How you can protect yourself in case they do
The best we can say is… maybe.
And maybe has been slowly changing over time to something closer to possibly.
It depends on a lot of different things, including the type of backup, where it’s stored, and most importantly, the specific ransomware involved. There are many different types (or variants) of ransomware, each with different characteristics.
Fortunately, there’s a simple approach to keeping your backups safe.
Become a Patron of Ask Leo! and go ad-free!

Most ransomware does not encrypt backups, but the possibility exists. The best protection is to keep backing up normally and periodically take an additional copy of your backup offline.
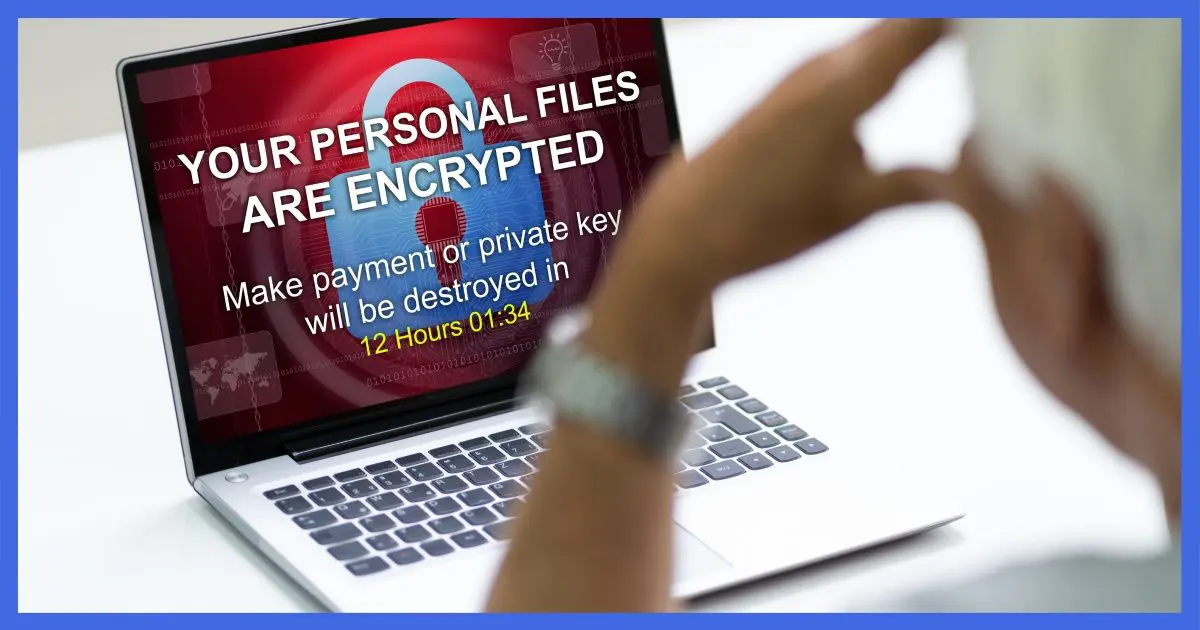
Ransomware
Ransomware is malware. Once it infects your machine, it begins encrypting files it finds there. Once done, it displays a message indicating your files have been encrypted. Your files are inaccessible to you until you pay a fee — the ransom — to get the decryption key.
One problem is that most ransomware is pretty good when it comes to encryption. There’s little chance of somehow cracking the encryption to get your files back. Typically, you’re left with three options:
- Pay the ransom. Strongly discouraged, as it encourages more attacks.
- Restore the files from a backup: strongly encouraged. This can make it all a non-issue, but requires that you have backups.
- Give up. Remove the malware, but live with the loss of whatever files were encrypted.
Relying on the backups, of course, assumes the backups themselves haven’t been encrypted by the malware.
What ransomware encrypts
What we call “ransomware” is not a single thing. It’s an entire class of malware that shares a particularly destructive behavior. There are hundreds, if not thousands, of different types of ransomware.
They differ in two important ways: where they look for your files and which files they choose to encrypt.
Drives scanned
Most current variations of ransomware scan only your system drive. For most systems, that’s the “C:” drive. Any other drives — including your backup drive — are ignored. This allows the ransomware to be fast, encrypting before you notice while still giving it access to your important files (typically also stored on C:).
More sophisticated variations that can scan all drives attached to the system, including external and/or network connections, do exist. Anything with a drive letter could be at risk.
One small bit of good news is only drives are scanned. Storage accessed only via your browser or a dedicated application, such as some forms of cloud storage and online backup services, are not directly at risk. There’s still bad news, however, since if those services mirror or back up files on one of your drives, it’s very likely they’ll mirror or back up the files once they’ve been encrypted, perhaps overwriting previously saved, unencrypted backups.
