Be careful not to give away more than you expect.

To begin with, good on you — not only for your donation, but for thinking to clean it before you do so.
All too frequently, we hear of computers being donated by banks, hospitals, or other institutions that end up exposing all sorts of private information that should have been erased first.
The best way? Well . . . how paranoid are you?

Wiping a hard disk before disposal
In most situations, a simple full (non-quick) format of a traditional hard disk is sufficient. For advanced situations, full disk encryption can be used. SSDs should be erased using a utility with the SSD-specific “ATA Secure Erase” command. For the extra paranoid, physical destruction is also an option. What’s not an option is leaving an operating system installed, as that will inevitably leave personal traces as well.
Not an option: leaving anything
Quite often, I get this question with an additional caveat: how to remove all of your personal information while leaving Windows installed.
You can’t.
Even after removing all of your data — even if you remember to remove every scrap, and even after removing every single application — some of your personal information will still be left behind.
There’s likely to be random information left in the Windows registry. On top of that, unless you take additional steps, all of those files you carefully deleted could possibly be recovered.
What’s worse, of course, are the people that do nothing and leave everything on the machine. It’s not uncommon to hear stories of second-hand machines containing a wealth of personal and private information from the previous user.
Let’s not do that, OK?
Basic precaution: format the HDD
When it comes to hard disk drives (HDDs), conventional wisdom is that reformatting your disk is the right thing to do. And I agree with that if it’s done properly. (I’ll discuss solid state drives, or SSDs, below.)
What do I mean by properly?
Windows (all versions), and even MS-DOS before it, has the option to perform what’s called a “quick format.” In reality, a quick format does very little except create an empty top-level directory and possibly add a label. The rest of the disk is left alone. That’s why it’s quick.
That’s why it’s also insecure. Because the rest of the disk is left untouched, any data that was there will remain. Many disk recovery tools will be able to recover data from a “quickly” formatted disk.
So the answer is to reformat the disk, making sure to not specify a “quick” format.
Unfortunately, if that’s your C: drive, you won’t be able to format the drive if you’ve booted from it and are running Windows. You’ll need to either install the disk in a different machine to be able to reformat it, or boot from something else.
However, there’s another approach that could work just as well.
Encrypt the disk and throw away the key
This feels counter-intuitive, but it’s actually a very secure approach.
Full-disk encryption securely scrambles all the information on the physical disk such that it can only be read if the decryption key is provided. So, encrypt the disk and lose the key.
There’s one caveat: if you’re given a choice whether to encrypt only the files, or the entire disk, always choose the entire disk. This will secure everything, even those deleted files that could otherwise be recovered.
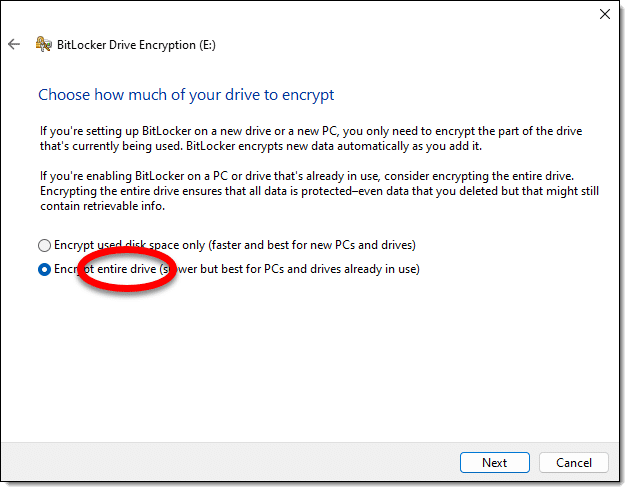
If you encrypt a non-system disk (meaning a second disk drive in your machine, or an external drive), BitLocker will ask for a password. Perfect. Forget the password, don’t save the recovery key, and the disk is as good as completely wiped.
System disks — the drive on which Windows lives — are a little more complicated. You can certainly BitLocker encrypt the drive, but it will remain bootable, and anyone with access to your account credentials could conceivably sign in and see/recover the data.
There are two approaches for your system disk:
- Remove the drive, place it in an external USB enclosure, and use BitLocker encryption as described above.
- Use the option in the Reset this PC to remove everything and wipe the data. (Article coming.)
SSDs are different
Unlike HDDs, SSDs wear out the more you write to them. The techniques mentioned above — a not-quick format or using BitLocker– write to the entire drive. While it probably won’t appreciably impact the useful life of the device, there are better alternatives for SSDs. Most involve a special command called “ATA Secure Erase”. It’s the least impactful way to erase an SSD completely and securely.
- Check with the SSD manufacturer. Many, if not most, have free maintenance utilities that include the secure erase command as an option.
- Use Windows Disk Manager to remove all the partitions on the drive. Technically, this isn’t a complete erase or overwrite, but it does make any attempt at data recovery much more difficult. And it’s free.
- Use a third-party utility like PartedMagic. Unfortunately, most are not free, but in exchange, they often include additional partition-management functions that could be useful in other situations. Be sure to look for “ATA Secure Erase” (specifically for SSDs) functionality.
The important thing is to avoid treating your SSD like an HDD, and avoid a full over-write if you can.
Over the top: physical destruction
It’s a common recommendation to use a big heavy magnet to erase a hard disk.
Don’t.
Any magnets you’re likely to have around the house, even your big speaker magnets, are unlikely to affect your hard disk in any significant way. I believe there have been studies that show even some exceptionally large magnets still leave the contents of hard disks in a recoverable state.
Another approach to really, positively, and permanently destroy your data is to physically destroy the disk.
Personally, encryption is more than enough for me, but if you care enough to go this far, perhaps drill a few holes all the way through the hard drive casing, through the disk platters, and out the other side.
Unfortunately, that level of destruction also makes your gift significantly less useful.
If you want to leave Windows on the machine…
As I said before, it’s common to want to leave Windows installed as part of your gift.
That may or may not be legal (it depends on the terms of the license for your particular copy of Windows). To keep it at least ethical, it means you would no longer keep or use that copy of Windows yourself.
The right and safe way to transfer Windows, in this case, is to, after wiping the drive, reinstall Windows from scratch using your original installation media. If your system didn’t come with installation media, then you could try the restore media that you received, or you could restore to an image backup that you took immediately after receiving the machine and before adding any of your own programs or data. You can also download an appropriate copy of Windows.
Part of your gift would be to include the product key activating that copy of Windows, which you would no longer use yourself, having given it away. For Windows 10 and 11 the digital activation should be associated with the machine and you won’t need the product key.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!




Yes, there are various utilities out there that will do varying degrees of data “wiping” to help decrease the chances that the data can be recovered. And if an unconditional Format isn’t enough for you, then they might be worth checking out. But remember that there are few guarantees … they only decrease the probability of recovery, not neccessarily eliminate it. Format takes care of the 99% case … the rest of you need to decide how much trouble you want to take.
If you want to erase your hard disk, simply throw it into an incinerator. That way, theres no freakin way thanyone will ever get to your stuff.
oh yeah!!
My sister inlaw gave me her comp. but it has a virus on it that i cant get rid of. I was wondering if i could erase or reformat my hardrive to reinstall WindowsXP without the hard drive still having the virus on it. Im not to sure what kind of virus it is, but im pretty sure its some kind of spyware or adware.Your comments would greatly be appreciated
I think reformatting and reinstalling is a great way to start clean. Make sure to install anti-virus and anti-spyware software right away. A couple of articles that may help:
http://ask-leo.com/how_do_i_keep_my_computer_safe_on_the_internet.html
http://ask-leo.com/how_do_i_set_up_my_computer_simply.html
I’ve used the Web-deployable EraseYourHardDrive.com and found it to be an efficient and effective method of conducting a three-time disk overwrite and verification pass. The software automatically produces a Certificate of Data Erasure – guaranteeing success of hard drive erasure. I tried three off-the-shelf data recovery programs and could find no trace of data. I liked the fact that the software was Web-deployable so that I could erase the drive immediately and did not have to download an .exe file nor did I have to wait for a CD to arrive in the mail. Quick, convenient and obviously effective.
