It’s important to make sure.
The last question is easy to answer: yes.
Yes, you absolutely should keep Windows as up to date as possible. (This article focuses on Windows 10 and 11.)
I know there are those who disagree. Some go so far as to seek out ways to prevent Windows from updating itself.
Let’s look at why they feel that way, and what I believe you should do.

Keeping Windows up to date
Windows Update automatically makes sure Windows is as up to date and secure as possible. You can mitigate any perceived risks with regular backups, but letting Windows Update do its job automatically and regularly is a key component to keeping your computer safe from malware and other threats.
Vulnerabilities & updates
The issue is common to all software: nothing is perfect. All software has bugs, period, no exceptions.1
While many bugs are inconsequential, some make the software vulnerable to exploitation by people trying to do something bad, like hack into your system, steal your data, use your computer to send spam, or worse. These bugs are often referred to as vulnerabilities, and the software taking advantage of them is termed malicious software, or malware for short.
When vulnerabilities are found, manufacturers release updates to their software that fix (or patch) the bug.
It’s important that users of affected software install those updates when they’re made available.
Unfortunately, some individuals do not install updates for a variety of reasons. This leaves their computers vulnerable to more and more malware, even though the associated bugs the malware can exploit have been fixed.
Help keep it going by becoming a Patron.
Automating updates
Windows Update is Microsoft’s solution to update distribution and installation.
It runs in the background, periodically checking for updates to Windows2 that apply to your machine’s particular configuration. When available updates are found, Windows Update downloads and installs them automatically.
It’s not uncommon for updates to require your machine to be rebooted. Software cannot be updated if it’s in use. That means in order to update core components of Windows itself, Windows needs to shut down briefly. That’s a reboot.
Updates & failures
I said earlier that all software has bugs.
Updates are no exception. They are software, so they could have bugs. The update process itself could have bugs.
The net result is from time to time, or perhaps from person to person, Windows Updates are sometimes considered risky. There’s a perception that with any update, there’s a risk your machine could become less stable. In the worst cases, Windows updates have completely crashed the machine on which they’ve been installed.
That bad reputation — warranted or not — has had serious long-term consequences.
Perception and reality
Windows 10 is installed on close to, if not over, a billion machines world-wide. That means when there’s even a hint of a problem, it makes headlines everywhere. The size or scope of the problem is immaterial to the headline writers; every failure is treated as a big deal, if not a disaster.
To be fair, even if one tenth of one percent of all Windows 10 machines suffered a failure due to Windows Update, that’s still a million machines. That’s a lot.
And yet, everything else being equal,3 you run only a 1 in 1,000 chance of having a problem.
Still, because of headlines and reputation, some users delay updates to what they consider a safer time — a few days or weeks later. In some cases, they try not to take updates at all.
Malware authors approve. To them, delaying or skipping updates means once a vulnerability is discovered, they can continue to write and circulate malware to exploit it, because they know not everyone will take the update to fix it. If you pay attention to notifications of large data breaches in the news and dig deep enough, you’ll often find that hackers gained access via a vulnerability for which a patch had been made available but had not yet been applied.
Applying updates regularly remains the best approach to keeping your system secure and up to date. I continue to recommend you let Windows update itself automatically, so you don’t have to take any action at all.
Forced automated updates and your options
Windows 10 originally had no option to delay updates in its consumer (“Home”) editions. Updates were downloaded and installed automatically.
In a perfect world, this would be a perfect solution. Unfortunately, we do not live in a perfect world.
There have been two major issues:
- While the stability of Windows updates have improved over time — fewer and fewer updates cause significant problems — some Windows 10 updates, at least initially, seemed a step backwards. Reports of people having problems after an update seemed to increase.
- Updates requiring a reboot would indeed reboot, often at an inconvenient time.
The stability of updates appears to be improving once again, and Microsoft has made additional options available.
In Settings, Windows Update, you’ll find an option to “Pause updates for 7 days.”
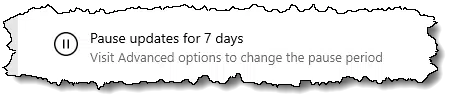
This is particularly useful if your computer usage is about to be particularly sensitive or important; you know you won’t be impacted by an update.
Similarly, Microsoft added the concept of active hours.
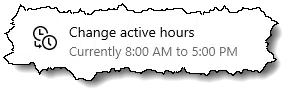
This allows you to tell Windows Update when you normally use your computer. It will not reboot the computer during this time.