Files encrypted
Ransomware does not encrypt all files. It cannot. This fact is often overlooked in the panic.
It can’t encrypt everything; Windows itself needs to keep working, as does whatever mechanism the ransomware uses to display its demands and recover your files.
Ransomware usually targets what I call “potentially high value” files based on the filename extension:
- Documents such as “.doc”, “.docx”, “.txt”, and others
- Spreadsheets and finance databases like “.xls”, “.xlsx”, “.qbw”, and more (particularly impactful for businesses)
- Photos, including “.jpg”, “.jpeg”, and so on (particularly impactful for individuals with precious family photos)
This isn’t meant to be an exhaustive list, but it points out that not all files are always at risk.
In fact, if you’re using an image backup program, it’s worth noticing that I didn’t list “.tib” (Acronis’s format), “.mrimg” (Macrium Reflect’s) or “.pbd” (EaseUS Todo’s). More often than not, these files are not encrypted. Why? Well, since they’re typically large, the encryption process could take quite a bit of time, making it more likely to be detected before it does its damage.
So there are three possibilities for those backup image files:
- They’ll be ignored. This is still the most common.
- They’ll be encrypted. This can happen, but is less frequent.
- They’ll be deleted. This is rarer still, but would leave you without a backup.
While it’s infrequent, ransomware can encrypt backups, but we don’t know if it will. The best we can say is maybe.
What it takes for backups to be encrypted
In order to truly put your backups at risk:
- The ransomware variant needs to scan more than just the C: drive.
- The ransomware variant needs to choose to encrypt backup files.
Most ransomware today does not have both those characteristics. It’s not likely to happen.
But most is not all. You could encounter ransomware that encrypts your backups.
How to protect yourself
The knee-jerk reaction to hearing that backups might get encrypted is to disconnect the backup drive when you’re not actually making a backup. Don’t do that.If you do, backups are no longer automated. You have to remember to reattach the drive in order to back up. Forgive me, but I don’t want to rely on your memory — or mine, for that matter — to perform backups. Especially when (today, at least) the risk we’re trying to avoid is relatively small compared to the many other reasons you want that backup to happen.
My recommendation:
- Keep backing up as you do: automated, with your backup drive continually attached.
- Every so often, make a copy of your backups somewhere else. Copy them to some device which is then disconnected. It could be another external drive or even another machine on your network. One approach is to have two backup drives but only connect one at a time, and swap them periodically.
Don’t get me wrong: the risk of ransomware encrypting your backup exists, but it’s still on the low end of the scale.
It’s much more important that your automated backups continue to help you recover from more likely issues.
Of course, the best defense is to never get ransomware (or any malware) in the first place, and stay safe in general.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!




The key words are “might” and “currently.” The people who design malware are not idiots. I would suggest that the probability of backup files being affected will be increasing over time, so worry about it now instead of having to buy extra boxes of Kleenex later on to wipe away your tears when it happens. I would suspect that if you don’t go where you shouldn’t ought to go on the internet, and don’t click on email attachments, the likelihood is that you won’t have to worry about it.
“I would suspect that if you don’t go where you shouldn’t ought to go on the internet, and don’t click on email attachments, the likelihood is that you won’t have to worry about it.” – Yup, absolutely. Probably 99% or more of malware infections are the result of some form of user action, such as opening an email attachment. Commonsense is by far the best defence.
I’m reading this a lot in forum comments. However, I’ve never seen it substantiated by any hard data.
Not wanting to be personal here, but I have a feeling that sort of statement comes from a sort of “serves you right” attitude. Some people seem to think that they are immune from malware because they just know better, and if you don’t, tough luck.
What is, however, absolutely proven, is that you don’t need to do anything to be infected. Visiting a malicious or compromised site and doing nothing more is enough. And compromised sites need not be porn or hacking related, to be clear.
Thanks again, Leo, for very good info. When I first read about ransomware I was happy that my backup routine eliminates the possibility of being targeted, since I backup every week or two and in between save important files to a flash drive that I keep plugged in at all times. If ransomware gets to that I won’t have lost much.
Another reason I actually CAN’T keep my external backup drive connected all the time is that often my computer will not boot with it connected (yet once in a while it will). Very weird. I noticed last time I did a backup and forgot and left the external drive connected, the next time I tried to boot the computer it wouldn’t boot. Would love to know what’s causing this problem.
Also, I am confused about backing up while I’m using the computer–I think it’s said that it’s ok to do that, but I think I read someplace else that it’s better not to be using the computer. I keep my computer turned off when not in use and don’t have a set time that I will or won’t be using it, so seems impossible to schedule a time for automated backups without having to remember to have my computer booted at the same time everyday..
Maybe for ‘everyday’ computer users (without a lot of critical data to worry about) my personal routine is best–though I would love to go automated and not have to remember to backup!
