Don’t make this mistake yourself

Absolutely not.
This is a critically important distinction to make, and it’s one I’m afraid many people misunderstand.

Wi-Fi security happens between your computer and the Wi-Fi access point. Open Wi-Fi hotpots have no security. If you need a password just to connect to the network, it’s likely a secured connection, but your computer can’t tell you for certain. Webpages asking for log-in or acceptance of terms of service have nothing to do with security.
Wi-Fi security
When it comes to “open” Wi-Fi, security (or lack thereof) exists in the wireless connection between your laptop and the Wi-Fi access point.
An open Wi-Fi hotspot is an internet access point which requires no password to connect.
It is not secure, period.
It doesn’t matter what happens after you connect.
The Rule: if you didn’t have to enter a password in Windows or on your device simply to connect to the network, you are not on a secure network.
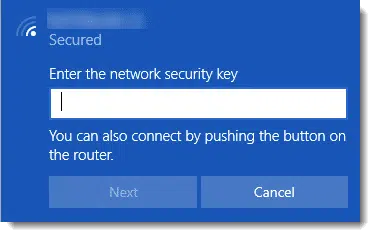
If you don’t need to tell your device the network security key — often referred to as the Wi-Fi password — and you’ve never connected to that network before, then you’re probably connecting to an open Wi-Fi hotspot. And again, an open Wi-Fi hotspot is not secure, period.
Which is which?
Almost all Wi-Fi enabled devices show you which networks are open and which are secure.
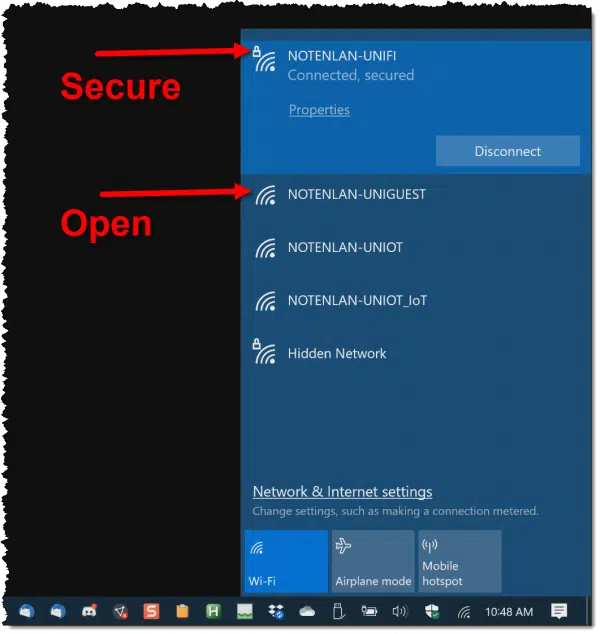
The presence of the padlock means the Wi-Fi network is secure and requires a password or network security key in order to connect. Your connection is encrypted.
The absence of a padlock means the Wi-Fi network is open, and anyone can connect. The connection is not encrypted, and unless you take additional steps, anyone nearby can see what you send and receive.
To add to confusion Windows will for some reason display an exclamation or shield for open Wi-Fi, and nothing for secure. In any case, the word “secure” is present for your connection if it is indeed secure.
The open Wi-Fi login
If the first thing you see in your browser is a log-in or Terms of Service page, you are connected to the network. The network is displaying that page. You’ve connected to the network, and probably the router; it’s just not letting you get any further until you log in or accept those terms.
If you can connect without giving Windows1 a Wi-Fi password, and you can see anything in your web browser — even that log-in page — then it’s an open Wi-Fi hotspot, and it is not secure.
If, for example, the coffee shop tells you a password to use, then:
- If you need to give it to Windows or your device so you can connect at all, that’s a secure connection
- If you need to enter it into a page within your browser, that’s an open connection, and it is not secure.
It doesn’t protect you; it protects them
If the connection isn’t secure, what’s that log-in page or “terms of service” all about?
What you’re seeing is called an “interstitial” page, which has nothing to do with technology and nothing to do with security. It’s about liability.
Technically, it’s called a “captive portal”, as it “captures” your connection and forces you to read and respond to that intermediate page before you’re allowed further.
Take a close read of the words on that log-in page. Chances are, all you’re doing is agreeing to the terms of service. The wording and specifics vary, of course, but in general, by clicking on “I Agree” (or whatever the button says), you are stating that you:
- Won’t download porn.
- Won’t use it for anything illegal, like downloading copyrighted material (such as movies).
- Won’t use it to stream “too much” information, flood the network, or adversely impact other network users.
- Won’t use it … well, in whatever ways the network provider doesn’t want you to use it.
Obviously, they can’t prevent you from doing that kind of stuff. But it does allow them to kick you off, and potentially even prosecute you, if you don’t follow the terms of service you agreed to.
So they force you to agree to those terms of service if you want to use their open Wi-Fi hotspot.
That’s all it is. It doesn’t protect you. It protects them.
Protecting yourself
So, if this log-in or accept-the-terms page has nothing to do with your security, how do you protect yourself?
Simple. Take all of the usual steps to use an open Wi-Fi hotspot safely.
Or don’t use the open Wi-Fi hotspot at all. Instead, provide your own, more secure alternative.2
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!