In Advanced Options, you’ll find the following options.
- “Show a notification when your PC requires a restart to finish updating.” This allows you to control when your machine will reboot, allowing you to save your work and make sure nothing will be negatively impacted by the reboot.
- An option to pause updates. This is the same as the setting above, but allows you to pause updates for up to 35 days if need be.
The bottom line is that Microsoft really, really, REALLY wants you to keep your machine as up to date as possible.
And so do I.
Managing risk
It’s all about risk management: trading the risk of a misbehaving update to the risk of having an unpatched vulnerability exploited by malware.
The good news is, we know how to manage risk.
For all versions of Windows, my recommendation remains:
- Back up regularly. Ideally, perform system image backups as I’ve outlined in several articles. Then you’re protected from any kind of failure, be it hardware failure, a crashed disk, malware, or even a troublesome Windows update.
- Configure Windows to notify you when a restart is required, and restart as soon as is practical. This places the restart and its impact completely under your control.
- Don’t delay updates if you don’t have to, and if you do, choose the smallest length of time you can. This minimizes the length of time you leave your machine exposed to known vulnerabilities.
- Don’t try to disable Windows Update. It’s critical to your safety.
In my opinion, this is the safest approach to managing a wide variety of risks related to using your computer — not just the risks of a failed update.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!
Podcast audio
Footnotes & References
1: If someone claims a particular bit of software has no bugs, then either they haven’t yet found the bugs, or they’ve dismissed some erroneous or unexpected behavior (aka a bug) as not rising to the level of being called a bug. It’s still a bug.
2: And optionally, other Microsoft software.
3: With no specific characteristics to refine the number, it’s 1 in 1,000. However, it often becomes quickly apparent that a failure applies to certain machines, or certain characteristics of machines, meaning you can much more accurately judge the risk you actually face. Typically, you have even less risk than 1 in 1,000.




My question is simply this. When I scan Windows XP (home edition) with Spybot SSD, I get a report indicating that a threat “Windows Security Center.AntiVirusDisableNotify” has been detected and fixed. Would this problem prevent me from getting the most recent Windows updates?
When trying to get updates I always get zero found .
Thank you,
Ted …
Maybe.
I would: run the system file checker http://ask-leo.com/what_is_the_system_file_checker_and_how_do_i_run_it.html, get and run an up-to-date anti virus package http://ask-leo.com/viruses_how_do_i_keep_myself_safe_from_viruses.html, and get an additional anti-spyware program and run that too http://ask-leo.com/spyware_how_do_i_remove_and_avoid_spyware.html
I’ve been reading through the INTERNET trying to find a solution to this problem – “Could not start the Automatic Updates service on Local Computer. Error 1058: The service cannot be started, either because it is disabled or has no enabled devices associated with it.” I’m running Windows XP Professional with SP2 – I had SP3 when this started and removed it. I’ve been all over the web and tried all the re-start solutions I could find. I am at my witt’s end. Please help.
Steve
smajero@msn.com
> Microsoft on occasion automatically downloads AND installs updates even with this setting
IIRC, this is true, but limited to security problems *with Windows Update itself*, in which case a lot of normal mechanisms are bypassed.
IMO this is understandable, and in context, perfectly acceptable.
Why? Well, if you have a problem with as OS vendor doing things to your computer that you don’t explicitly know about, then to be honest you have way bigger problems than an occasional mandatory update — you’re using a proprietary OS, it’s doing things you don’t know about all the time. If you consider that unacceptable, then Windows is not the OS for you; use an open source one. On the other hand if you do consider it acceptable, mandatory updates don’t really change anything.
But choosing to run a proprietary OS and then being paranoid about the OS vendor updating it is just silly.
On my XP I have Windows Update turned off.
I understand that Microsoft releases updates on Tuesday.
By Friday Microsoft has fixed all the bugs in the updates that third party testers have reported.
On Friday afternoon I go to Windows Update and only download the high priority updates.
Windows update is only the appetizer. Avoiding updates to other popular applications is just as dangerous as not having anti-virus software.
Secunia’s PSI is very complete, but its also complex and wants to run constantly in the background.
They also offer a simpler online product, one that doesn’t have to be installed at all – the OSI or Online Software Inspector. For an intro to that service see
Free, Comprehensive Windows Patch Notification: Secunia
It requires Java and it doesn’t check as many applications as PSI. But, with the 80/20 rule, its probably good enough. My experience has been that it’s hard enough to get a clean bill of health from OSI.