Ejecting the drive – using the Safely Remove Hardware feature – prior to shutting down may solve the boot issue. Backing up while using the computer will not cause any problems whatsoever, but you may notice an impact on performance.
Thanks, that very well might be it. I’ve been running Easeus Todo Backupper after I’m finished for the day (every week or two) and setting it to shut the computer down, so I don’t get the opportunity to safely remove, so makes sense that sometimes the computer will boot (at times when I have used the drive and safely removed), but sometimes it won’t.
Carefull with terminology: “EaseUS Todo”, and “Backupper” (a product by AOMEI) are two completely different products.
Sorry, that’s what 2 hrs of sleep at night gets me!
Oh, and there are a number of things you could try to get the PC to boot with the drive connected and powered on. You could try altering the boot sequence in the BIOS and disabling legacy USB support. Or, if the drive is USB powered, you could try connecting it to a powered USB hub. Unfortunately, the issue could also be caused by an incompatibility between your PC, in which cases there is really nothing you can do about it.
yep….hopefully Liz does NOT have a ‘Dell” proprietory hardware…..
perhaps, you should make that external backup drive, a ‘read only ATTRIBUTE…(ATTRIB) command in shell. Then, when you boot, it should see it……….oldguy
If you make the external drive ‘read only’, you won’t be able to back up to it. You’d have to change the attributes before running t a backup. That’s more complicated than unplugging it an plugging it in each time you perform a backup.
Hi Leo,
Is there a program that you would recommend I download to display reminders on my desktop? I find it easier to keep track of important dates using my macbook due to the built calendar function on the Mac. However, I find the windows calendar more tricky to navigate.
The reason I’m asking on this post is because I don’t usually keep my external hard drives connected to my macbooks or desktop machine. I’d like to have some sort of software (or learn how to use windows 7 built in calendar) to remind me to back up.
Thanks for your time,
Sean
“Keep backing up as you do: automated, with your backup drive continually attached.” – I agree. And your second point – to also back up to a secondary location – is equally as important as a power surge that takes out your PC could also take out your primary backup drive. Creating a secondary backup in the cloud is the best option as this also provides protection from local disasters (fires, floods, etc.).
what’s funny is when i was taking a hardware course many years ago, our instructor said to back up our files on an external drive, tape drive, cd, thumb drive….even toilet paper if you have to. point being is that if multiple copies of your backup files are made then it’s more likely that your data will be recoverable.
An interesting article. Apparently malwarebytes have introduced this:
https://forums.malwarebytes.org/index.php?/topic/177751-introducing-malwarebytes-anti-ransomware/
Not sure if it will work, but I tried the beta version and kept getting BSOD. Apparently there are all sorts of issues at present. If they do manage to get it working that could be a great thing.
Not sure of your take on this Leo.
It’s an interesting program, but I’ve read of quite a few problems with it – from performance issues to false-positives. It’s probably best to avoid while it’s still in beta (unless you’re not adverse to testing work-in-progress software that may cause issues with your PC).
It’s also important to balance the pros against the cons. In the case of Anti-Ransomware, the pro is, obviously, that it may protect you from ransomware – although, as current variants are only distributed via email attachments, you can easily avoid infection simply by exercising caution. The cons are that all programs that run in real-time have a performance impact and that all have the potential to cause problems – whether it’s deleting something that shouldn’t be deleted or open up other vulnerabilities on PC. For example, Malwarebytes’ Anti-Malware was recently found to contain exploitable vulnerabilities: http://www.zdnet.com/article/google-lays-bare-security-flaws-in-anti-malware-product-with-250-million-users/
Personally, I wouldn’t use Anti-Ransomware, even once it’s out of beta, as I think the pros are outweighed by the cons. As I said, current crypto variants can easily be avoided by exercising caution with email attachments so I consider the risk of my PC being compromised to be extremely small – small enough that I don’t feel it necessary to install a program to mitigate the risk. You mileage, of course, may vary.
I have heard that the current beta is a tad unstable. I look forward to seeing what it eventually turns into. (Though it really doesn’t change my position: backups, common sense and avoiding the problem in the first place are by far more important than any specific tool you might try to throw at your computer.)
Crashplan backup by default keeps old versions of files backed up forever, so even if ransomware encrypts a file and it gets backed up to Crashplan, you will always be able to go back in time and grab the previous version of the file.
Of course, really smart ransomware could change your settings in Crashplan to get around this. For a variety of reasons, I don’t see that happening any time soon, but it highlights the major problem with malware: Once you are infected, all bets are off.
Yup, backing up to a well-known reputable online service in addition to backing up to an external hard drive is absolutely the best defence; not only against cryptos, but also against other risks that could potentially impact on-prem data – fires, floods, power surges, theft, etc. For the average home user with an average amount of data, online backup is now so cheap – if not completely free – that it makes absolutely no sense not to do it.
i do multiple level backups – some miight say overkill, but it is working for me.
