A couple of days ago, Google researcher Travis Ormandy made the following statement on Twitter:
I think @natashenka and I just discovered the worst Windows remote code exec in recent memory. This is crazy bad. Report on the way.
Turns out it wasn’t Windows, per se, but Windows Defender (and Microsoft Security Essentials, in prior Windows versions). And “crazy bad” is apt.
It set into motion an example of “the system” working, and working well, to keep you safe.
The Windows Defender bug
While the details of the bug are naturally complex1, the bottom line is very, very simple: if an attacker managed to get a maliciously-crafted file onto your machine, a Windows Defender scan of that file could be exploited in such a way as to allow what’s called “privilege escalation” and “remote code execution”.
In English: the act of downloading a malicious file could allow an attacker unfettered access to your machine.
In scarier English: files are being downloaded all the time. For example, the simple act of downloading your email or opening a web page causes files to be downloaded to your machine. Unlike normal situations where you need to take action to get infected, you don’t need to see, access, read, or open the email or file; its mere presence is enough.
Protecting yourself
The solution is simple: ensure that Windows, and in particular, Windows Defender (or Microsoft Security Essentials), is up to date. Make sure automatic updates are on2 or visit Windows Update in Control Panel and “Check for Updates”.
As long as you’re updated, the threat has passed.
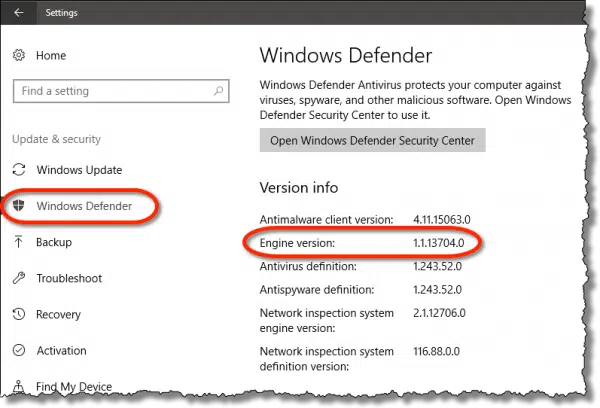
To confirm you have the latest updates in Windows 10, open the Settings app, click on Update & Security, and then Windows Defender in the left-hand column. Scroll down until you see “Engine version”.
In Microsoft Security Essentials, this information is present in the Help -> About dialog.
As long as the Engine version is 1.1.13704.0 or later, you’re protected.
So. What happened?
What went wrong?
Very simply, Windows Defender had a bug.
I don’t want to minimize the importance of that bug, or its discovery, but I do want to make an important point:
All software has bugs. No exceptions.
Software is incredibly complex — much more complex than people realize. Bugs — mistakes — are a fact of life. While everything is done to minimize the number of bugs, and the impact of bugs, the fact is that bugs happen.
This isn’t limited to Defender; it’s true of every anti-malware tool. This isn’t limited to Microsoft; it’s true of every software provider.
And every so often, the bug that’s discovered has an impact that’s big, bad, ugly, and scary.
What matters most is what happens next.
What went right?
Google researcher Travis Ormandy is a member of Google’s Project Zero. His job is to look for zero-day vulnerabilities in the software used by … well, by just about anyone.
On May 5th, 2017, he succeeded3, finding a bug in Windows Defender.
Responsible disclosure
Using what’s referred to as a “responsible disclosure” protocol, Microsoft was informed. Quoting the case:
This bug is subject to a 90 day disclosure deadline. After 90 days elapse or a patch has been made broadly available, the bug report will become visible to the public.
The concept is simple: the vulnerability is kept secret to keep it out of the hands of malware authors until it’s been fixed. A 90-day limit is put on that secrecy to act as a strong incentive for the software vendor to provide a fix for the issue.
Microsoft moved significantly faster than 90 days.
A fast fix
In what may be record time, the Windows Defender team made a fix available in less than 72 hours.
For an organization as large as Microsoft, a product as complex as an anti-malware tool, the sheer number of flavors of Windows (versions, editions, and languages), and particularly with the pressure of knowing the immense scope of the confirmed vulnerability, this is absolutely amazing.
An automated update
I’m sure that one of the motivations for the fast turn-around was to get the fix folded into the already-scheduled “second Tuesday” round of Windows updates.
As I said, there’s a good chance that many people will have been updated and protected against this potential threat before they even realize it exists.
That’s exactly how the system is supposed to work.
My recommendation
My base recommendation for Windows Defender isn’t changing. For most people, it’s quite enough.