The Windows 7 option about allowing all users to install bug fixes (excuse me, “changes”) means that a standard/restricted Windows 7 user can install patches without any UAC interruption. If this is off, then a standard user needs to supply an admin password to install patches.
Windows Update, in Automatic Mode, does not always load all of the critical updates.
It seems that some of the Updates require a more recent Windows Genuine Authorization check before they will download & install. Also, Service Packs will not install automatically.
A recent laptop with Vista did not have any SPs installed. It took about four hours to download and install these over a wireless cable-based ISP connection.
Personally, I turn Windows (Microsoft) Update off, and run it manually. Otherwise, it runs automatically at bootup – and hogs resources – and I’d rather have a working PC faster. I don’t mind being out of date for a week or two if I get lazy with these updates.
Now my antivirus – that is the only program I allow for automatic updates.
Great website Leo – thanks as always!
Automatic updates reserve 10% of internet bandwidth.
My college teacher informed me Microsoft reserves 10% of your bandwith and it is better to use the Windows update from all programs once a week on Thursday. Windows releases proper updates weekly and you do not get hot fixes. The weekly updates are full update and not hot fixes. A pc with hotfixes is not all that good, the fixes are often not correct and you are sent another hot fix to any errors. We were advised to turn off automatic updates and to ensure you manually install all updates either from Windows Update link or search Microsoft and download and install manually from the downloads.
Hope I was informed correctly and this helps to clear the pros and cons of automatic updates
17-Dec-2009
For getting windows updates from command line, see http://www.wuinstall.com
You can turn off automatic updates and get the updates when you want them, via command line
There is an argument to update vulnerable software QUICKLY which Leo didn’t stress particularly but which is very important. I want to give it here, because for years, I did fall myself in the trap because I didn’t know it.
Indeed, an argument *not* to be in a hurry to update, is the following (and it is a fallacy but it is not evident): “given that I have been running this piece of vulnerable software/system now for 2 years without any problems, what’s the hurry now to do it right away ? If I do an update every 6 months or so, that will be good enough, right ? I’m not more vulnerable today than I was 6 months ago, right ?”
In fact, you soon will be. The argument above sounds good but is flawed, for the following reason. Once a vulnerability is known, it is made public 45 days after it has been reported, usually with “demonstration software” that shows how to abuse the vulnerability to hack the computer that is vulnerable. So from the moment that someone (honest) found the vulnerability (and in order to demonstrate that it IS a vulnerability, one has to use it to demonstrate the problem of course) and informs the software distributor of it, the counter is set in: 45 days and ALL BAD GUYS will learn about it, and most often, exactly how to use it. One can be surprised by such a ‘ criminal policy ‘ but in fact, there are strong arguments that this is indeed the safest way to report vulnerabilities, no matter how strange it may sound that one sets free code of how to attack systems.
But this means that a vulnerability that has been dormant in code, eventually for years, is hopefully not, and in the worst case, known only to a handful of hackers ; however, from the moment that it is “officially discovered and reported”, a counter starts, and 45 days later, ALL HACKERS IN THE WORLD are informed how to abuse it. So the software distributor should fix it within 45 days, and you should install it within 45 days, to be safe.
Vulnerabilities aren’t necessarily disclosed after 45 days, or even at all. Each company has its own disclosure policy. Additionally CERT will extend – or sometimes shorten – the 45-day window in the case of vulnerabilities that are serious or being actively exploited.
All that matters is that the hacker community knows it, by some means. Once that happens, everyone is immediately at risk.
I was talking of course about “officially announced” vulnerabilities (mainly by security researchers) to instances like CERT. The disclosure policy is meant to find a compromise between leaving some time to patch it, and “putting the cards on the table”, so that 1) yes, hackers know about it, but 2) also all people that might be exposed to the vulnerability know exactly what risk they are exposed to (and can eventually decide to stop running the vulnerable software until patched), and 3) put software writers under pressure to *really* patch it.
History has shown that “secretly informing the software provider” – especially if it is propriety software – has often led to no action at all, pretending there’s no problem (preserving “good name”) or giving out an ineffective patch. Now that’s of course worse.
