make the concepts somewhat understandable. Encryption and its use is exceptionally complex, and the details are well beyond anything it makes sense for most of us to learn.1
Magical mathematics
The single most important concept behind public key cryptography, often also referred to as asymmetric cryptography, is this.
A complex mathematical formula is used to create two (very) large numbers with the following relationship:
-
- You cannot calculate one from the other.
- Anything you encrypt using one can only be decrypted using the other.
That last point is key.
You’re probably used to traditional encryption, where you encrypt something using a password and you use that same password to decrypt it. Tools like VeraCrypt, Zip, and even the encryption built into “password protecting” a document work this way. It’s called symmetrical encryption because the same password or encryption key is used for both encryption and decryption.
Asymmetric means you use a different encryption key to encrypt than you to do decrypt. Symmetric encryption, on the other hand, uses the same password to encrypt and to decrypt — such as a password-protected document or zip file.
In this article, we’re looking at the first. It’s beautiful digital and mathematical magic, as far as I’m concerned.
Help keep it going by becoming a Patron.
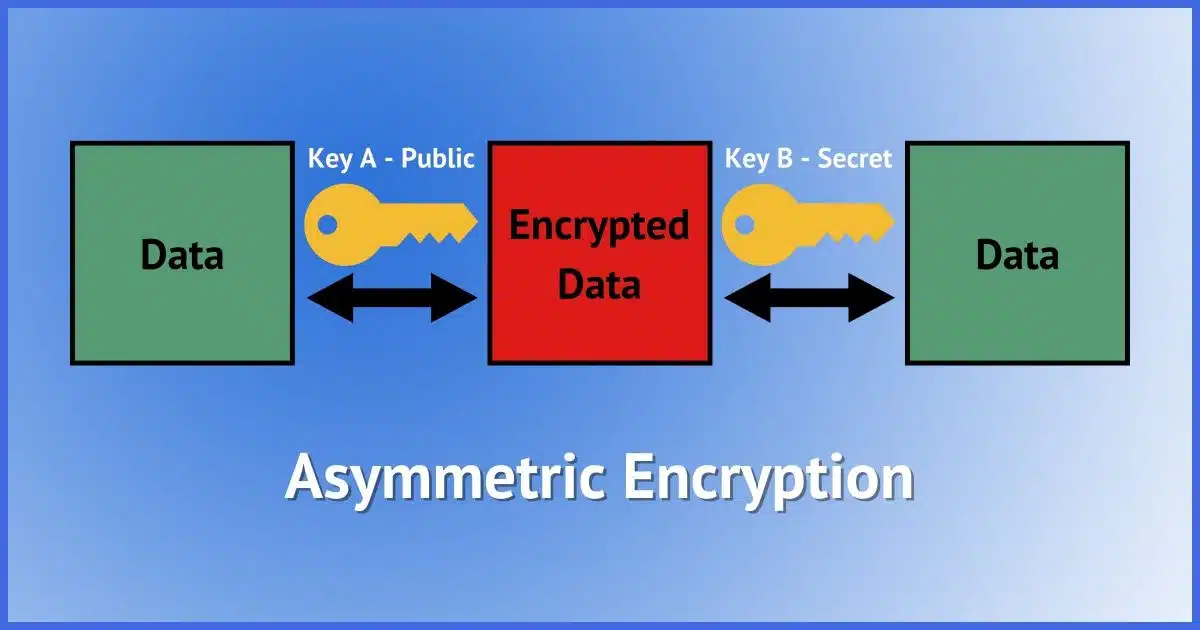
Asymmetric encryption
The steps for using asymmetric encryption are:
- Using a special program, generate two large numbers called a key pair. I’ll call them keys A and B.
- Use one of them — key A — to encrypt some data.
- Use the other — key B, in this case — to decrypt the data.
Keys A and B are two completely different numbers. The “magic” is that they can both decrypt data that was encrypted using the other; in fact, they can only decrypt data encrypted by the other.
They can’t even decrypt data they themselves encrypted, meaning key A cannot be used to decrypt data encrypted using key A. Only key B can do that — and vice versa.
So, why is this so important and useful?
It’s all in how you use those two keys.
Public and private
So far, I’ve not talked about the “public” part of public key cryptography. Everything discussed so far as been generic, treating keys A and B the same.
Let’s make one of the keys public, meaning literally anyone can see it, and keep the other a secret. This is done in several ways, depending on how you intend to use the keys. For example there are public key servers for certain encryption tools that you might upload your own public key to. For websites there are the so-called “root certificates” present in the operating system that are part of the mechanism that make website public keys public.
We’ll call one of the keys — it doesn’t matter which one — the secret key and the other the public key.