I format hard disk by command (format c:/q/u/s)
after that i loss my data can you suggest me any process for recovery data
That’s what formating does … it erases your disk.
You can try googling for “unformat”, and you may find some tools that can help, but I would not be hopefull.
at the risk of looking like i didn’t read the above comments (I did)…I gave away the desktop monitor years ago and kept my compaq hard drive out of fear of data security…it was purchased in ’99 and has a very old Windows on it…there’s no chance of buying or using any of the cleaning software – so are you saying the rumor of strong magnets won’t work? I live in an apt, I’mnot about to be drilling into anything…HELP! Anyone know of companies that come take away and clean hard drives???someone once said tat HP had a day when people could drop off old machines but I’ve never seen it advertized. What can a paranoid do with an old drive lying around the apt that htey are dying to ditch???
Here is one possibility,
Put the HDD into a working computer (perhaps the one it was originally installed in).
Use BitLocker to encrypt the hard drive.
Format the HDD with the quick option unchecked.
Install Windows.
Encrypt the HDD with BitLocker.
Format the HDD with the quick option unchecked (again)
The HDD should now be as unrecoverable as possible. The first BitLocker encryption encrypts all the data on the drive, and stores a key there as well. Formatting the drive removes all the data on the drive
After re-installing Windows, then re-encrypting the drive with BitLocker, a new key is stored on the drive (replacing the original one). Re-formatting the drive a second time removes all data on the drive. At this point, even if someone is determined enough to recover any data on the drive, the best they will be able to do will be to recover the dearth of data from the re-installation of Windows, then re-encrypting the HDD. Since the original encryption key is no longer accessible (it was overwritten by the second BitLocker encryption), any data that may be recoverable will be encrypted, and meaningless. This is a lot of work, and will take a considerable amount of time, but I believe the result is very secure.
My2Cents,
Ernie
Yeah, a strong magnet won’t. It’s pretty amazing, really – I’ve seen some interesting examples on TV of things that you would expect to be demagnetized by a high powered magnet that just keep on working.
It depends on how paranoid you are about the old data. Putting the drive into a machine and simply performing an unconditional format would be enough for most. Otherwise, anything that you can do to destroy the disk physically (open the case, bend the platters, whatever) would be the near-ultimate.
I want to agree with leo it is all about how paranoid you are. If you know that you have something on there you shouldn’t. Or are worried about someone finding it out. Then my advice is just get a 5 puond sledge hammer from home depot and beat the living crap out of it on the side walk. However if you just want to donate a computer. Get partition magic 8 and delete the partitions and recreate them, then use a 98 boot disc to format the drive and format it 5 times in a row. If anyone can recover your data after that, they worked hard enough for it I say let them have it. In all seriousness most people don’t know how to access the data on their computer that wasn’t erased. So don’t freak out I am the lead PC Tech for a Circuit City located in Countryside,IL. You would be amazed at how little the average person knows. Data Retrieval is not even in there vocabulary. So format it or smash it if you are that worried, Otherwise you could leave everything on there and for the most part no one would find anything anyways.
Just my opinion, I could be wrong
Paul
PC Tech
Both ‘DriveScrubber’ and ‘KillDisk’ have functional demos for download- the file you download creates a bootable floppy disk that will overwrite the entire surface of whatever drive you choose-erasing data, partitions, etc. You would then have to create and format a new partition. It would take special hardware to retrieve any data after that. Takes about 2-1/2 minutes per GB on an average HD/machine.
IBM has a free (Anyone can download and use it) software program that you can download from their website called “IBM(R) Secure Data Disposal (SDD) Version 1.2.”. It runs from a boot disk/CD, and a will wipe out your drive by copying, sectory by sector, track by track, random data onto the hard drive. It will overwrite everything that is there, as many times as you want. So there would be no chance of someone every reading what was on your disk drive.
Caveat – doesn’t work with RAID systems very well, since it needs drivers to read them.
Bill Tkach
System Administrator
I would recommend using a Overwriting software.
That’s what Leo should have mention is Erase a hard drive using a Boot-Up Hard Drive Erasing Software (like Active Killdisk, etc etc.), erase it Guttmann method, then erase it with other methods, then when your done you erase with One Pass Zeros so it looks like you never erased, or written data.
Then after that Reformat, then install the Operating System (95,98,XP,2000,2003,Vista) not to mention you overwite when you reinstall your Operating System too.
Now you know how to erase everything without destroying the hard drive. I need to have a data erasing service. Maybe computer repair shops can have a erasing service and make some $$$.
Another way to destroy data from recovery is to put all data in a (Strong 128-Bit) or more encrypted container and reformat-it because you can recover files but never destroyed strong encrypted files from a deleted encrypted container. That’s the reason why Strong Cryptology is Banned in certain countries.
Don’t use magnets, don’t destroy you Hard drive. It’s not nessisary.
I inadvertently formatted my hard drive with the system rescue disk. THE GEEK SQUAD assures me they can have all my photos and videos rescued by a level three retrieval.
A level 2 is $500, but a level three in a clean room is $1500. I this even possible, or am I getting ripped off?
There is an Open Source, Free utility named TestDisk. It comes with the System Rescue disk image. You can get it from https://www.system-rescue.org/. This is also a free tool, and it has saved my bacon many times (I experiment a LOT). TestDisk can recover (aka unformat) data from a formatted HDD.
The System Rescue disk image (.iso file) can be burned to a CD, DVD, or a USB drive (using rufus – yet another free utility 🙂 ). Then re-boot the computer from the System Rescue live image, and (from the command line), start TestDisk. Follow the prompts, and you may be able to recover your stuff. If you have not tried to use the drive since formatting it, you should be able to recover all your formatted-over partitions.
This is a daunting task, and you will need access to another computer to get the System Rescue disk image, and put it onto a CD or USB stick, then re-boot the formatted computer with the System Rescue disk you just created, but with a lot of patience, time, and a bit of luck, you should be able to recover (un-format) your hard drive.
I hope this helps,
Ernie
My request to format the hard drive is met with “Format cannot run because the volume is in use by another porcess” I have nothing else open or running. Any idea why I am getting this response?
You have Windows running – windows has the volume in use.
What about tools designed to permanently erase files from hard drive? There’s no mention of them here.
I believe those are roughly equivalent to the multiple-format option mentioned in the article.
DBAN (Darik’s Boot and Nuke) is a free, easy to use tool, that performs hard drive wipes up to DoD (Department of Defense) specifications. It’s similar to the technique used to destroy data on computers that store secret defense information. Just run the boot disk builder utility, stick the disk in the drive of the computer in question, reboot and follow the on screen instructions. You can download it here … dban.sourceforge.net
for wiping your hard drive data… you can Stellar Wipe – An advanced safe data eraser.
Download the software from here
http://www.stellarinfo.com/file-eraser.htm
It’s free for 30 days…
Give a try.. it is a wonderful software
Here’s some advice on using geek squad if you’re computer literate enough to be posting and reading comments on this web site. Don’t. And as for their use of “clean rooms”, most of their techs don’t even bother with discharging electricity.