1. Image backups – every week or so, for c: drive. (Paragon hard disk suite)
with daily computer usage, I would assume that I would notice if files are being corrupted/ransom-encrypted;
BUT – i keep multiple dates of images. So, I could go to a prior image if needed, for recovery.
now, that takes care of c: drive
d: drive, data –
I back up to multiple (rotating) external drives. I DO rely on memory, specifically because I don’t want the drives connected.
I also back up to amazon (have unlimited account, $59.00 per year)
I ALSO back up to ATTACHED drives, that are now BITLOCKED, and I only mount the bitlocker drive when needed, because ransomware can’t access the drive if not mounted. I WAS using truecrypt/veracrypt systems, BUT since that is actually a volume on an existing drive, ransomware might attack the .TC or the .VC file itself.
I use a program called syncovery, to sync the d: drive and the external drives. It will encrypt the file name and folder names, for other security reasons.
AND, in future ,when run, it may detect “if x% of files are being changed on destination”, PRIOR to the sync, so you would see if your backed up files were being overwritten.
Beyond that, if they crash my computer, I give up : – )
My nephew was hit by cryptolocker last year, all files and local backups. All 2,000 dropbox files were also updated to the encrypted version. We were only saved by the dropbox rollback command. So my suggestion is simply cloud storage with rollback.
Dan – exactly what I had to do last week with Dropbox and it was successful, once you know the first date which Ransomeware started encrypting your files as it took them 3 days to encrypt all the personal files on my daughters’ laptop, despite AntiVirus… Just be sure to delete the entire Dropbox folder contents BEFORE requesting the Rollback and preferably “Unlink” the Hard Drive from the Dropbox cloud. Then once the Rollback is complete, you can review what has been restored into the Dropbox Cloud, catch your breath… and if it all looks good, “Link” the computer hard drive to the Cloud once again…
That’s a great layer of protection. I use it myself, but it’s no substitute for a system image backup. The more backups, the merrier.
I like this info Leo. What I usually do is disconnect my drive after a back up and if I do a restart Norton will prompt me for a backup. Another comment I like to make could we name the backup drive a specific name such as letter and numbers almost like a password.
I use a log on script and map a PC to another PC/File Server drive. Then I run the backup to the newly mapped backup location. Once the backup is complete the script then disconnects the mapped drive meaning the ransomware can’t see the backup location, and can’t attack it accordingly.
If you are running 2 PC’s you can perform this on BOTH PC’s meaning that you have original data and a backup of the secondary PC on both units. Of course this does mean having a large capacity drive available for the purpose though!
From there an external backup drive can be used to create another copy of the backup/data.
Overkill maybe but I would rather multiple copies of my data giving myself a greater protection level.
I swap daily two external backup disks. And I image daily with Macrium. So theoretically, the ransomware would need to encrypt Macrium files, and it would need to implement some delay mechanism, by which it would infect one backup without raising alert, then the other one the next day, then the internal disks, then ask for money once all files have been encrypted.
Perverts abound, so that’s possible, but still, highly unlikely.
Regarding unplugging and remembering to plug in back up drive – I have used a program called “Remind Me” from Beiley Software for years. Among other things it can be set to pop up a message to remind me whatever I set it up to tell me on a daily, weekly, monthly or yearly or one time only basis. I have set it to remind me weekly to “back up computer”. Now I just have to make sure to stop whatever I’m doing at the moment and plug in the drive.
My suggestion for critical drive backup is to purchase: 1) a spare hard drive equivalent to that installed in your computer, 2) Acronis True Image backup software and 3) a USB drive adapter to interface with a bare hard drive. With this combination you can do a manual backup at a frequency you are comfortable with. In addition, on a more frequent basis, I suggest to do minor backups of important data that has changed, onto a flash drive. Then if you experience an attack, swap out the compromised hard drive with the latest backup drive and… voilà.. online again. You can then restore the compromised drive with with data from the original backup drive and use it as the new backup.
Swapping out the hard drive with an image backup won’t work, as an image backup is a copy of your system drive compressed into one or a few files. It is possible to create a bootable clone as a backup, but this wouldn’t allow you to do incremental backups. And you are probably better of using Macrium Reflect or EaseUS Todo backup as you can get more help on those programs from Ask Leo!
1) I use Linux Mint as my main PC. w/Dropbox (no auto-start)- I log in when ready to copy files to it only
2) Two portable HDDS, each has folder w/year & inside, folders for months
3) backup by copy/pasting my user folder 1-2 times a month. To be extra cautious, you can AV scan the files you’re copying beforehand.
4) every few months, I delete the oldest month, saving three copies for each year.
