The secret administrator account, at that.

We tend to think of accounts on your Windows PC as being either administrator or limited. There are reasons to use both in various situations.
But what you think of as an administrator account isn’t really THE administrator account. Some computers have another account that has been referred to as a super-administrator mode.
Computers can run in limited, administrator-capable, or administrator accounts. I’ll describe the differences between the three and how to access the most powerful account of all.

Enable the administrator account
Besides the standard limited and administrator-capable accounts, there’s a more powerful administrator account. It’s disabled by default. Enable it by running “net user administrator /active:yes” in an administrative command prompt. This account runs without UAC prompts and initially has no password, which poses a security risk. You can use it for specific maintenance tasks to avoid repeated UAC interruptions, but it’s crucial to set a password if you activate it.
Limited user accounts
Limited user accounts (LUA) run with restricted privileges. This prevents malware from being able to do whatever it might want to on your machine. When running with an LUA account you, and malware, don’t have the privileges to make system-level changes to you machine. In some corporate environments, it prevents you from making changes to your system contrary to your IT department’s wishes… but that doesn’t mean you can’t try.
When you attempt to make system-level changes while signed into a LUA, or try to run an application that requires true administrative access from the get-go, you’re likely to be presented with the UAC, or “User Account Control”, message.
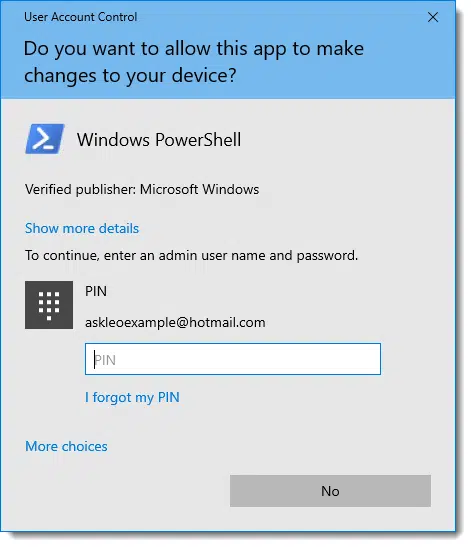
In order to proceed, you must prove you are authorized to do so by providing the credentials for an administrator-capable account on that machine. Otherwise, you can’t do whatever you are trying to do.
Administrator-capable accounts
This is the default type of account created when you set up Windows. While we call them administrator accounts, they’re really not; they’re what I refer to as administrator-capable.
When running normally, they run much like an LUA. And like an LUA, when administrative access is required, you’ll see the UAC prompt.
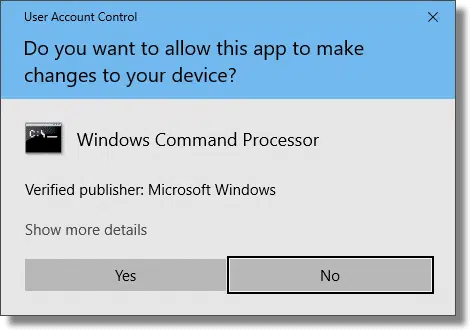
The difference is simply that you don’t need to authenticate any further. All you need do is say “yes”. When using an administrator-capable account, no further authorization is required.
That’s the primary difference between LUA and administrator-capable accounts: whether or not UAC requires more authorization or you can just click on Yes.
The real administrator account
There is another account, called the administrator account, in every version of Windows. Using that account, you are running in administrator mode all the time. There are no UAC prompts to get in the way.
By default, it even has no password!
Also by default, you have to enable it before you can use it.
In an administrative command prompt, run:
net user administrator /active:yes
The output will be very boring.
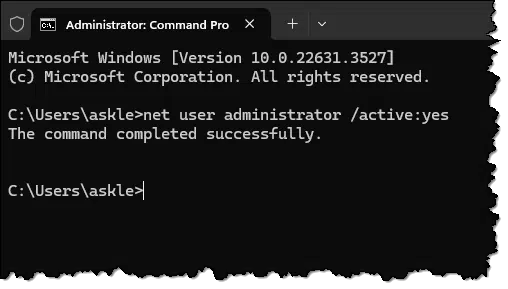
Sign out of Windows.
On the sign-in screen, you’ll now see the Administrator account listed as an option.