I read your comment about a large magnet not being effective at erasing a hard drive. I have one of those “lift an outboard motor” magnets. I was hoping it would erase a notebook drive I have to return to H.P. because it failed. Because it had failed I was unable to use a program to erase it. I obviously can’t damage it because they want it back (or I pay for a new one – even though the in-warranty replacement they sent was apparently used (scratched). I have a lot of pesonnal info on it so I’ll try the magnet anyway – and hope for the best.
Thank you,
what is about the DD command, so far as i know this is safe as well, isn’t it ?
e.q.
dd if=/dev/null of=/dev/hda
With regards to using magnets to erase your files. Even if you have a powerful degausser, if you want to give the drive away or have it usable afterwards, don’t use a magnet. The manufacturer stores important data on the disk for the drive itself to function. Erasing that will render the drive unusable.
Also, it takes a strong magnetic field inside the drive to actually erase the data on the disk. Even magnets that you or I consider very strong typically don’t project the magnetic field strongly enough far away from it’s surface. And by far away, I mean about half an inch.
Empty your trash bin and the space will then show up on your pie chart. When you delete something, it doesn’t free up your space until you empty the recycle bin.
Emptying the trash only removes the addresses of the files in the trash. The files remain on the hard drive just as they were. This is why recovery programs can recover ‘deleted’ files. Also, bits and pieces of files may be left behind in the sectors used by new files.
Emptying the trash is a superficial method of making files disappear from the folders and their space available for storing new data.
True deletion of the data is the purpose of this web page and making deleted data unrecoverable by anyone.
In MS DOS mode i typed in FORMAT/U and it says “required prameter missing-” what now?
Gina, the parameter missing is the drive letter.
Example: format c: /u
quote”what is about the DD command, “
if you’re using dd, it’d be better to use urandom rather than null as you input file and do it a few of times
Here is what I do, to delete my Ex: nakedPic.jpg: Before deleting it, I look for an innocent picture like: tree.jpg and I rename it nakedPic.jpg.The system tell me that that name already exist and if I want to replace it. I click yes. Now, if I open nakedPic.jpg, I will see a tree instead of my wife’s naked body. Now I delete it. If somebody recover this picture, all they see is a tree. No trace of other picture. You can replace an important doc,txt,jpg,mp3,… for a insignificant doc,txt,jpg,mp3,… save it and delete it after.
I think that you should reconsider your technique. All you do is change the pointer of the file name, you do not overwrite any existing data. Eventually new data might overwrite some or all of that file.
After deleting that newly named file, it and the first file still are on your hard drive since the OS does not overwrite data when it deletes the address in the directory, it only deletes the directory entry. Both files can be recovered unless their data has been overwritten.
—–BEGIN PGP SIGNED MESSAGE—–
Hash: SHA1
For the record, it’s quite possible to reconstruct the
original picture even after you’ve “deleted” it the way you
describe. The actual data on the hard disk has not been
erased by your actions. It’s not easy to recover, but to
someone dedicated enough to the task it might be.
Leo
—–BEGIN PGP SIGNATURE—–
Version: GnuPG v1.4.7 (MingW32)
iD8DBQFHlp5rCMEe9B/8oqERAunBAKCCqxyB9I8ig4FhQMxzcTSsdEHLoQCbBMGd
BtaAr2D1skB6j/IUxX7autU=
=DewF
—–END PGP SIGNATURE—–
I tried to run format c:/u and it’s asking me for the volume label for drive c but I do not know what that is. How do I find it?
The Volume Label they are asking for is the new label you want to give to the volume, not the existing one.
—–BEGIN PGP SIGNED MESSAGE—–
Hash: SHA1
Before you do the format do a “Dir C:” – the result will
start with something like this:
Volume in drive C is XXXXXX
where XXXXXX is replaced by the volume label for that drive.
Leo
—–BEGIN PGP SIGNATURE—–
Version: GnuPG v1.4.7 (MingW32)
iD8DBQFHp+LpCMEe9B/8oqERAj7UAJ0WZLxDMmQ/D2PYowMK2dlprYA+PACePUgU
btQOHOR7QDLWwdck+JCPzf8=
=spPv
—–END PGP SIGNATURE—–
Drilling right through the disk will completely kill the entire drive correct?
—–BEGIN PGP SIGNED MESSAGE—–
Hash: SHA1
Yes and no. But 99.99999% yes 🙂
The “problem” is that seriously advanced, expensive and time
consuming techniques could, perhaps, recover data everywhere
there’s not a hole in the disk platters. It’s HIGHLY
UNLIKELY – more like the stuff of spy movies and bad TV
shows – but remotely possible.
For all practical purposes, though, drilling a few holes
works just great. 🙂
Leo
—–BEGIN PGP SIGNATURE—–
Version: GnuPG v1.4.7 (MingW32)
iD8DBQFHrzCoCMEe9B/8oqERAvJzAJ49LdoRfN5Lof5ryogsxhuGwJOs2wCgiTXv
Aqq6AqPNusoJbOAwAqkyWWg=
=U/D0
—–END PGP SIGNATURE—–
It’s easy to securely erase your hard drive. First, simply perform an erase on the entire drive (no need to really erase anything – just makes the allocation table identify everything as unused space) then copy other information that you don’t care about onto the drive until it is full). And the simplest way to do this, is to copy very large files, I would recommend movie files (ATI, WMV, MPG etc etc) and you can even copy the same file many times provided you give it a different name, otherwise it will just keep overwriting the same disk space. If you are still paranoid, then do this
(1) do a full, low-level format
(2) fill the disk up with junk
(3) do another full, low-level format
Please add WipeDrive you list. http://www.wipedrive.com
Know & learn more about wipping the Hard drive
http://www.eraseharddrivedata.com
tried “format/c” – the system cannot find the path speicified – now what
—–BEGIN PGP SIGNED MESSAGE—–
Hash: SHA1
There’s a space between format and /c.
Leo
—–BEGIN PGP SIGNATURE—–
Version: GnuPG v1.4.7 (MingW32)
iD8DBQFIQ2czCMEe9B/8oqERAieFAJ9nStFM6p1gojY38HuquDd3N/RPIACeIknR
QFvw1jUqms5cK+HhalRN1Wo=
=KL41
—–END PGP SIGNATURE—–
very nice article about how to erase your hard drive permanently. formatting can erase disk but not permanently as you said data recovery software recover these files. SO in this situation you could try drive wipe software which rewrite and overwrite the data by special algorithm so that it couldn’t be recovered by any recovery software.
More information: http://www.drive-wipe.com
Look for DBAN… by far the best nuke program I’ve ever seen. I don’t know anyone that’s been able to recover data off a DBAN’d drive. And trust me, I know “social engineering” people who do it all the time on weak reformats.
—–BEGIN PGP SIGNED MESSAGE—–
Hash: SHA1
DBAN is Darik’s Boot and Nuke available at
http://dban.sourceforge.net/ – and yes, it’s another good
solution.
Leo
—–BEGIN PGP SIGNATURE—–
Version: GnuPG v1.4.7 (MingW32)
iD8DBQFIS17QCMEe9B/8oqERAhAIAJ9IGqq07FyUC8WVPpdMCQLAiOrwgQCfWM/0
OWGaJrKs/z1l7ZCSL4JY/6I=
=1ajY
—–END PGP SIGNATURE—–
can I ask a question. I had a new hard drive with new bios put in. If I erase the HD will the BIOS be left so I can reinstall the OS.
Thanks
—–BEGIN PGP SIGNED MESSAGE—–
Hash: SHA1
Erasing your hard disk does NOT erase your BIOS.
