I was wrong. Let’s fix that.

There’s no shortage of confusion around passkeys. I recently updated my article What Is a Passkey? to try to further clarify what they are and how they work.
Originally, I got one aspect of passkeys wrong: the confusion between passkeys and hardware keys (like the Yubico YubiKey). I thought they were completely unrelated.
Not necessarily so.

Hardware keys and passkeys
Passkeys are secret codes used to sign into websites your device keeps safe and only uses after you unlock it. Some hardware keys, like certain YubiKeys, can also store passkeys if they’re FIDO2-ready. Hardware keys can act as two-factor authentication, portable passkeys, or both. (Older hardware keys work only for two-factor sign-ins.)
Passkeys on your device
What Is a Passkey? has a more complete overview, but the issue relevant to what we’ll discuss here is that a passkey is a cryptographic secret — a blob of data — stored securely on your device. When you need to use that key — say to authenticate with a website when signing in — you’ll likely be asked to authorize the device (by entering a PIN, providing your face or fingerprint, or something else specific to that device) to fetch and use that secret key.
For example, when you sign into a site using passkeys, on Windows you might need to provide your Windows Hello PIN. On your phone, you might need to unlock it with your fingerprint, even if it’s already unlocked.
The key concept here is that your secret key is stored by your device securely, and you need to authenticate with the device to allow the key to be used.
Help keep it going by becoming a Patron.
Hardware keys
To date, we’ve talked about hardware keys like the YubiKey only in the context of two-factor authentication, their original and perhaps most common use.
When you set up two-factor using a hardware key, you establish a cryptographic relationship between that key and the account you’re setting it up with. The hardware key contains a pre-programmed, unique cryptographic key. Once set up, that, along with some magical math and synchronization, means that key, and only that key, will be recognized as your authorized second factor.
Typically, when you sign in for the first time on a new machine1, you’ll enter your username and password, and then be prompted to prove you have the hardware key by inserting it into a USB port. Its cryptographic code is confirmed to be correct, and the second factor is confirmed.
That’s one use of hardware keys.
Turns out there’s another I was unaware of.
Hardware keys as passkeys
Some — but not all — hardware keys can be used as passkeys as well.
As I mentioned above, a passkey is a secret key that is stored somewhere secure, typically on your machine. It turns out it can also be stored on a FIDO2-certified hardware key. FIDO2-certified is just a fancy way to say that the device has the functionality required to do this securely.
Not all hardware keys are FIDO2-certified.
- Those that are not can only be used as 2FA keys.
- Those that are can be used as 2FA keys and as passkeys.
Hardware keys that can act as passkeys typically have limited storage. Per YubiCo: “Currently, YubiKeys can store a maximum of 25 passkeys.” (This applies to their series 5 FIDO2-certified keys.)
The advantage of using a hardware key as your passkey is that you can use your key anywhere to sign in to the account(s) associated with it. It’s considered the most secure form of passkey storage. It’s also the most inconvenient because, unlike other passkey storage techniques, the key must be physically present for use.
Setting up hardware keys as passkeys
I’m not going to dive into the process in detail because honestly, hardware keys are overkill for most folks, and the process can be confusing. I also expect (or, rather, hope) that the setup process will be streamlined at some point to make it easier and clearer.
As just one example, though, after asking Google to Add a Passkey to my account, I’m faced with this dialog.
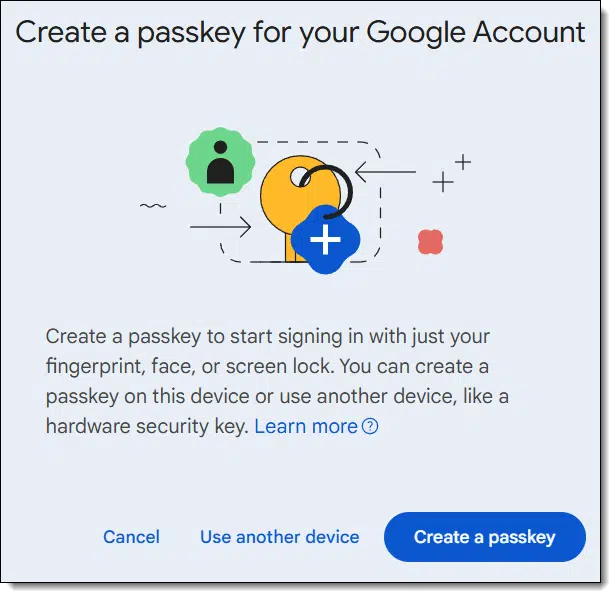
“Create a passkey” will create a passkey on Windows that is stored in Windows secure credential storage2. Any hardware key will be ignored.
If I want to use my YubiKey instead, I need to choose “Use another device”. This will bring up dialogs relating to inserting and setting up my particular YubiKey as a passkey.
Yubico Authenticator
The most popular hardware keys are made by Yubico. They have a nifty app you can run in Windows to examine and manage your YubiKey: the Yubico Authenticator.
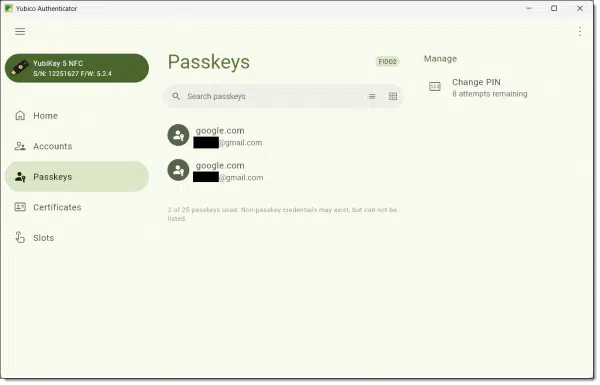
In this example, I have my FIDO2-compliant YubiKey inserted. You can see that it currently has two Passkeys, one for each of two different Gmail accounts.
Even though the keys are listed and you can view some data about them, there is no way to export or view the actual secret key.
Note also the notification: “2 of 25 passkeys used.”
If I remove this YubiKey and insert my older, non-FIDO2 compliant key, passkeys are nowhere to be seen.
Protecting your key
Naturally, it’s important to protect your hardware key from loss and theft, but neither is quite the disaster you might think it would be.
Theft: the thief would need to know everything else required to sign in to your account and know what account the passkey applies to.
When used as a passkey, there’s typically a PIN you set up that the thief would also need to know. In addition, if the thief attempts to sign in on a machine you’ve never used, they’ll likely have to provide a second factor. If not… if you, for example, can sign in on a different machine with only the security key and its PIN, I strongly recommend you enable two-factor authentication.
Loss: There’s always another way in. It may be less convenient or more time-consuming, but you can typically sign in using an emailed or texted code, confirmation on a different device already logged in, or something else. Once in, you can then visit the security settings for that account and disable the passkey you’ve lost.
Some people recommend always using hardware keys in pairs: always set up two, and store one in a safe place in case you lose the first. That feels like overkill to me unless you’re in a highly secure environment where passkeys truly are the only way to sign in.
Do this
Though hardware keys are overkill for most users, I find them fascinating technology.
If you are considering using a hardware key for two-factor authentication and/or passkeys, just make sure to get one that’s FIDO2-compliant, so you’ll know you can use it for either or both when you need to.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.