If anything, Microsoft’s response has only served to solidify my opinion. As I said, bugs happen, and something like this can happen to any software, including any anti-malware tool. What matters is the response — and the response was exactly as it should be.
It also solidifies my recommendation that you leave automatic updates for Windows Update turned on. This removes any dependence on you even being aware of a problem before it’s fixed.
Again, exactly as it should be.
I’m sure that some will be spooked by this event. That’s also understandable. If that’s you, my only recommendation in this case is that you take the time to research and select a reputable replacement, in the hopes that when they have an issue, their response will be as professional.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!


Nice explanation, Leo. Based on your recommendation a while ago, I decided to go with Windows Defender on my custom-built rig over a year ago. Thus far, no regrets.
Well done Leo; as always thanks for your use of a broad brush when explaining operating system security in terms intelligeble to the layman. On my desktop PC running Win 10, I’ve been using McAfee antivirus because the suite is included for all the computers in my home from At&t (my ISP). I also run Malwarebytes about once a week. Should Windows Defender be run in parallel or in place of these other software products?
By design, if you’re running another anti-virus program (e.g. McAfee), Windows Defender will detect it and will turn itself off. Malwarebytes can safely co-exist with Windows Defender.
p.s. For most of my customers, I recommend, and personally prefer, Windows Defender over the major security suites (e.g. McAfee, Norton, Kaspersky, etc.). It has a smaller “footprint” (less impact on the host windows), less issues, and is free. (Most ISPs that provide security pgms such as McAfee actually charge a fee. Not unusual to see a small monthly surcharge — $4.95 or so — included in the ISP’s Internet access bill.)
Windows Defender will likely not run in the presence of another anti-malware tool like McAfee. You should have only one running at a time.
Along with this although on a slightly different issue, MS has just issued a patch for XP, Vista, Server 2003, concerning the WannaCry and Wanna Crypt ransomware making the rounds, KB4012598.
Kudos to them.
This is a bit off topic, but to me it highlights the benefits of using Windows Defender/Security Essentials. A work colleague has a computer which was running so slow, it was in its death throes. I uninstalled Avira and enabled Defender. The computer immediately came back to life. Sometimes Defender is the only AV which doesn’t cripplingly slow a computer down.
If you have Microsoft Updates turned off will MSE still updates its virus definitions?
No. Make sure Windows Update is turned on.
I have Windows 7 update set to notify me but not download or install. (I am rigorous about updating though.) I noticed that MS Security Essentials updated without me doing anything. It also regularly (every day) gets a new signature file which gets installed with no intervention on my part. So my conclusion is that MSE is not constrained by the settings you might have made for updating.
That would be a good decision on Microsoft’s part, but I don’t believe they do. Updating your AV is not just good advice. It’s essential to security. For myself, I feel the same way about Windows updates. I have Windows 10 Pro, so I can turn them off if I chose, but with so many vulnerabilities being discovered, I’ll risk the possible discomfort of something breaking. Instead of delaying an update, I have a nightly incremental backup to roll back to in case an update messes things up.
The Creators’ Edition did mess up my computer, but when I was powering down to restore from my backup, Windows said it was going to update before powering down. When it restarted the bug was fixed and I didn’t have to roll back.
My understanding is the opposite: MSE relies on Windows Update. Especially in this case the update was not a simple definition update, but an actual update of Windows Defender itself – I would be surprised if that didn’t require Windows Update to be running.
Lesson: don’t turn off Windows Update. Please.
I have to say, I do run Windows Defender/Security Essentials AND also Malwarebytes. and BOTH have caught something one time or another.
Malwarebytes pops right up and tells me what it is, if the page is safe and so on. It is set to auto-quarantine anything it finds.
Best of all for me, I have the lifetime version, which has all the bells & whistles. It was free for a while, now one must purchase it, But
well worth the money.
Just my 2 cents worth……
Keep up the good work Leo, Have fun in Alaska……
Nice article, and I know you’re a fan of Windows Defender and prefer it to paid for protection. But the fact is this security hole was not present on ESET, AVG and other protection products. And I don’t think this is the first time. People have been affected and fixing it later is not a solution for those already affected. I work in this area myself.
Windows Defender is weak. I would not be promoting is as a security solution to either individuals or companies.
All software has bugs and vulnerabilities. It’s just as likely that the problem could happen to any of those other products.
All I can say is that when — not if — security holes are found in those other products that they’ll respond as quickly.
Some products are not protected I was so very sad pls help me how to back all my lost data..someone attack my accounts & the most sadly thing I join a binary options I don’t have my data someone hack it