Leo
—–BEGIN PGP SIGNATURE—–
Version: GnuPG v1.4.7 (MingW32)
iD8DBQFITLFlCMEe9B/8oqERAhFRAJ9y3NuoBYxOlcPHe5lmL66mn8uDVQCfXxQv
/5HrFQO+WSA1ml+UV9sTqcg=
=i1HT
—–END PGP SIGNATURE—–
What about encrypting the data? then I would think it could (in many cases) become an impossible task to decrypt the data, from the partly recovered data you get from the drive.
Specifically I think if you used whole drive encryption from day one on the drive you might be ok.
But if you’re suggesting to encrypt just prior to disposal, I’d just format instead. Or break out my drill press. 🙂
-Leo
>Amanda Stephen:
>can I ask a question. I had a new hard drive with >new bios put in. If I erase the HD will the BIOS >be left so I can reinstall the OS.
The Bios isn’t saved on the hard drive. It’s normally saved on a chip on your motherboard. This chip can be overwritten or in some cases physically replaced. Without a bios a normal PC is useless, because is can’t load an operating system and thereby can’t be operated 😉
Why erasing hard drive is required ?
Get your answer here…
http://www.eraseharddrivedata.com/wiping-hard-drive-process.php
To erase the data on my old hard drives, I strip out the hard drive from the computer and then use a screwdriver to open the hard-drive case. I then light up my acetylene torch and cook the actual platter.
Within a few moments, it’s melted and virtually destroyed. I can’t believe for a second that any data is still there.
I also have a giant magnet that weighs about 20 pounds. I’ve often wondered what might happen if I put it in contact with the platter.
(BTW: Tim’s a friend, and posts less destructive home-improvement tips over at Ask The Builder.)
10-Dec-2008
DBAN works well but has limits too.. here is a good versus article. DBAN Versus Wipedrive
I have gone to c: and put in “format/u”. It keeps telling me I have wrong or missing parameters… Please help I am trying to erase a hard drive so that I may give the computer to someone else. Thanks
19-Jan-2009
Does formatting the hard-drive during reinstallation of the operating system via the original CD (vista or XP) adequately erase the HD
06-Feb-2009
Hi! I have a failing external hard drive that I want to give to a local computer recycling center. I want to do this safely and I’m wondering if I can use a bulk eraser – the kind that radio stations used to use to erase reels of audio tape? Thanks.
17-Mar-2009
I would advise degaussing the drive. After all it is a magnetic storage device. Had a quick google read more here…
http://www.pureplanetrecycling.co.uk/data-destruction.htm
12-Jun-2009
Try using WipeDrive – software which erases all data on your storage devices.
Dear Leo,
Great info here about wiping a drive. I’ve got two older HP laptops I’d like to sell, but they don’t work, so I have to either sell ’em without the HD, or wipe the drives by other means. I have access to some huge magnets (think “MRI”)and I’ll do it that way. I know it might not be enough, and I know that I won’t even be able to know that, but I’ll take the risk (I’m not too paranoid)
My question: Assuming I can successfully scramble the drive, should that drive be able to be reformated by the new owner?
Thanks!
Ed
Now that I have erased my HDD how do I get the new OS to install?
When I insert the Windows or Linux install disc, it gives disc error and will not load. I have used a partition floppy to install a MBR partition but the OS will not start.
I am trying to wipe my hard drive as i have a worm and my comp is shutting down every half hour or so i tried to format it and reboot from windows disc but nothing works i have tried webroot washer also but nothing seems to boot when i switch on can you help please
Formatting Doesn’t Erase the Data,it can still be recovered.Use a Program called “Dban” which Overwrites the data with Random data several times…rendering it USELESS!!!
It’s an Iso Image file,so you have to get a free program like “BurnAware” and burn the file to a Cd-r or Dvd-r.And boot it from System Start up.
This goes to Jeff,the System might be too infected to just format,you might want to wipe the drive all together and then try to re-install Windows.
Dban
http://sourceforge.net/projects/dban/files/dban-beta/dban-beta.2007042900/dban-beta.2007042900_i386.zip/download
If you want to be sure of total data loss, disassemble the hard drive, remove and destroy the discs.
WHEN I TrY TO FORMAT THE HARD DRIVE, I GET A Message that” says format cannot run because the volume is in use by another process , format may run if this volume is dismounted first, would you like to force a dismount” Then “cannot lock the drive volume is still in use”
Formatting and deleting the data from the hard drive does not removes the data completely from the hard drive. It can be recovered easily using any recovery software, so removing the data in that manner will not be safe.
So, to remove the data completely from the hard disk any special softwre is required and Wipe Mac is simply perfect which I used as well. It removes the data at changes the hard disk format in its native state that is to 0 and 1. I am sure it will help you out as well.
ya i would use dban’s boot and nuke which will render anything that was on on the hard drive useless and plus all u have to do is put it on a disk boot off the disk confirm that you really wana get rid of everything and let it do its thing
Just write zeros to the disk. Takes a long time but it’s worth it, WD has a utilty that can accomplish this. http://support.wdc.com/product/download.asp?groupid=609&sid=3&lang=en
i have a laptop that the screen is broken on. i want to erase the hard drive, but cant see anything to do it. i used to work at a drs office that has an MRI, if i have them put it in the room while its one will it do the trick? if so, how long should it be in there and how close? thanx!
22-May-2010
maybe you can see what’s running by connecting the vga port on side or rear of laptop to old display.
Long-time fan, first time caller . ..
If you are looking to erase and recycle your laptop, we offer a free and secure service at http://www.EraseMyLaptop.com
Please support our goal of keeping laptops and smartphones out of landfills. Our goal is to be sure your personal information is completely erased in the process.
Thanks for the great article and many years of excellent computer advice Leo, you are a legend!
Yeah it is very imp to delete all the sensitive data b4 u get rid of ur hard drive.The simplest way to do this is by formattng the drive…but that too may not delete all the data and there are always chances to recover them.I can suggest you 1 tool that will remove all ur data permanently forever and no other tool can also be able to recover it.Advanced System Optimizer…there is this tool named Secure Delete in ASO that does the permanent deletion of the data…but be cautious once the data removed can not be recovered anyhow.
its free version is also available at cnet
I had reformatted a hard drive for someone and reinstalled windows xp. Then my friend tells me his wife wanted music and pictures on it. I could not retrieve them. So, after some researching I bought a program for $70.00 called Power Data Recovery that retrieved all formatted data to an external hard drive as long as the original data was not rewritten over. I was able to retrieve all her pictures and music. Then I burned them all to 2 DVD’s for her (or it would have been like 6 cdr’s). So,yes, it is possible with the right tools to retrieve data unless it is completely rewritten over with a data destroying program.
i do’n undersand clearly that is WipeDrive is ?
I removed the hard drive, the mother board is fried, what can be discovered on the RAM?
We are selling it with full disclosure. We figure the buyers want the parts, screen, etc. We were suprised that anyone wants this stuff, but happy to keep it out of a landfill.
20-Nov-2010
While I enjoy taking power tools to my redundant electronics (who doesn’t?!), I can recommend this company’s Data Destruction services for anyone who needs it done in a more sustainable fashion.
Jim
its is very easy to recover data even after it is format. most secure way is to download a software which provide complete delete.
Formatting a drive will NOT I repeat will NOT destroy files on the drive even if it is an unconditional format.
The proper way is to overwrite each and every sector on the drive with random data. Once is enough for all but perhaps an intelligence agency to recover BUT there is a defense department method that uses rewriting seven times with different data that will ensure even the NSA won’t be able to do it.
A free software that does all of the above is available here:
http://eraser.heidi.ie/
I am NOT an expert it’s just a hobby to me.