Next, a funny comment to wrap your mind around:
as zero-day vulnerabilities (they are called zero-day because the 45-day counter has not been set in: in other words, “not yet officially announced vulnerabilities”), which are the juice of hacking:
1) cost a lot of effort and work to find
2) are very valuable to people wanting to hack into systems (mostly state-sponsored intelligence agencies and law enforcement, next to organised hacker crime)
it is somewhat silly to put out for free those vulnerabilities, while rich entities are willing to pay you a lot of money to get them exclusively so that they can exploit them without people knowing or the software provider patching it. There is already a market for vulnerabilities. Now, in order to protect the economic activity of vulnerability searchers, one could do something similar as what one does to protect the economic activity of software writers.
In the same spirit as the laws that protect intellectual property, in fact, there should be a kind of Digital Millennium Vulnerability Act that grants the right to knowledge of vulnerabilities to those finding and/or buying them, and nobody should have the right to tell it to others, or to spread the word, or to install patches that are not licensed for good money to the hacker that bought the intellectual rights to them. Only the owner of the vulnerability right has the right to inform people about the patch. Anybody getting a licence of a “vulnerability information” agrees on a VEULA (Vulnerability End User License Agreement) not to disclose this information to anyone (not even to his family members).
In other words, in order to obtain the right to install a patch against a propriety vulnerability bought by a hacker, you should first buy a license from that hacker 🙂 But even to *learn* about their existence in some detail from any other person but the license holder would by “vulnerability piracy”. It should then be totally illegal to *inform* people of vulnerabilities, as this knowledge is intellectual property. There should be institutions who analyse internet traffic and try to find out who is guilty of the act of piracy of informing others about a vulnerability that is licensed.
This is nothing else but applying the logic of intellectual property rights consistently into the domain of vulnerabilities, and illustrates the sickness of the principle in my eyes.
“Honestly, it’s all about risk management, trading off the risk of a misbehaving update compared to the risk of having an unpatched vulnerability exploited by malware.” – Agreed. The bottom line is that the changes Microsoft has made to WU will result in more PCs being more secure – and that’s good news for everybody.
Let us say that this is a nice side effect of Microsoft using most free (beer) users of Win-10 as guinea pigs / beta testers for the paying customers with enterprise licenses 🙂
Otherwise there would be no reason to allow enterprise licenses to be more “insecure” than free (beer) licenses.
That’s a very cynical viewpoint 😛 The simply fact is that Microsoft either force updates on people, or we have bigger and bigger botnets – consisting of unpatched consumer systems – pushing out spam and other unpleasant stuff in a bigger and bigger quantities. And, of course, there are very good practical reasons why the update process needs to be handled in the enterprise space – and having us act as beta testers for them isn’t one of those reasons!
Updates can be delayed in win 10 by selecting “metered connection”. Updates will be automatically downloaded and installed next time an unmetered connection is available.
I guess I’m an exception, but automatic updates became a nightmare on Windows 7, and I just do not do them any more. I’m not unaware of security; I have a paid subscription to ESET NOD32 antivirus and frequently run Malwarebytes and Spybot S&D. Microsoft has to show me that they are not doing more harm than good.
You’re not an exception. Many people do that. Problem is that it’s not a good idea at all. It’s better to fix the update if it’s causing problems. I’ll point you at this article: https://askleo.com/fix-windows-update/
Back again Leo, with an update observation/ question regarding Windows 10 updates. I have a group of seven seniors using new Windows 10 laptops (out of the box with W10). Three have been stymied by an update removing their task bar, including the menu icon. For your average user this is dead end. Using shortcut keys I’ve been able to get to system restore and start the process. None has run to completion, but upon subsequent power off/on cycle, they came back in some form off usability, from which we could recover. This has occurred over a three week window, yet I’m not finding much online help. Were these folks not in this group, this would be a $100 repair action at the local merchant providing service. So the question part is: How do you keep these folks running when Microsoft keeps breaking their machines? Sure back-ups are nice, but most users are not gurus, but rather ordinary people trying to use a tool. Roger
“Sure back-ups are nice, but most users are not gurus, but rather ordinary people trying to use a tool.” – Many seniors are, of course, able to deal with backups perfectly well – Leo, for example 😛 Like anybody else, the seniors may need some help with the initial setup, but managing things on an ongoing basis likely isn’t be beyond their capabilities.
That said, in a situation such as this, I’d have probably opted for Chromebooks (unless there was a specific need for Windows-based systems, of course). Chromebooks are just as easy to use as Windows PCs, considerably cheaper, less susceptible to user-caused or update-related problems and, because they’re designed to be used with Google’s cloud services, you don’t need to worry about backing ’em up.