5) repeat
I do NOT leave my drives plugged in when not in use & I copy to them one at a time (one plugged in, then the other- not together). So far, in 15 years (using backup media available at the time), I haven’t had any issues.
In my mind, the concept of connected devices (whether local or cloud) is they’re basically just a target waiting for someone to find the key. It’s not a big deal to me to: select>copy>paste my data out to my HDD’s. If you want a reminder, then use a calendar, etc if you must. But this way you know your data is as safe as it can be. I’ve seen far too many auto-backup software fail to either copy properly or restore properly. No thanks. Copy/paste>done.
I am, to be clear, speaking residential here. For business, it’s made a bit more difficult. However, I don’t see why a batch file or script can’t be written & launched to automate things somewhat.
FYI & Imho
The problem with this strategy is that, unless you’re keeping the drives in a fireproof safe – one that’s rated for electronics – or storing them outside of your home, your data is vulnerable to fires, floods, theft, etc. To mitigate these risks, I keep data on a fire/waterproof NAS (an ioSafe) which is automatically backed up to the cloud.
What I haven’t seen discussed here and elsewhere is preventing infected files from getting backed up. I keep my backup drive disconnected. Prior to connecting it, I run Bleeping Computer’s Listcrilock.exe. This program very quickly (instantly) determines if there are any ransomware encrypted files on the computer.
Should a problem be detected, I would then make a full recovery from my external hard drive booting with a DVD. IF there is no problem, then back up can be run.
Actually, I run a two stage operation. I first automatically backup to a second internal drive. Then, every couple of days, I copy that to the normally disconnected external drive.
I have assisted two clients who were infected with ransomware. The first client had no backup of any kind. Only his .docx, .xlsx and .jpg files were encrypted. I made a clone of his HDD, did a clean install of Windows 10 and then restored the unencrypted files from the clone.
The second client did regular backups to a NAS device (Western Digital My Cloud). Since this device is not directly connected to the computer the ransomware did not gain access to it and her files were intact. However, the ransomware encrypted the filenames as well as the contents of the files. This was a *good* thing because these files did not overlay the previously backed up files. Before starting the restore operation I deleted all of the encrypted files on the My Cloud. Then I restored her files to a clean install of Windows 10. There was also a 32GB USB flash drive attached and files on it got encrypted.
I’d like to know if my thinking is correct.
The time taken for ransomware to encrypt a drive is minutes to days. Also, some ransomware encrypts your files and lies low for a while, days to months, before making a demand for ransom and preventing you from accessing your files. The point is, there is an interim period of time when your system works normally even though some files are encrypted. Which means that the ransomware is decrypting and encrypting files on the fly for applications that want to use the files.
The type of backup software you use is critical. If your backup software creates disk images (bit-by-bit copy), then the backup image *during the interim period* will contain encrypted files. If the backup software does a file copy, then *during the interim period* the copies will be normal (unencrypted) because ransomware would decrypt files to allow the backup application to read files (unless the ransomware recognizes backup software and acts differently).
Conclusion: File copy backups are better than disk image backups as a protection against ransomware.
Caveat: If file copy backup software creates a mapped drive (I don’t know if they do), either permanent or for the duration of the backup, then the copied files are at risk.
I don’t agree with your thinking here. The point of an image backup is to do it when your machine is malware free. The *real* point is to have something to easily revert to in case of a malware infection… be it ransomware or another type of malware. Revise your thinking in a couple of ways and you’ll get the protection you are looking for.
Get that image backup done and set it up to run automatically. Back up your “backup file” occasionally when you know you are clean; have that on a disk that is not connected to your computer – in the worse case scenario you use this to go back to a clean machine using that last backup date. In other words: even if you do that today and need to use it a year from now, you are at least going back to a clean and usable version of your computer. It doesn’t hurt to have some method of file backups going as well for recent files – cloud based systems can be good for this – but rely mostly on your image backups.
And finally, stay safe on the internet! In the end ransomware needs to be installed through some action.
Didn’t notice the reply button. Please see below.
I would say it is more important to have the most recent good data, rather than be able to revert to a working system quickly. But yes, priorities will differ depending on the system and data impacted.
“… when you know you are clean …”. How do one know a backup(s) is clean? How does one automate the process of checking they are clean? This is crucial and is a whole other discussion which I did not bring up earlier.
I have not seen any good time analysis of ransomware. What are the typical time periods between the stages: Exploit –> Files encrypted –> Ransom announcement? When ransomware lies low, does it lie low after the exploit stage or after the file encryption stage? (If the former, some of my earlier post is incorrect.) It is important to understand this before deciding on a backup-restore-check plan.
If I keep my files and folders in a Vera Crypt container are they safe from ransomware? Would I have to keep the container closed most of the time to render my files and folders immune? Does ransomware know how to find it’s way into an open Vera Crypt container?