A fellow brought is hard drive to me and said I could have it if I did a complete format infront of him. I did the complete format then overwrote it with a large Linux OS then formatted it again then overwrote it with a different OS then formatted it again. Then I installed an OS system on it so I don’t think anybody is going anything off that thing. Besides nobody knows where the thing is. Not even me, It’s in somebody’s computer and I don’t keep track of that stuff. Poor mans method. lol. PS. Make sure you overwrite the WHOLE hard drive.
Just Reinstall windows
03-May-2011
If you are *really* concerned, a secure way to do this would be to encrypt it before reformatting it. This will make it impossible to recover the information. This is what I would do:
1. install truecrypt from http://www.truecrypt.org/
2. encrypt your entire hard drive using twofish, Serpent and AES and a 65 character password
3. use a strong password like this: NGeiiyQvCzUkgbDUhH@MKorEgD&j%$XHNDJlSKxN!Q#ZhGGBLg$vfrRPTxAu#a&xn
4. reformat the hard drive
5. burn piece of paper you wrote the password on
I know that is overkill but if you are concerned with the data being recovered after holes are drilled in it, this should technically be more secure.
i think you would have to run the encryption app from a liveboot OS (liveUsb, LiveCD, etc) or booting an OS from another drive.
However, i suspect encrypting the whole target drive costs a larger processing expense than writing random data over the whole target drive.
I also think that technically, encryption produces data that possesses a pattern (some meaning, in the philosophical sense). And even large ‘key’ and ‘password’ is finitely crackable.
Writing random data produces data that is patternless (meaningless) in its essence.
Comparing… random write-over seems cheaper and more effective.
If you want to really destroy the information, you dissasemble the HD, take out the disks, and pass some sand paper on them…
What about using fdisk? does win 95+ (98-win 8) still have it> Will that work (not as good as drill press) but still work than reformat?
I used to use Fdisk then format then install whatever I could and do it again about 3 times then just fdisk and install the basic OS.
Below is a list of the best and completely free Hard drive wiping software available today
http://www.comtips.net/free-data-sanitization-software.html
To know more about how to erase hard drive easily, go here http://how-what.blogspot.com/2011/11/how-to-erase-hard-drive-how-to-erase.html
It goes without saying (okay, it _should_ go without saying, but I’ll say it anyway), but…
If you don’t have original install media, see if you can make an install/recovery set of media _before_ you nuke the drive. In fact, even if you _do_ have media, see if there is a way to make an additional set.
Also, if it’s not printed on the side of the computer (and sometimes Windows has been upgraded to a version other than the one on the sticker), you should use a utility such as Belarc Advisor — http://www.belarc.com/ — which can tell you the key for not only Windows itself, but most applications you have installed. Again, once you’ve nuked the drive, this information is gone.
Finally, make sure you have backups of anything you might want to keep and/or move to a new computer.
I have donated many PC’s/laptops over the years and my philosophy is this, simply remove your drive and install a NEW one! Hard drives are cheap. Maybe not so much for laptop drives depending on the size. But for piece of mind it’s well worth the added expense. I also would like to think that what I donate is not merely a worn out piece of junk but a machine that someone can rely on for a reasonable amount of time. One last point regarding computer donations and perhaps the most important. Know who you are donating to so you know your donation is not just being resold for profit. Especially in the case of laptops! We started a program at my church to recycle computers and I was stunned at the number of machines which started coming in. We started out with several of us getting together once a month to go through the machines. However there were so many we couldn’t keep up. So we recruited the youth groups to help. It gives these kids hands on hardware experience and they also teach us old farts a thing or two. It has been a very rewarding experience and everybody wins!
On a paranoia scale of 1 to 5, you’re a 5 if you overwrite the entire drive several times, then disassemble it, saw the platters into several pieces, and discard the pieces one every month over a large geographic area so they’re not all in the same landfill.
I am a 2 on that paranoia scale. I use a run-from-cd version of linux to erase the data.
>dd if=/dev/zero of=/dev/xxx bs=1M
(xxx represents the drive id, usually sda but not always.)
This leaves the drive more empty than when it was shipped from the factory, but the manufacturer’s low-level drive info (like the serial number) is still there and the drive is formattable and usable. Theoretically, data could be recovered from the drive using hi-tech sophisticated forensics, but not by the average computer user or even a tech-geek like me, and the folks who could do it wouldn’t waste their time recovering my data.
The way Leo writes it, “DBAN will automatically and completely delete the contents of any hard disk that it detects.”, once you boot from your DBAN CD, it will erase every hard drive on your system! Let’s hope he doesn’t mean this, and that DBAN asks you which drive to erase. Meantime, though, I would not yet dare to try DBAN. As a constructive further comment, if you have replaced (say) a flakey C-drive, and want to erase it after replacing it with a new one, put the old drive in a USB enclosure (e.g. NexStar-CX, about $50) and (assuming DBAN lets you select the drive) erase it in there.
14-Dec-2011
Why not use Secure Erase instead? It’s built into almost every contemporary ATA drive and thus, significantly faster as well, since it’s the drive doing the work, not the CPU.
http://cmrr.ucsd.edu/people/Hughes/SecureErase.shtml
I want to donate my old computer,I used Gutton eraser and it ran for 48 hours. I was told that it also erased the windows vista ,and it wouldn’t be any good.And i don’t have the windows cd.would that be true.I thought you could use a pc monitor with any cpu My knowledge of computer is limited,so not sure if the man was telling me the truth.
AFAIK, on most big brand computers, Vista and later has a “run once” program to backup Windows (of the the new computer) to 2 or 3 DVDs.
Normally, at any time, you can restore Windows from a “recovery partition”.
If you wiped the whole drive, you wiped the recovery partition too.
@Anice
Certainly seems likely that the eraser program deleted everything off the disk, including the operating system. It’s unfortunate that you do not have the re-installation media. The computer is still good though. It’s just that the new owner will have to get an operating system going on it, and find any necessary drivers.
One thing that many people do is install a non-microsoft operating system in a case like this. Ubuntu is a good choice. So go ahead and give away the computer, and refer them to this article on Ask Leo!
should I convert to Linux?
7 years ago after buying a new HP notebook the drive died after just 6 months. The people at HP talked me through trouble shooting the drive and decided it had died, and sent me a new drive, free. I only needed to return the dead drive. Not being able to format the drive, I took a strong magnet and sat it on the drive for several hours. I don’t know if this worked, but it was the best solution I could come up with.
@Ken
That magnet probably did nothing, but if you haven’t had any problems 7 years later you’re probably OK. HP probably immediately destroyed the drive pretty quickly anyway. It’s unlikely they would go to the expense of trying to recover the data as it would have no value to them. Sometimes, unfortunately, we’re forced to trust the people who fix our computers. Our data is exposed whenever we bring our computer to a tech for repairs. If you have sensitive data you might want to think about using Truecrypt. Otherwise, after the fact, as Leo said, drilling through the drive may be our best alternative.
Do you know if a degaussing coil has sufficient strength to erase date on a hard drive? I worked in TV repair years ago and used this regularly to degauss(or rearrange) the magnetic properties of
old CRTs? I am looking for a quick fix obviously, but this may determine whether I donate or recycle. Thanks!
11-Feb-2012
I’m looking to sell an alienware computer, which has the hard drive formatted for RAID (I’m still not entirely sure what this means). Anyway, I tried to use Dban and RAID hard drives aren’t supported. I’ve already used my alienware respawn disks just to get the ball rolling. How can I completely erase all my personal information and get by this unsupported Dban problem?
@Michael
It’s probably too late now but you need to open the BIOS and change the SATA mode to IDE then erase each disk. You can then change it back to RAID in the BIOS to reinstall using recovery disk or system image but you may need to recreate the RAID.
