And why we’re still vulnerable to well-crafted scams.
I was listening to a podcast recently where the hosts were discussing an account-hacking scam that tricked people into sharing a one-time code they had been texted or emailed.
One of them brought up the apparent contradiction with messages saying “never share this code” specifically when you’re being asked to enter — or share — that code with the service you’re signing into.
Let’s clarify that, shall we?

To share or not to share that code
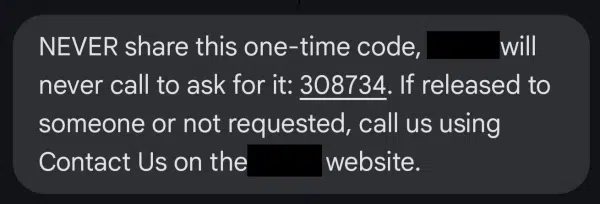
Although one-time codes are meant to enhance security, scammers exploit the contradiction of being asked to “never share this code” when we do need to enter the code with the site we’re signing in to. Key advice: only enter codes on official sites; never share them over the phone.
Let’s look at the normal uses of one-time authorization codes: when you’re signing in to a device for the first time, making security changes, or recovering access to your account. Then we’ll walk through two common scams, one over the phone and one through email, that try to trick you into sharing that code when you shouldn’t.
Normal use: signing in
The most common use of the one-time code is when you’re signing in to your account, typically for the first time on some device. If you then use the “remember me” or “trust this device” feature, you won’t be asked for a code again.1
The sequence usually works like this.
- You visit a site’s sign-in page.
- You enter your username.
- You enter your password.
- You click Sign in.
- The service asks you for a code.
- That code is sent to your phone via SMS or to your email account.
- You enter the code, and you’re signed in.
Your ability to provide that code proves you have access to that phone or email account and acts as a second factor confirming your identity (your password being the first).
Help keep it going by becoming a Patron.
Normal use: extra security
You may be asked for your code at other times. For example, if you’re about to change your account’s security information, you may be required to re-confirm that you are authorized to do so.
Some services simply ask for your password.
Others send a code to your phone or email and ask you to enter it to prove, once again, that you are who you say you are. This is more secure than asking for a password. Should a hacker gain access to your account and password, asking for a code prevents them from making changes.
Normal use: account recovery
Let’s say you’ve somehow forgotten or otherwise lost the password to your account.
An account recovery process uses alternate methods similar to the two-factor methods mentioned above to confirm that you’re authorized to enter the account and set a new password.
Once you begin the process, the service sends a code to your phone or alternate email address. Your ability to enter that code proves you have access to the device or email account associated with the account you’re trying to sign in to, and thus should be allowed in.
So far so good.
In all these cases, though, it is kind of a contradiction to say “Never share this code with anyone” as they’re asking you to share the code with them to sign in or make other changes. It’s a reasonably good approach to maintaining the security of your account.
But that doesn’t mean it’s perfect. Let’s look at those scam routines.
Basic scam: the phone call
Here’s the sequence scammers use.
- The scammer visits a site’s sign-in page.
- They enter your username.
- The scammer then calls you2. Their request is similar to this:
“Hello, we’re from <the service’s> security department, and we’ve noticed some suspicious activity on your account. I’m going to send you a code to confirm that you’re in proper possession of your account. When you get it, please let me know what it is, and we’ll know your account is secure.”
- They click the link saying “I forgot my password” or “Problems signing in?”
- The system sends you a code via email or SMS.
- Believing the scammer to be a legitimate representative of the service, you tell them the code.
- The scammer proceeds to sign in to your account and wreak havoc, possibly changing your password and preventing you from accessing the account thereafter.
This scam leverages the fact that you’ve been “trained” to provide the code to the service when you sign in. It’s not a huge leap to think it’s OK to share the code with the service over the phone — even though it’s not the service at all.
The telltale sign? They called you. Legitimate services never ask for these codes over the phone, and they never randomly call you and ask for these codes.
Never.
Bonus scam: phishing
The phone-call scenario is a variation of a scam I’ve talked about before. It works like this.
- You receive an email indicating that something important about your account needs your attention. It implies it’s an urgent, time-sensitive issue. It includes a link to click to resolve whatever the issue is.
- You click on that link.