It depends on the ransomware. There are as many different answers to your question as there are variants of ransomware.
If your VeraCrypt container is mounted and its contents visible, then some ransomware might encrypt some of the files there in. Other ransomware might not. Some ransomware might encrypt the container itself if it’s not mounted.
Worry less about the specifics of ransomware, and keep yourself protected and safe from all malware instead. Ransomware is just malware.
I know you are typing to make this simple but the most foolproof system to date is:
1. Backup whatever folders contain data that you do not want to lose using a recognized rotation scheme and software (e.g., Acronis with one full and seven incremental backups per week, maintaining whatever depth makes sense to you. (I retain four cycles — four full and 24 incrementals. All of this is easily set in any reputable imaging and backup software.
2. Set a schedule to back up designated folders unattended so you don”t have to remember.
3. Back these files up to a NAS (network drive) or a portable backup drive attached to your computer via a USB 3.0 port. Costco sells a variety of sizes.
WHAT FOLLOWS IS THE DISTINCTIVE STEP
4. Most backup software will allow you to execute a program including a batch file before and after the backup executes. Create two batch files, one to mount the USB or NAS drive before the backup and a second to un-mount the drive when the backup completes. You may need to get help with this step but many amateur computer geeks know how to write batch files. I have listed an example of each below. If you get the basic idea, you can use them as templates.
If your imaging or backup software does not support running before and after backup programs, you will have to perform this step by hand or change software.
By having your drive mounted only during the backup period (typically only a few minutes for daily incremental backups), you minimize the chance of being attacked, especially if you schedule the backups when you are not opening email, etc.
Please be sure to get help if you are not comfortable writing batch files. They are easy and you might find it worthwhile to learn. Note: The commands used below work from Windows Vista forward. They will have to be modified slightly for older versions of Windows (delete or modify the “Choice” command) or for Apple computers.
SAMPLE DRIVE MOUNT BATCH FILE
@echo off
REM Be sure to change this to the drive letter you want to mount the drive to!
set drive=G
REM Be sure to change this to the Volume Name of the drive you want to mount!
set volume=\\?\Volume{18d824d9-7d2f-11e3-a70f-386077904405}\
:start
echo Mounting Drive…
mountvol %drive%: %volume%
echo Drive Mounted!
echo Pausing 3 seconds . . .
choice /C X /T 5 /D X > nul
exit
SAMPLE UN-MOUNT BATCH FILE
@echo off
REM Be sure to change this to the drive letter you want to mount the drive to!
set drive=G:
echo Unmounting Drive…
mountvol %drive% /p
echo Drive Unmounted!
echo Pausing 3 seconds . . .
choice /C X /T 3 /D X > nul
exit
Good luck!
I have a hybrid approach because my consulting and teaching work demands not only secure backups but instant access to files when traveling, in case my trusty ThinkPad has a problem, or is stolen: First, I use Carbonite to back up files pretty much in real time. For some extra important files I click to have the backup done immediately, as soon as saved, rather than wait until the next daily scan it does for backup purposes. Second, I use Macrium Reflect to create a *full* image of the PC about once a month, plus each time I have any software or hardware changes to do. This combo saved the day last month when the HD on my fairly new, name brand desktop croaked. BTW, in the event a ransomware program manages to infect a file just before it’s backed up, Carbonite archives previous versions of every backed up file:
Old versions of changed files are kept for up to three months, as follows: One daily version of the file for each day of the past week, one weekly version for each of the previous three weeks, and one monthly version for each of the previous two months that the file has been backed up. And at least the three most recent versions of a file are always kept, regardless of age.
I am in the middle of a ransomware recovery. DMA Locker 3.0 besides locking the files, knocked the backup drive to an offline state that can’t be reversed. Per usual – disabled the antivirus and uninstalled the Carbonite applet and made a change to the account name associated with the Carbonite account. With some searching through billing records they were able to determine the correct account and then the engineers began to prep our data for recovery. They were sure to eliminate any files with the corrupted date time stamp.
“The knee-jerk reaction to hearing that backups might get encrypted is to disconnect the backup drive when you’re not actually making a backup.
The problem with that is the backups are no longer automated. You have to remember to re-attach the drive in order to back up.”
This is actually not a bad strategy, i un mount my backup drive after each backup, and remount before starting, this is done by scripting using mountvol.
Some backup software allows for you to use before and after scripts so makes it easy. However you could simply run the scripts as tasks prior too and after each backup.
In my situation i have a small home server Win 2012R2 built on Hyper v that is only accessed via Remote desktop and contains mapped NAS drives of data to be backed up i use backup assist and have the below scripts run before and after each backup , the backup drive is an encrypted USB drive. works like a dream.