Hi Leo, you said hardware keys are overkill for most people and you use a password manager to store your passkeys instead of a Fido2 hardware key. What is the best method to store the credentials for the password manager, password, passkey, hardware key etc?
Thanks.
I’m not sure I completely understand the question, but with a password manager I have one and only one thing to remember day to day: My master password. I “store” that in my brain. I do have backup storage (like 1Password’s “rescue sheet”), which I encrypt and store in a secure location, but that’s not what I use day to day. Everything else goes into the password manager’s vault.
Leo, thanks for all the great info. Can you suggest why some accounts offer a “passkey” system, but when I click start they want me to scan a code with a camera from my phone or laptop. I’m using a computer. Also, one account offered to set up a passkey, but then asked me to insert a hardware key. What’s going on? Many thanks!
Depends on the system, but my guess is: the QR code is likely for a companion app to be installed on your mobile device to act as a backup authentication approach.
When asked to insert a hardware key, a) make sure it’s passkeys and NOT two-factor, and b) look for something akin to a “try another way” link.
It’s early days, and in addition to users being confused about passkeys, my sense is a lot of the site are as well.
Leo, you wrote:
“Not also the notification: ‘2 of 25 passkeys used.’ “
Oops! Typo! 🙂
I move to amend by appending the letter “e” to the end of the word “not.”
Good catch. Fixed it.
From the article “ Loss: There’s always another way in. It may be less convenient or more time-consuming, but you can typically sign in using an emailed or texted code, confirmation on a different device already logged in, or something else. Once in, you can then visit the security settings for that account and disable the passkey you’ve lost.”
That said is a hardware key a false sense of security because there “is always another way in”. And that other can be exploited? What is the point of the hardware key guarding the front door when the back door is open to normal exploitation? Can accounts be set only using the hardware key, no secondary security, just the key? That’s the only way I would feel protected.
Yes, that’s a very good question. Your acount is only as safe as its weakest access method. You can disable the alternate access method, but that will leave you vulnerable to losing your account if you lose the device with your passkey. If the website allows it, you can use a strong second factor method to access the account. If you use an email address for account recovery, you can use second factor authentication to protect that email account.
Or you can install a passkey on more devices.
so passkey is only “memorize my password”, right? If one wants to avoid hackers use a only-machine-login method, one has to use hardware key.
I now tried samsung pass, I think it only memorize my password. Not “only owner machine can log in”.
I tried Taiwan government FIDO ID card for I wish can create a “only I can log in” way. it needs a reader card reader machine connect to computer.
Leo, I bought a “Yubikey 5 NFC” and I have created a Passkey for my Google account, but unlike you, it does not appear in the Yubico Authenticator app (in the Passkeys section). What could be the reason for this?
Without knowing the exact steps you took to create the passkey, it’s impossible for me to say. Sorry.
Hi Leo, I believe the procedure is the one you explain.
The exact steps are as follows:
* Manage your Google account
* Security
* Passkeys and security keys
* Create a passkey
* Use another device
* Choose where to save this passkey
* Security key
(After inserting the Yubikey and entering the PIN, it says:)
* Passkey saved
* Passkey created on your securit key