Two really interesting things are now possible:
- Anyone can encrypt something using the public key that only the matching secret key can decrypt.
- This is used for secure data transfer.
- Anyone can verify that something was encrypted by a specific secret key if they’re able to decrypt it using the matching public key.
- This is used for identity verification.
Public key cryptography and secure data transfer
Let’s say you want to send me a document full of sensitive information. It’s so sensitive that you want to ensure no one but me can see what’s in the document, so you decide to encrypt it.
You would (with the appropriate tools, perhaps GPG or Gnu Privacy Guard):
- Locate the public key I’ve published that anyone can use.
- Encrypt your data using my public key.
- Send me the encrypted result.
You can send me that data via any method you like, from email to passenger pigeon. It doesn’t matter if the way you get it to me is secure or not — the data is securely encrypted.
Only I can decrypt it because only I have the secret key that goes along with the public key I made available for anyone to use. Only my secret key can be used to decrypt something encrypted using my public key.
So that’s how public key encryption can be used for secure data transfer. Let’s look at our second use case: identity verification.
Public key cryptography and identity verification
Let’s say I’ve published a document, but because of its sensitive content you need to be sure it came from me and not someone pretending to be me. (A signed contract, perhaps.)
Here’s how public key cryptography makes that possible.
- I encrypt the document2 using my secret key. Only I have this key.
- I publish and make the encrypted document public.
- Anyone can use my public key to decrypt the document.
If decryption using my public key works, that means only I could have encrypted the document with my secret key. That document must have come from me.
Putting the ‘s’ in https
So far it’s all been conceptual and theoretical. While this will remain conceptual, let’s look at how public key cryptography makes https connections — like the connection you’re likely using right now to view this article online — possible.
Https does two things:
- Verifies the identity of the site we’re connecting to
- Encrypts the data we send and receive
Sound familiar?
When a website is set up to support secure connections using https, part of the process is to purchase, procure, or create a pair of encryption keys. One is made public (via official channels, registering it as the public key for this domain),3 and the other is kept secret on the web server.
When a browser connects to that website, it can encrypt something using the public key, and the server’s ability to decrypt that message confirms that the server must be who it says it is. For example, my browser might encrypt something — a random number will do — using askleo.com’s public key, send it to the server, and then ask for the decrypted result. If the server can show it was able to decrypt it by sending back that random number, it must be because it has the matching private key. This, then, means the server is the official askleo.com server.
Once authenticity has been confirmed (in the blink of an eye, it’s so fast), the browser and website can start exchanging encrypted data.4
Public key cryptography via https enables vast amounts of secure communication on the internet. I daresay much of what we take for granted today — your banking, online shopping, secure government access, healthcare and more — wouldn’t be possible without it.
Replacing something you know
To explain one final way public key authentication might be used, consider two-factor authentication. Imagine if you had two-factor authentication set up on an account and you only needed your second factor by itself, making it the single factor.
Traditional authentication means you need:
- Something you know: a password.
Two-factor authentication increases the requirements to:
- Something you know: a password.
- Something you have: a two-factor device, email account, phone, etc.
Public key authentication feels like a step in the other direction, as it changes the requirements to:
- Something you have: a secret key.
It remains secure because there’s nothing to remember and nothing that can be intercepted or stolen, as both passwords and some two-factor methods can be.
Public key authentication can be used to confirm the identity of the site you’re visiting and will be part of confirming your own identity to that site.
Do this
Be aware of this technology and how it’s being used to keep you safe and secure online.
And perhaps appreciate the mathematical magic.
I try to demystify things like this in my Confident Computing newsletter. Less frustration and more confidence, solutions, answers, and tips in your inbox every week. Join us today!
Podcast audio
Footnotes & References
1: Pedants need not point out errors unless I’ve grossly misrepresented something, and even there it might not be worth it if it a correction doesn’t improve general understanding.
2: In reality, there are other techniques that would not involve encrypting the entire document, but they all come back to using public key cryptography.
3: It’s more complex than this, of course. One aspect is that the root certificate infrastructure confirms that the public key is legitimate.
4: This involves a somewhat complicated bootstrapping process that lets the two sides encrypt in higher speed using a magically agreed upon random symmetric key.




Very interesting.
Next question:
1) How do you design the crypto-software?
2) How do you prevent your private key from being stolen?
3) If your private key is stolen, can it then be used by the thief?
1) You don’t design the software. You rely on the experts to do that.
2) you store it somewhere safe and keep your machine secure. Specifics will vary depending on the user. Mine are in CryptoMator encrypted folders.
3) yes. (There’s often a revokation mechanism built in, but it’s not something that would prevent use, more a notification that you’re a revoked key)