Can anyone help me urgently? I had some sensitive data in pendrive, that i have overwritten now but i am scared by the recovery tools that pretend to recover even overwritten data. So should i also use Dban?? I am giving pendrive to someone, please help me. If i only want to use Dban for USB flash drive, not for hard disk, would it work?? Please answere my few questions , i want to wipe pendrive permanently so that nothing can be recovered.
@Rihana
Dban isn’t for wiping a pen drive. Dban nukes all of the drives attached to your computer, so it would also wipe out your hard drive. A good program for wiping an external drive such as a pen drive is CCleaner. On CCleaner’s tool menu there is a function to wipe an entire drive.
Ask Leo! article on CCleaner
ErAce is good software to shred hard drive to meet even strict security standards. It can be found free from erace.it
Does Leo have thoughts on the SAFE approach: 1) Encrypt, then 2) Secure Erase
http://windowssecrets.com/top-story/rethinking-the-process-of-hard-drive-sanitizing/ ?
It’s easy to overlook that encrypting needs to be done from day 1 – meaning that sensitive data should always have been encrypted. It’s unclear whether taking a drive that is 100% full of sensitive unencrypted data, and then encrypting it all before securely erasing would actually sidestep the problem. Also worth noting that traditional magnetic hard drives don’t have this issue. A traditional multi-pass wipe should work. Encryption of course adds an additional layer of security. (And it’s pretty bizarre that SSDs do what they do – I’m still not sure I totally “get” it.)
And finally, for most people a standard secure wipe will do. Unless someone is taking forensic tools to your data it’s rarely an issue as long as you just format or wipe the drive, even once.
Nothing said about cost, if you have to be licened to do , or if it’s a subscription deal .
I need to return a faulty laptop for refund in next few days. It is only 3 mths old and recently had motherboard replaced. The only sensitive data would be some passwords. Should I wipe the HD? If I do, will I be liable for any charges if I leave no OS. I do not have any disks so wouldnt be able to reinstall windows and not sure I would know how.
Depends on the sensitivity of those passwords. If it were me, I’d wipe it.
Why the article says it’s “Posted: December 9, 2011” but yet there are comments from 2004?
Because the article also includes this line: “(This is an update to an article originally published December 24, 2004.)”
I have used low cost ErAce. It lets you to determine overwrite times. And works on any Windows computers. It also works on SATA, IDE, SCSI, USB drives
Hello Leo,
My name is Victor, 45 y/o, Portuguese. Don’t know if you have anything published about flash drives security. I would like to know your opinion (if you have one) on this. I work with very sensitive info and I’m always afraid that if I lose any of my pen drives, falls in competition hands and they find my password… I’m (sort to speak) doomed….
I’m thinking to purchase the “Ironkey D80” that seems to be… if the access fails it automatically overwrite the full existing content. The reason of my contact is because I’m not too sure that this will be so effective as they say and would like to know if you have any option about this or can recommend better solution. I apologize if you already have a thread posted about this, if this is the case I’ll be happy to receive the link.
Thank you for your attention,
Kindest regards,
Victor Oliveira
11.30.2014
17H17 GMT
You can use a program like AxCrypt or TrueCrypt to encrypt the files:
https://askleo.com/how-do-i-password-protect-a-flash-drive/
http://ask-leo.com/how_do_i_encrypt_a_file.html
Hi Mark,
Thank you for lhe indo. I’ll check both links.
Regards,
Vic
And make sure you have the contents backed up. I would assuming that losing your only copy would be just as disastrous. Flash drives often fail.
Hello Connie,
Thank you for your reply.
Indeed, all contents are kept safe in the company. I just would like to be sure that if I lose any of those pens whoever find it (and assuming) wants to know the content inside have a sort of “mission impossible”, despite I know that there are always somebody capable to crack it even only getting few % of it…
At least I’ll try to difficult that task in case it happens. Thank you.
Kindest regards,
Vic
please sir i need the answer now. what happens to a DVD disk drive when when its content is erased and replaced with another
That content is erased and replaced with another. Not sure what you’re looking for – the question is very vague.
I took the hard drive out of my HP laptop computer. I want to do this because before I donate the laptop. Will some get it and put in a hard drive and see my files? The computer crashed so I cannot delete anything at this time.
Thank you
Your files are on the hard drive, so there is no way anyone can access them if the hard drive is gone. However, do keep in mind that if you give the computer away without a hard drive or operating system it is not much use to the person you are giving it to. They might not want it then. So you should explore a few different options before moving forward.
Hello ok I didn’t see this question I apologize if it was there. I need to deep clean my lenovo y430 laptop it came with vista installed is there anyway I can do this and keep vista on there? I am not giving it away or getting rid of it so it doesn’t have to be wiped yet but alot of programs on it and its slower than molasses.
It depends on what you mean by “deep clean”. You can try a repair reinstall, but a true deep clean means a real reinstall which would wipe everything and you’d need to reinstall all your programs.
This is topic that recently became of interest to me when a 2TB drive from my RAID array went bad (lots of bad sectors). I tried reformatting, but that failed, so I realized the drive was in bad shape. I tried running DBAN, but it estimated over 2.5 YEARS to do a one pass erase. Another drive of same size from my array started showing signs of trouble, so I ran DBAN on that one and in 26 hours it made 7 passes. So, here I was with a drive I cannot format or erase because it is just too far gone. What to do? I started investigating options regarding using magnets and degaussing equipment and found this was an area ripe with confusion. Degaussing equipment certified to DoD standards to perform the job costs thousands of dollars. However, I did find three permanent magnetic wands that were certified by NSA to meet DoD standards. I wondered how they were approved given all the information stating that this type of degaussing is not possible for permanent magnets. So, here are the key points: 1) The magnets need to be very strong, like 12,000 gauss strong to overcome the coercivity of modern disk drives. 2) The magnets need to touch the platters, which means disassembly of the drive and separation of the platters (each platter is wiped on both sides. This is due to the fact that while the magnetic force is extremely powerful, it is only that way at very small distances). Also, steel, as in the case of harddisk enclosures, acts as a shield, so the tests people have run using very strong magnets on the outside of drive cases are faults tests, because the case is shielding most of the magnetic flux, and the distance to the platters is too great to overcome, no matter the strength of the permanent magnets. 3) In reading various papers and patents, it appears that one aspect that needs to also be considered is alternating polarity of the magnets. Some of indicated that an AC circuit is needed, but that would seem to be refuted in the case of the NSA approves permanent magnet wands. So, it would appear that having an array of very strong magnets, with alternating polarity, passed across the platters, in direct contact with the platters, is enough to overcome the coercivity of the media being erased. The problem is that these NSA approved wands and anywhere from $500 to $700, which is probably not much for a business, but for individuals it is a pretty penny. Also, one can never be completely certain that the wand really performed the job, as the drive cannot be used again once the procedure has been performed. However, I would think that performing such a function, followed by some form of physical media destruction would probably be sufficient to almost certainly guarantee little if any chance of data recovery. One would need to consider how likely it would be at that point for someone to attempt to recover such data. So, I decided to build my own paddle, which uses N42 rare earth magnets at 28 pounds of pulling force each, which I am pretty sure is significantly higher than the NSA approved paddles I looked at, given the dimensions of the magnetic material. I used an alternating pattern of poles, which concentrates the magnetic field between the poles. I placed each platter in a paper towel, as demonstrated by one of the vendors of one of the NSA approved paddles, and moved the platter back and forth across the array of magnets, rotating the platter from time to time to induce an alternating magnetic field across the entire surface. I repeated on both sides, and performed this procedure on all the platters. The fields of these magnets are so strong that the platters now have a noticeable level of magnetism, which they did not have before the procedure, and, in theory, the lines of magnetism should be rather scrambled across each platter surface. I doubt seriously there are any forensic tools out there that could read any data remnants from these platters, but, to be safe, I will also perform some physical destruction on them as well. So, the point of this posting is to let people know that there are physical methods available that use permanent magnets to scramble data to the point that it cannot be retrieved, and they are within reach of the average consumer, but you have to know and abide by the science behind it. The magnets cost a total of like $70. One might ask why if these are inferior to the $500+ NSA approved wand, based on price. The answer is no, because magnetic materials have physical limitations in terms of their ability to produce magnetic force. These are N42 magnets, surpassed only by N52 of the same size in terms of strength. Larger N42 magnets can yield higher magnetic force than smaller N52. Even if the NSA approved paddles are using N52 magnets, the physical size of the N42 array I created is thicker and produces more force. The reason these paddles are so expensive is because gaining NSA approval costs big bucks, and these paddles are sold to businesses, where the businesses don’t care about the price, compared to the cost of say an $18,000 degaussing machine where you don’t have to disassemble the drive. So, even if your drive refuses to work, making options like DBAN unavailable, there still is hope, at a reasonable price, and it doesn’t involve dunking your drive in acid or using a blow torch. 🙂
Honestly, that’s when I just get out the drill and start drilling holes in the drive. Much cheaper, and often quite therapeutic.