- You’re taken to a page that looks exactly as you expect. It’s a near-perfect copy of the service’s sign-in page. Except, of course, it’s not the service’s page at all, but a page crafted by the scammer.
- You enter your username and password to sign in. The scammer now has your password.
- As you are doing this, a real person working for the scammer immediately uses your username and password to attempt to sign in to the real service.
- Since you’re protected by two-factor authentication (good for you!), the scammer gets a page requesting your two-factor code.
- They then cause an identical page to be displayed to you.
- You enter your two-factor code.
- They capture the two-factor code and immediately enter it into their attempt to sign in.
- Done quickly enough, they sign in to your account and wreak havoc, possibly changing your password and preventing you from accessing the account thereafter.
- Your attempt to sign in on the fake sign-in page fails.
Once again, the scammer relies on fooling you into thinking something is official when it’s not. In this case, instead of an official-sounding phone call, it’s an official-looking webpage. And again, they contacted you.
It’s phishing, pure and simple.
Postscript
As I was writing this article, I got a scam phone call related to my Amazon account, which went to voicemail. Instead of following their instructions, I just went to Amazon.com, signed into my account normally, and looked for any issues or unexpected orders (that’s the scam: claiming a suspicious order on your account). All was well, and I returned here to add this postscript.
Do this
Never, ever use two-factor codes for anything other than signing in or confirming your identity when you’re making account changes. The only place you should enter these codes is online to the service they’re associated with. Never, ever give them to anyone else, even if they claim to be from the service.
Consider not answering your phone for numbers you don’t recognize.
Be alert when getting notifications via email. Rather than clicking the link in the email, go to the service’s website yourself and look for issues. If you do click the link, make absolutely certain that you’ve landed on a page controlled by the service and not a scammer.
Above all, be skeptical.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.







The bottom line: If they call you, it’s a scam.
No company will ever call or email about suspicious activity. I’ve gotten several legitimate emails about suspicious activity. Mainly the “We’ve detected new activity on your account, in or near {my approximate location}. If that was you, please ignore this message. if it wasn’t you, please contact us at {web link}” All I’ve gotten were legit, but to be sure, never click on a link. It is the email equivalent of don’t trust a phone call from a company.
Go directly to that company’s website if you aren’t sure.
The bottom line: If they ***contact*** you, it’s a scam.
Newer versions of the scam have been reported where they contact you via Social Media messaging (Facebook, X/Twitter, etc.), Text, direct website chat, email or other means that appear at first blush to be official communications with proper logos, etc. Closer inspection will generally reveal inconsistencies and/or spelling and gramatical errors.
Had to do some financial transaction at the bank. In the past, I’d insert my card and enter the PIN for identification. Now, I show them my ID and they send 2FA to my phone which I need to verbally tell them.
I have my phone set up such that notifications pop up without me having to unlock my phone. So technically, if someone impersonates me at the bank and has my phone in toast.
I wonder if my Android phone has a setting to disable popups if phone is not at home or on my person?
google calls me with a one use code to sign into my Gmail.
they tell me not to share this code with anyone else, if its a one use code, even if i did share it with anyone else, its one use is over when i signed in.
not to mention i never commit a one use code to memory. once i enter it to sign in i hang up the phone and its gone. i couldn`t share it if i wanted to.
Replying to Mark Jacobs, decades ago Discover credit card called me because of a suspicious purchase. Apparently the purchase was so expensive they had a voice interaction with the buyer, and when they called the land line number on my account to confirm, the Discover employee realized the voice on my answering machine message was unlike the buyer. I called back, and confirmed I hadn’t made the purchase. Discover issued me a new card with a new number. They may have changed their security practices in the decades since, of course.
I once had my credit card company phone to inform me of any transactions over a certain amount, but it was an opt-in feature. So there are some exceptions. This is a kind of second factor authentication for credit card transactions. In this case, the caller isn’t telling you do do anything. All they want is a yes or no as to whether the transaction is legitimate.
The smallest amount I coud set for notifications was $100. I phoned my bank and the were able to set the trigger amount for notifications to $1. Now, I get a text for every credit card or online transaction.
If I have to use a one time security code sent to my email or telephone why do I need a D password?
Sooo, soon we will be facing three or more security hoops to jump through. You have to love the US, government and big businesses can waste more time and money than sand in the Sahara.
It’s two factor authentication. If only a one-time password were required, it would only be one factor,