********************************************************************************************
Cls
mountvol A:\ \\?\Volume{b7e4e1a8-c0ef-4b75-aa72-6ef81395c4cf}\
Exit
********************************************************************************************
Cls
mountvol A:\ /d
Exit
********************************************************************************************
A fine approach for those capable of figuring it out. For the average consumer, however, I’d rather have them keep their drives connected and backing up regularly.
Had a laptop hit with what we think was a first version of Cryptowall. Took all files just left empty ones. Never paid the money. Had a local company totally wipe the laptop and reload OS. We still have the Seagate stand alone backup drive. Just never plugged it in to the new computer fearing it may be infected and wipe out the new laptop. Any suggestions on looking at that old drive to see if backups exist? Very leary about plugging it in and opening it up.
The chances of getting malware from that drive are low but just to be sure: Get a live bootable Linux distro install it to a DVD or USB flash drive. Either Mint or Ubuntu are good versions for that. Boot from the disc or drive and you will be able to access the files on that drive without activating any malware on it. If you used a backup program to create the backup. Use the rescue disc or flash drive you created or create a new one and boot from that. You should then be able to safely mount the virtual drive and restore your files.
thx for that!
I have read the pros and cons about disconnecting the external backup drive. As you have said Leo, Randsomeware (or other virii) are unlikely to encript an external drive … BUT it CAN happen. So being a super careful type I disconnect. My precedure is to make a Backup every Sunday night using EaseUS Todo Free. I use a scheme to remind me to make the backup … which I found on the HOWTOGEEK page. https://www.howtogeek.com/136894/how-to-create-popup-reminders-with-no-additional-software/
Fairly easy to set up and I make it pop-up at 10.00pm Sunday evening. The Back up takes in the order of 4 hours and then the machine goes to sleep, if I make it turn off, I invariably forget to disconnect the external drive and experience the same problem that Liz has …. wont Boot! By putting my machine to sleep, I am reminded it is Monday morning and that I should delete the oldest backup (I keep the last 4) and then disconnect the external USB drive.
Thanks Leo, and Team Leo for a wonderful source of help and hints. Chris
Good common-sense article from Leo who makes it clear that you cannot make yourself 100% safe, but if you do the right things, especially by keeping good backups, you’re going to be reasonably safe.
Thank you!!
I use the backup program/application that creates *.tib and lately *.tibx (not to advertise the product name, unless you (Leo) decide to).
Since around a year ago that program/application has a built in security feature against ransomware.
Of course I always keep copies of my *.tib and *.tibx files on a second HDD that is only on when I make the copy, regardless, but I believe if you (Leo) check the latest version of this program/application, may be you’ll find it right to advise most readers accordingly on this issue. I also believe it is only a matter of time until all backup products will have such a protection, but until then…
Best regards from across the ocean 🙂
Sounds like Acronis. Macrium Reflect has had a similar backup-protection feature for some time as well. I really like it.
No reason not to mention that you are using Acronis True Image. Leo used to recommend it but now he recommends Easeus Todo or Macrium Reflect.
How much does syncing my files to One Drive help protect me from Ransomware (or does it at all)? Can ransomware encrypt my files on One Drive? I am a retired Home User, so I do not have the resources available to large businesses or corporations. I do however suspect that I am as much of a target as anyone else on the Internet and that it would be foolish to assume otherwise. What do you think Leo?
Your own backups are most important, but yes, ransomware can affect OneDrive (or Dropbox or others…). This article has a section on it: How to Protect Your Cloud Storage and Backups from Ransomware
I can definitely say, YES! I have had customers & family get ransomware and their external backup hard drives also were encrypted (unable to restore).
Luckily, we setup on multiple backups and were able to get the previous weeks backup drives and, after thorough cleaning and removal of infections, do a complete clean restore.
We use Macrium Reflect and their later, Paid, Version (over the last couple of years) has a feature called “Image Guardian”, that locks down the backup hard drive and only it can right to the backup drive. It has worked quite well, and I am sure many other backup producers have added such protection by now.
What we like about Macrium Reflect is, it is very affordable, reliable, easy to use and tech support has been great (always one of the most important things!). And I believe one of the first (if not the first) to add the hard drive backup protection!
If I understand correctly, if you wish to write malware to attack unmounted devices, you can use the mountvol command to discover volume names. You can then mount the devices. It takes some parsing of mountvol’s output, and you have to run your malware as administrator.
I haven’t tried it, but your victim might thwart your malware with a USB switch to de-power the device, or an “AB” switch that connects a device to either of two computers, by switching the device to a non-existent computer.
I am a computer service/repair guy down here in New Zealand, one of my clients had a ransomware attack and IT DID ENCRYPT the backup drive plugged into the PC at the time and also some shared folders over the local network on other users PC’s
Yeah, it’s unfortunately starting to happen. It’s not the majority of ransomware attacks, but it’s definitely happening.