Hi Leo,
Aside from the hard drive, are there any other laptop components that hold sensitive data and should be erased before donating?
Thanks!
If you wipe your internal drives (both hard and SSD), you’ll be safe. DBAN will automatically find and wipe all internal and attached drives on your computer.
What ever happened to the bios format? I remember on older machines the Bios setup used to have a format. It doesn’t anymore it seems. here is al ink to recover deleted files in hard disk
How many holes do you drill? Which area/position of the disk do you drill?
Thanks
There are no specifics available on that. I’d say, as many as you can.
Hi Leo. What are your thoughts on CCleaner’s “Drive Wiper” feature? I typically delete the files that I know to be personal then use the “Free Space Only” option. If completely overwriting a drive I use the “Entire Drive” option. I like doing it this way so I can wipe drives while being logged into windows.
CCleaner’s wipe feature is fine for wiping free space, but it can’t wipe the c: drive. In order to wipe the system drive, you’d need a program like dban which is a standalone bootable wiper as you never know if there is a sensitive file which you forgot to delete.
That works, except the a drive wipe can’t completely wipe a system drive that’s in use. For that you need to be able to boot from something like dban.
This iPad was given to me by a family member I have pictures and other things on here but I’m still getting my family members messages and info on here how do I delete her without messing up what’s mine on here?
You would do well to find a site the specializes on iPads to get your best answer. But mostly you’ll need to log out as her. That means to log out from her Apple account, and also from any apps she has installed. Delete apps you are not using. Then create your own Apple account and log in as you.
You’ll want to first make sure that your own pictures are stored locally on the iPad and not in her iCloud account. So it would be good to find iPad specific instructions.
Well if you dont do so….you data might be at risk. Around 57% storage devices have data in them at the time of reselling. Hope no one wants to share their private data with suspicious people. A good way of doing so is using certified and secured Bitraser for file software
Or DBan. Or just encrypting the hard disk and throwing away the key.
Dear Leo,
Thanks for your reply!
Encrypting is also a nice option.
Cheers
According to Scott Moulton a hard drive recovery expert, a simple Windows full format of a hard drive is enough to prevent the data being recovered by normal human beings, repeated overwrites or smashing the drive is plain overkill unless you expect the NSA or FBI to be looking at your drive.
There is nothing I haven’t tried to erase clean my hard drive.
I have a Dell computer with Windows xp version 3.1 no matter what I cannot see what key would allow me to erase everything.
I installed the disc but only allowed me to reboot nothing more .
Every one on the Internet shoot of their mouth but nothing that I am able to use .
Can someone please help me and spoon feed me the information.
Thanks
Honestly, it really depends on exactly what you’re looking at.
My hard disc is about to fail and as my computer is over 7 years old I’m thinking I should replace rather than repair. If the HDD fails before I have
purchased another PC, will I still need to run something like DBAN? Is disposing of a failed disc still insecure? Thanks…
In some cases, there are ways to revive a faulty drive so it’s best to take the extra steps to wipe it. The drive may be damaged in a way that DBAN won’t work, in which case, you might have to drill a few in the drive.
Question – my only concern is if passwords or keystrokes can be recovered from a hard drive after a factory reset of a Dell laptop using Windows 7. I want to donate the laptop in usable condition – as long as my previously saves passwords cannot be recovered. I performed the factory reset already and as I visit sites I had previously it appears my old usernames and passwords are gone – but therein lies my level of paranoia. Are they?
Run dban, or a full (not quite) format of the drive, as outlined in the article.
As an alternative to the drill press – In the past I have put all my old hard drives in the fireplace. Thy melt into a small puddle and later solidify into a nice round metal blob you can just toss.
Software obsolescence is a good argument for hanging on to an older computer with an older version of the OS to be able to run older programs to be able to access data otherwise inaccessible by a newer machine.
When I’ve had hard drives that were no longer needed and still functional, I did a full format of the drive then encrypted the drive using Bitlocker and tossed the recovery key. Then I took the drives to my local computer shop, letting them know that the drives were encrypted. This way, whoever got them had to format the drive before it could be used to remove the encryption. I’d guess that the same could be done using Veracrypt.
Failed drives get introduced to my drill.
A full format would be sufficient. Encryption would add no more security. Since there are no files on it, there is nothing to encrypt.
Hello, all;
Since I gave up on windoz & went linux I’ve learned a bit more.
To “securely” wipe a drive is pretty easy.
Download a linux distro, put the .iso on a flash drive, & make it bootable.
Stick the drive in a USB port, & reboot.
When you boot into most linux distros you’ll have the option to try the distro or install it.
So using the ‘try it’ option you can use the linux drive tools to format the drive.
Done properly that should completely remove all user data on the drive.
I’ve done this on several old computers.
I haven’t even bothered to try to recover any old data, mainly because its not worth the time.
That last bit is key.
If someone wants YOUR old data there must be a specific reason.
If it will take a lot of time (I mean really LOTS) so most simply won’t do it.
Remember, “paranoia will destroy ya'”.
If you are really intent on removing the user data its not too hard.
But usually its also not needed because hardly anyone could care.
I think for most people the drive is worth more than any data on it.
Have a GREAT day, Neighbor!
If you do a full format, the data will be, for all practical purposes, unrecoverable, except for an expensive recovery service. If you do a quick format, the data can be recovered by anyone with a data recovery program such as the free Recuva.
I tend to use ‘Secure Erase’ (using ‘Ultimate Boot CD v5.3.9’ from majorgeeks website which is free (it’s not straight forward to use though but it’s not hard once you know what to do)) to wipe a drive as it’s faster than DBAN and ‘good enough’ even though it’s more complicated than DBAN (DBAN is okay for regular hard drives but NOT for SSD’s) since it requires removing power cable with the SSD/HDD on and then plugging it back in etc to get it in a state the Secure Erase command can be issued.
but Secure Erase, like the article mentions, is needed for SSD’s and good news is it only takes a couple of seconds to finish on a SSD since it resets some sort of encryption key internally in the SSD drive itself from what I understand. so while the data is still on the SSD, it’s unreadable as it’s like it was wiped and explains why it works so quickly compared to a regular hard drive where it’s got to wipe the entire drive to erase it which takes much more time.
but issuing a Secure Erase command using that Ultimate Boot CD it does not give you a estimated time remaining but the drives I used it on take roughly 1-1.5hrs to finish and then it alerts you it’s finished. on regular hard drives… Secure Erase will always be faster than using DBAN given DBAN, like this article says, makes more than one pass, which like the article also says, many (including myself) consider to be a little overkill. although… DBAN is a safe option for securely erasing a hard drive is your not that concerned with time to erase it.
if I get a hold of a used hard drive I issue a Secure Erase on it before using as you just never know what the previous person had on it. plus, it’s something I run on my older hard drives for good measure once in a while to make sure anything sensitive that may have been on there 5-10-15 years ago is truly gone.