Wait … did I just get called a “senior”? 🙂 Not that I mind, it’s just that I suspect most people’s definition of “senior” changes as they get … um … older. I’m 58, fwiw.
That being said, I know a ton of seniors (let’s say 80’s and above) who are quite adept with their technology and backing up. I bristle (to steal someone else’s term) when people try to use age as an excuse.
OK…I am eligible to respond to these remarks :-)….I will be 81 on Saturday…fit and well, play Picleball 3 x’s a week for about 4 hours and never get tired. Healthy diet most of my life, and don’t know what I would do without the internet.
I also want to add how grateful I am to you and this site, because one does not have to be computer savvy to understand your writings, which really helps those of us who are self taught. When I think I need to contact the Geeks…I check here first. I love the challenge of trying by myself first though till I get frustrated, and then things change.
Blessing to you all
Gloria
The big snag with Windows 10 forced updates is that even if you can identify an update that causes a problem, yes, you can uninstall it but … whilst the problem may go away short-term, with the next update check, Windows discovers that you don’t have that update and puts it back again.
You can block specific updates quite easily:
https://support.microsoft.com/en-us/kb/3073930
You are right about Microsoft Updates. With Windows 7 winding down it’s extended support from Microsoft, there is no incentive for Microsoft to distiguish between Windows 10, 8.1, 8, 7 updates when they download updates. Your machine might not have any reason to apply the updates they suggest, thus making your machine run more sluggishly. I click the “more information” link and review the update they suggest, then decide if I want to download it. It saves a lot of aggravation. For example, “kb/3035583-Update installs Get Windows 10 app in Windows 8.1 and Windows 7 SP1” and who needs that if they’re happy with Windows 7? I do try to keep Windows Defender up to date even though I run stronger Security programs. Thank you for your articles.
W10 shut down my computer as part of an update.
It was not a good time as i was fighting for my life in Dying Light.
Zombies attacking me and more coming as i fought, ran, climbed for my life.
I was NOT happy.
Got W8 and W7 set to update normaly on a shut down and they are no bother.
I never get any updates applied because, I guess, I am on a metered connection with Hughes Net satellite internet. So I can run my Windows 10 computer with all vulnerabilities just waiting for a hacker to use. I never use more than 10-20 % of my allocated service so I would like to tell MS that I am metered but install the updates anyway. Any way to do this???? Because of this I never bring my W10 machine up. What a waste. On my Vista machine, which I use for everything, every time I bring it up I update my AV, and if MS updates are flagged I install them. All done over my metered connection with never a problem. It’s a screwed up mess. Any suggestions will be appreciated.
Why not set your connection- at least temporarily – as non-metered?
How safe is Chrome in storing passwords and personal information?
Not very. It’s much safer to use a secure password manager like LastPass.
I recently fixed my old Samsung laptop and I have been trying to update windows 7, however it continuously says to shutdown in order to install updates. I do this, but when i log back on it states the same thing with no update. I would really love to get this old laptop running again. any info would be a great help
Perhaps info in this article will help: https://askleo.com/fix-windows-update/
Although I always keep Windows Update active, from time to time I still find Updates that haven’t installed or failed to install on my three machines and find the same on some of my friends’ PCs that I give help from time to time. Therefore, I do a manual Update from time to time just to be sure.
Two Windows updates have blocked access to all my Word and Excel files: KB4462223 and KB2553332. Luckily I kept a record of the numbers of all the files that were to be downloaded and installed so that i could identify the culprit among the group in “Add/Remove Programs” and delete it. I now download each update file individually and test the results to insure that it is not malevolent. Of course, “update” keeps trying to download the malefactors. If I allow the computer to download and install the entire group at once and there is one malefactor, I have no way of knowing which one it is. I am still running XP; could this be the problem?
I just ask how can I know if the notification (at the bottom right hand corner of Windows 10) is genuinely from Microsoft? Reading through this page, just waste my time! Microsoft is really getting idiotic these days!
With the automatic updates of Windows-10 on my three years old Lenovo Laptop, “This PC” does not show its CD?DVD Drive, although it is detected by the “rescue CD” of the “Image Backup/Restore” .