If the connection is made over a secure link (https://…), the WiFi link may be open, with no risk of somebody reading the data in transit.
Hi,
I think TrueCrypt is gone now. There are many alternatives.
I use SafeHouse Explorer. I also never have certain info on my laptop when I travel, encrypted or not.
Customs and TSA, and their counterparts in other countries may ask you to open encrypted volumes for them, and if you don’t, they can and will confiscate the equipment. Further, if they suspect you of wrongdoing, you could end up in situations you won’t want to experience.
If you’re worried about that, there are a couple of ways around that. Keep any sensitive files on a Veracrypt (the replacement for Truecrypt) volume a Boxcryptor folder online but not on your computer. Boxcryptor is probably better because you don”t have to download the whole volume to access one of a few files.
If you keep a Veracrypt volume on your machine, you can set up a hidden volume so you can give them the password to the innocuous data volume.
So would the connection be any more secure if the connection password was visible for everyone to see?
In a venue quite local to me, they have a wifi access, but the access key is printed on a sheet of paper and hung up for everyone to see. Meaning anyone in the room could connect to it.
Is that connection any more secure than if it had been completely ‘open’?
When you log in to the network with a password, the communication between the devices and the router are encrypted. You still wouldn’t be able simply sniff the data transmitted between the devices and the router. A hacker who understands how the packets are encrypted and decrypted might be able to use the password to decode the sniffed data, but that’s probably a rare scenario.
Actually that’s not true. With WPA2 the encryption key that’s actually used is unique to each connection, as I understand it. So with a WPA2 connection you still don’t run the risk of wireless packet sniffing.
IF (and only if) that’s the password you need to specify to Windows to establish the Wi-Fi connection, then yes. You are NOT using an “open” Wi-Fi, it’s actually protected by WPA2 and your data cannot be sniffed.
Ont the other hand, if you can connect to the hotspot, and it brings up some kind of web page into which you must type that password, then NO, it’s still an “open” wifi hotspot.
Thank you, Leo. I appreciate the info. A few years ago, I set up my friend’s restaurant router so that her access was password protected, while her customers did not need a password.
Based on what you say, I will suggest to her that we do the following:
1) Leave her network with her password (for her peace of mind)
2) Add a simple password for the customer network name, such as the owner’s first name.
3) Add a third network named: “MR Password = owner first name” or similar hint.
That way, even though it’s probably safe to let people use the main ID, she can feel safer, but meanwhile, the customers will definitely be safer. Thanks, again.
John
Thank you Mark!
I had steered away from connecting to it, ‘just incase’, but will consider it as somewhat more secure than any completely open options.
Answers it perfectly! Thanks again.
Thomas.
Is there a device that I could get that would connect to the open WiFi network but create a second network that is protected.
My smartphones are both on plans that are severely data limited (one is 1 gig per month, the other is 200-300 meg per month) so I’d rather use such a device that would create a secure way to use a public network.
The link to the open WiFi would remain unsecured, so … no.
A VPN along with a firewall and antimalware should protect you on public networks. https://askleo.com/how_do_i_use_an_open_wifi_hotspot_safely/
I carry a small travel router that connects between my device(s) and the open WiFi. It uses WPS2. When I get to my room, I set it up a Nam ready to go.
The problem with that is the connection between the pocket WiFi router and the open WiFi is unencrypted. It does offer the protection of a hardware firewall, though.
Leo:
“[I]n general, by clicking on “I Agree” (or whatever the button says), you are stating that you:
* Won’t download porn
* Won’t use it for anything illegal, like downloading copyrighted material (such as movies)
*’Won’t use it to stream “too much” information, flood the network, or adversely impact other network users
* Won’t use it … well, in whatever ways the network provider doesn’t want you to use it.”
AND there’s a better than even chance that there’s also boilerplate in there, granting them full permission and authority to monitor and capture every single bit (literally) of information you send or receive over their network, to use that data in any manner whatsoever that they see fit, AND completely and totally absolving them of any and all possible liability for any misuse of that data, intentional or otherwise.
Personally, I think Faust got the better deal.
One thing I notice about “free” wi-fi from some business places is that they want me to enter contact information first before I can get on. Then afterwards I find I’ve just become part of their marketing pool. Guaranteed to get emails or text messages about every new product or service they’re offering.
I just give them either a fake email address or I use my throwaway address.
“If you need to enter it [i.e. login credentials] into a page within your browser, that’s an open connection, and it is not secure.”
Technically that’s not necessarily always true. The web page could be served by a local network router or server, similar to the intrAnet in your company, or your router’s setup login page. I suppose Leo is talking about public venues which are not likely to have an internal (local network) gatekeeper.
Of course, I’ve also seen stupid network designs where the intranet (company services) is accessed via the public internet within the company!
Has nothing to do with corporate or other networking details. The only thing that matter here is: is the Wi-Fi connection encrypted (by WPA2 or similar). If not, it’s open and not secure. A login page doesn’t impact that.
I was just referring to your bullet statement under “The open Wi-Fi login”.
I am using Private Internet Access on all of my computers whether traveling or at home. I understand that the ENCRYPED data between my computer and the Internet could be seen in an open Wi-Fi. Does this reliably prevent anyone from seeing the unencrypted data I send and receive?
Yes, a VPN is absolutely one way to deal with using an open Wi-Fi connection safely.
Leo, you wrote:
“To add to confusion Windows will for some reason display an exclamation or shield for open Wi-Fi.”
Well of course, understanding the meaning of that icon would be a enormous help!
The “Exclamation-Shield” icon means danger (or at the very least, caution), which is why Windows uses this icon to flag insecure connections. (This is the exact same icon that causes such panic when seen in Event Viewer or in Device Manager.)
Naturally, secure connections don’t require the same level of concern, which is why they aren’t flagged.
It’s just Windows trying to be helpful, which, in this case, it pretty much is — always provided that you understand what the heck it is trying to say to you.
That exclamation mark inside a yellow triangle or shield mean “warning” or “attention needed.”
It does not always mean danger — it meany something requires your attention before Windows can continue normally.