DBAN is fine for SSDs. You can set it to one pass and that will completely wipe everything securely. In fact, for the average user, on pass is enough on hard drives as it will cost a few thousand dollars to restore any data. Unless you have data someone will spend thousands to recover, stick with one pass.
As I understand it, that’s not the case. Not because of wear, but because of SSD’s “wear leveling”. You may not actually be erasing everything. Which I find odd, but I see referenced too many times to discount.
More on what Leo said: SSDs don’t store or delete data the same way as hard drives so the typical overwriting of data or reformatting doesn’t work to securely erase data. The controller on an SSD has algorithms to decide where and how to write data. These algorithms are different for different manufactures, so only the specific SSD controller knows where the data is and how it might have to be erased. Along with “wear leveling”, these algorithms shuffle data around and do garbage collection in the background. In other words, your typical OS disk management software doesn’t know where the data is on the SSD. That’s why defrag doesn’t work on an SSD. If you try to overwrite an SSD with 1’s and 0’s, it will not necessarily overwrite in the same physical locations as the files you’re trying to erase. Besides, if you do that too often you’re wearing out your SSD. Also, there is a difference between erasing an entire SSD and erasing some files or folders. On an SSD data is written in blocks and pages and you cannot securely erase just a few files within a page if there are still other used files within the page. The best approach to secure erase an SSD is to use an application provided by the SSD manufacture, which presumably should know how the SSD controller handles data. The physical method of “erasing” is to apply a voltage to pages to reset the transistors to the factory initial state (no overwriting). Some newer computers may have this reset feature built into the UEIF.
I have a laptop which originally had windows on it. I have subsequently installed Linux on it not once but at least three times (for various reasons). No dual boot but complete installation
There has been no usage of the machine after the linux installs – do I still need to worry about old data?
When you perform a format and install of a new OS, it performs a quick format. That only clears the file index, and ll of the data stays intact on the free space of the drive. A full format or free space wipe is necessary to remove all of the data from the drive.
No need to worry. Just do a free space wipe.
I already made a post from Sep 2021 ( https://askleo.com/erase-my-hdd/#comment-1116356 ) but I was playing with stuff some more recently in regards to ‘Secure Erase’ which I think I might as well mention it…
while I already mentioned the ‘Ultimate Boot CD’ stuff, and that’s fine to still use, I noticed it comes with a old Linux kernel and I am not sure if that would be a issue with more recent hardware with it properly detecting everything (as the computer I used was older than the kernel used in that Ultimate Boot CD). but I recently learned one can use a more modern Linux setup, I used a Linux Mint ISO (I used Linux Mint v21.0-Xfce) which comes with a 5.15 Linux kernel which is pretty much Oct/Nov 2021, so it should support a lot more hardware, and with that (one simply boots up to it like usual) one can manually issue the ‘hdparm’ commands as follows to issue a ‘secure erase’ to the drive…
1)sudo fdisk -l (that “-l” is a lower case L) and find the precise location of the hard drive you want to ‘secure erase’. it will be something like “/dev/sdx” (where ‘x’ is the location of your hard drive you want to ‘secure erase’) and then use whatever yours is on the commands below!)
2)sudo hdparm -I /dev/sdx (that “-I” is the capital letter ‘eye’ (I)) (and check under ‘Security’ section as if you see ‘frozen’ instead of ‘not frozen’, which will likely be the case, proceed to Step 3 (if not proceed to Step 5))
3)sudo hdparm -Y /dev/sdx (NOTE: make sure to use a capital Y, not lower case!) (which will power down your hard drive (the one you want to ‘secure erase’) and after a few seconds you can then physically remove the SATA power cable from the drive you want to issue secure erase on, wait 5-10 seconds, then plug it back in, wait for it to fully spin up, call it 30 seconds or so, then proceed to Step 4.
4)sudo hdparm -I /dev/sdx (“-I” is a upper case ‘eye'(I)) (under ‘Security’ section check to see if it says ‘not frozen’ now. assuming it says ‘not frozen’ proceed to Step 5.
5)sudo hdparm –user-master u –security-set-pass temp /dev/sdx (NOTE: you can set the ‘temp’ to whatever you want but make it something very easy to remember) (at which point it will probably show something like “/dev/sdx:
Issuing SECURITY_SET_PASS command. password=”temp”. user=user, mode=high” then it will kick you back to the usual terminal prompt, then proceed to Step 6.
6)sudo hdparm -I /dev/sdx (check to see under ‘Security’ that it looks similar to the following…
Security:
Master password revision code = 65534
supported
enabled
not locked
not frozen
not expired: security count
supported: enhanced erase
Security level high
(the ‘enabled’ and ‘security level high’ are the important things that should be showing)
7)sudo hdparm –user-master u –security-erase temp /dev/sdx (once you do this the ‘secure erase’ will immediately start and you will see that white icon just sitting there like nothing is happening (but it’s currently ‘secure erasing’ the hard drive and will return to normal prompt after roughly 1-2hours pass to maybe 10-12hours depending on the size of your hard drive (but you can check estimated time to complete on the menu’s a bit before this starts which should be a pretty close time estimate. on my 250GB 2.5″ Toshiba drive it estimated ‘secure erase’ to take 88min). but once you are back to the normal prompt where you can type again, do one last thing, go to Step 8.
8)sudo hdparm -I /dev/sdx (basically the ‘enabled’ and ‘Security level high’ (shown in Step 6 above!) should NOT be visible anymore. so as long as it’s NOT visible, you are done and hard drive has completed the ‘secure erase’ process. you can power down and use the hard drive like you normally would if you want to.
NOTE: as a possible/safer alternative to Step #3, which does not work on my ASUS A8N32-SLI Deluxe computer, but may work on other peoples computers, you can try “echo mem | sudo tee /sys/power/state” instead as it will suspend the system and then wait a few seconds and press a key on the keyboard to bring the system back to life and see if the hard drive is ‘frozen’ or ‘not frozen’ as if it’s ‘not frozen’ then you won’t need to physically remove the SATA power cable from the hard drive while the computer is on, otherwise you will need to do it to get the hard drive to a ‘not frozen’ state to proceed with the ‘secure erase’.
recently on a 250GB 2.5″ SATA hard drive (a laptop drive) connected to my old desktop, which is a ASUS A8N32-SLI Deluxe motherboard (high end 2005 tech but I had it since March 2006 and is my backup computer), it took roughly 1hr10min to finish and on a 6TB HDD it took about 10hrs to finish as this will give people a good estimate of the time that’s required to finish ‘Secure Erase’ depending on your hard drive size.
that’s pretty much what the ‘Ultimate Boot CD’ does except the Ultimate Boot CD is easier. but I just thought I would mention the manual way from the prompt in case someone can’t use that Ultimate Boot CD for whatever reason and needs something a bit more recent to issue the ‘secure erase’.
while that sounds complicated it’s probably the most proper way to securely erase a hard drive so no data recovery is possible. but I suspect DBAN is good enough for a typical hard drive and is easier to use.