Its manufacturer, Lenovo, referred me to their authorized Repair Store”, who contacted Microsoft as they are “Microsoft Partners” and they gave the shop a solution but it does not stay till after a Restore and Start after Shutdown. Microsoft acknowledges that this is after a Windows-10 update, but never give even an estimate on when they will fix it PERMANENTLY by a Windows-10 Update.
A solution was to get the computer start as it was new, although this will remove all its saved data and Apps, but as there were several updates since then, the automatic Windows-10 Updates, are not with an automatic shut down after each, allowing to check if the problem is there after such update or not, and then remove the then installed Windows Update…And the problem after that is how after removing the offending Windows Update, prevent further newer updates?
The existing as got from Lenovo CD?DVD drive, worked perfectly on other computers. Trying other CD/DVD drives on my Laptop, did not work as they did not show up under “This PC”..
As a longtime reader of Ask Leo!, I’d hope you have a system image backup from before the update to roll back to. If not, take a system image backup now. Reinstall Windows from scratch, restore you programs from the backup, reinstall all of your programs from their original installation files, and start performing regular system image backups, preferably with daily incremental backups.
Sorry Marco, you can’t stop the updates and you can’t know if you’re getting a bad update until it has already done its damage. You also don’t seek assistance from Microsoft for any problems with Windows (that’s the last place to get help from). About Mark’s advice: That’s not an answer to your question. Even if you have an older backup image and you restore that, you can’t stop a bad new update from overwriting it and causing the same problem again. Given that you are asking this question in the first place, and you had to go to a computer shop to resolve your problem, you’re likely to render your computer inoperative by an image installation – so be careful. To delay a Windows update will depend on your version of Windows 10 and you’ll need to do some serious online research to try all the many, many different suggestions people have for delaying a Windows 10 update. Some people even claim that they know how to stop a Windows 10 update. But there is no guarantee that any of the delay/stop approaches will actually work. To avoid update surprises, don’t leave your computer on all the time. Turn it off when not in use or disable the network connection.
Never (and I mean, never) be in a hurry to install a Windows 10 update. Don’t worry, nothing horrible will happen. If possible, delay the update for as long as possible until you can research online to see if there are any reported problems. Microsoft uses its customers to debug updates, so let others be the guinea pigs. A Windows update is like a new vaccine – it takes time to get it right and someone is bound to get sick from it.
Unfortunately, you’ll never know if the next Windows update has fixed your CD/DVD problem. You’ll just have to allow the update and hope it works – and hope it hasn’t broken something else. Here is where Mark’s advice comes into play. Before an update you need to have an image backup to go back to in case of a bad update. Leo has lots of articles on this backup topic.
As for the computer shop that gave you a one-time solution. Go back and ask for your money back or a permanent fix. If all they can do is a one-time fix, they need to teach you what they did so you can do it yourself.
Hi Leo
I just wonder why the following comments are up to 15 years old
and mainly for Windows XP, after your header is for Windows 10?
Many thanks
Allan
“40 comments on “How Do I Make Sure Windows 10 is Up to Date?”
“Ted McQuaid
December 27, 2005 at 5:34 am
My question is simply this. When I scan Windows XP (home edition) with Spybot SSD, I get a report indicating that a threat “Windows Security Center.AntiVirusDisableNotify” has been detected and fixed. Would this problem prevent me from getting the most recent Windows updates?
When trying to get updates I always get zero found .
Thank you,
Ted” …
This article was written for XP and updated to apply to Windows 10.
As it says at the end of the article.
“Posted: October 22, 2020 in: Windows Update
This is a major update to an article originally posted 2004”
Just discovered askleo.com and have subscribed.
I have a 2018 Dell that serves me well for what I do: gmail correspondence and Social Media, with an occasional Word or Excel doc. Now that all support – and automatic updates – has been discontinued for Windows 10, is it really necessary for me to upgrade to Windows 11? While my machine can handle it, I do not want to go through all the revising of the appearances of the various programs (mainly toolbars I’ve customized) as I had to do when my company upgraded to Windows 11. It was a real pain. Is there any danger in not upgrading?
You want this article: How to Keep Using Windows 10 Safely after Support Ends
If your computer is capable of running Windows 11, it’s a good idea to upgrade. The interface is a little different from Windows 10, but it doesn’t take long to get used to. In fact, I find the Windows Start Menu cleaner and easier to customize than WIndows 10.
You can use Windows 10 relatively safely, but using a supported OS is safer.
And from what you’ve said, everything you use your computer for can be done with Linux.