Leo:
Would it be beneficial to rename doc, txt, jpg files (etc) to something else (like d1c, t6t, and j4g respectively) as long as we remember to change the file name back to doc, txt, jpg (etc) when we want to open or use the file again? I know there are many, many file extensions that are used by other programs, so finding a good file extension to use might be hard to do. Even if we change the file extension, I wonder if ransomware looks IN the files to see if it is a document or photo file.
I don’t believe ransomware looks in the files, but honestly — what you’re describing sounds like a lot of work, possibly error prone, and could STILL be encrypted by some forms of ransomware. Sorry.
For desktops:
1. Attach a mains powered back up drive and plug the power cord into a mechanical timer (the kind you use to switch your Xmas lights on and off). Set it to come on at X o’clock, and off at Y o’clock each night while you’re dreaming of a Covid-free. politically stable world.
2. Set Macrium Reflect or similar to clone your C drive within those hours (with a little buffer before and after to allow for the timer’s mechanical inaccuracy.
3. Assuming ransomware isn’t able to infect while the computer isn’t being used, you should be 99% protected.
4. For 99.9999999%, you could plug your modem into the same timer (I don’t bother). It’s not 100% because I suppose it is possible for sleeper ransomware to infect during the day unseen and activate during your chosen cloning time. For laptops at home you could do the same, but if you’re in say a hotel, I can’t think of a reliable (i.e. non-memory reliant) way to ensure internet connection is off during the cloning process.
Hope this is useful.
I have run a small one man shop in my town for the past 10 years. Coming from IBM I am very conscious of need for backups and the damage Ransomware or malware can do a client’s data, so for years I have recommended full system backups, originally I used True Image, but over time I have switched to Macrium Reflect. Last year I had recommended a client use it on her computer and assured her this would get us out of a jam, should anything happen. Well it did happen and no, the backup did not get us out of it. Both full image backups were encrypted with the malware, just like all her files. The only thing we were able to recover was from a 10 month offline backup and that meant lots and lots of email was missing, (she runs a small business from her home and this was a huge deal).
So, if recovery is really important, definitely keep a fairly recent backup offline. I felt terrible that she trusted me and what I thought was safe, turned out to not be.
NOTE: I also had Windows 10 file history running, but of course it was encrypted as well.
Really IMPORTANT specially for those with large systems and important Data…I would suggest keeping backups of more than 30 days on EXTERNAL DRIVES, MORE THAN ONE.. And to Start your computer, using an EXTERNAL “Rescue Media” and if you like to be more sure, create TWO Rescue Media, on two dates at least 31 days apart. .And Start your PC using one, if not successful, use the other.
Mounting and unmoving the back-up clone.
Powering up and shutting down the backup clone.
Assume the cloning operation is done once a day (or once a week, or other than that). It s better to mount the back-up clone immediately upon stating the backup task, and un mounting it after. Why ? Because it is harder for the ransomware to mount an unmounted drive. That can be automated with the back-up software (CarbonCopyCloner does it for me).
Backup drives can be powered immediately upon mounting. To do that, you can use home automation software. (1) it triggers drive power-up through an instruction to the drive’s electric plug. Once done (2), it triggers the initiation of the mounting and back-up task, through a shell script addressed to the backup software, (3) upon end of backup and drive un mounting, the backup software informs the home automation software that it is time to unplug the drive, which is achieved through an email initiated by the backup software and listened to by the mail application, which issues accordingly an instruction to the home automation software. For a 20 minutes backup occurring in the dark of the night, the backup drive is fed with electricity and mounted on the computer only 20 minutes., which is kind of neat.
You can increase level of protection (and complexity and, unfortunately, power usage) by backing up to a network computer (which then also needs to run during the night). There is no way the ransomware can follow you there.
Warning, a fire in your home will still destroy your local backup however protected it may be.
FWIW
Interestingly, just a couple of days after reading this, ransomware got to our OFF-SITE server system and made everything go away. About 8 TB of data vanished in a short time. [Still trying to figure out how they got in – all our machines appear to be clean.] No way they actually encrypted everything, and no big list of encrypted files. Just a ransom note and a couple of relatively small data files. My guess – they played with the directory structure in order to hide everything. Still wish I knew what they did, though. [At least it *was* the backup, so we can just back it all up again.]
Easeus Todo has just announced a new feature that they have called the Security Zone. This is a segment (unmaped?) of the external backup hard drive that is only accessible to the Easeus Todo program and not to File Explorer. The intention is to make it inaccessible to malware — especially to ransomware. The capability to run automatic backups is also provided.
This is good news. Macrium Reflect has a similar feature, though its files remain visible to File Explorer, but locked down using Windows File Permissions.