Click Sign in, and you’re in as administrator. You have full control.
The built-in security hole
But wait: all you had to do was click Sign in. No password was required.
That’s a huge security issue.
So the first thing you should do is set a password.
Hit the Start button, and search for “password”. Click on Change your password when it appears. This will take you to the Sign-in options page of the Settings app.
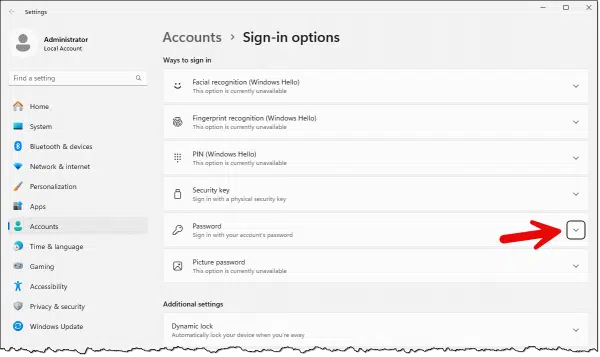
Click on the down-arrow to the right of the “Password” item. Then click the “Add” button that appears.
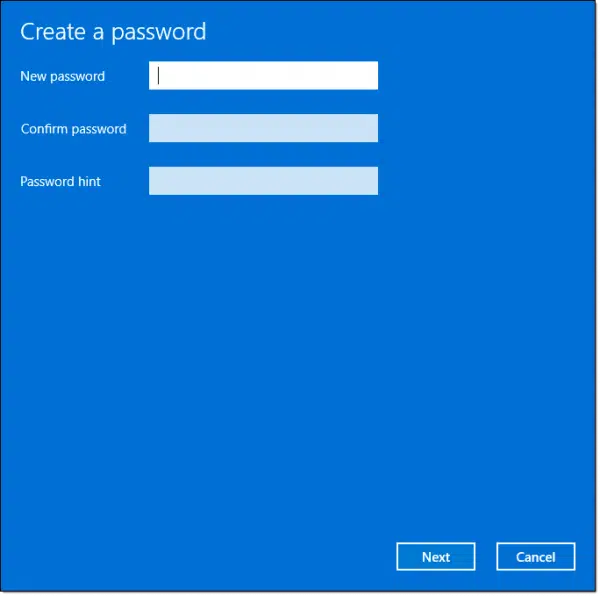
Enter your new password, add a password hint, and you’re done.
So why would you want this account?
Normally, you don’t need to operate your computer from the administrative account. That’s one reason it’s disabled by default. Your administrator-capable account is all you need for day-to-day computing.
However, in some situations — perhaps involving maintenance or other situations where you’d end up facing UAC over and over again — it might be a useful way to streamline your work.
Do not use the administrator account as your regular work account. Any accidental system changes would not require confirmation. Even more troubling, malware could install itself without notice.
I recommend living with the occasional UAC.
Do this
Live with UAC.
But if you can’t, or have a scenario where being the One True Administrator for your machine would be helpful, you can turn it on. Just be sure to add a password. Sign back into your normal account when you’re done.
Administrative access is not required to subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.




I remember in the old days when I’d get administrator access on store display computers and surf the Web. I’d sometimes make myself the administrator by setting a password.
I’ve used that account on my computer only a couple of times when the normal means of gaining access to a file didn’t work.
“However, in some situations — perhaps involving maintenance or other situations where you’d end up facing UAC over and over again — it might be a useful way to streamline your work.”
If it were just a matter of saving time by bypassing UAC, I wouldn’t bother using the Administrator account. Sometimes, accessing some files requires going into properties and changing permissions which can be a lot of work if I need to access several protected files. Admin accounts make changing permissions much easier.
Does the obvious “net user administrator /active:no” disable the administrator account?
Yes.
How do I determine what admin account I have currently?
If you haven’t followed the steps outlined in this article, you have an administrator capable account.
Off topic but important info about the deleterious effect of the Chrome Browser “swipe enabled” on a PC:
NOTE: If you do your computer stuff from a device with a swipe feature, ignore this post.This is for PC Chrome Browser users that do everything with a mouse and a keyboard.
I recently discovered this and I am passing it on to readers here to help them make their computers last longer.
I am running a PC monitoring program called HWiNHO64. It has a LOT of possible things that you can monitor. It is free and NASA uses it. It is free from malware too.
I monitor temperatures, wattage, CPU percentage usage and GPU percentage usage (etc.). It took me a while, but I finally got the software set up to monitor just what I wanted, and not the umpteen possibilities that come off the shelf. What bugged me was why my temps kept spiking for no reason. I discovered the cause was THIS SETTING in Chrome:
Chrome >Settings > Accesibility >
Swipe between pages
Navigate back and forward with a swipe gesture
Chrome has it ON by default. I turned it off and the temperature spike stopped. So, why is this important? Because routine 70 degrees C (158°F) or higher equals short term life for a CPU.
Since there is no swipe software on my PC, the computer goes bananas for a while trying to find a swipe thing that ain’t there. I need that like a dog needs ticks.
I have my alerts set on the HWiNHO64 software to >= 145°F to be super safe. My Dell Inspiron PC is now 8 years old and has outlasted any PC I had before. I’m pretty sure that is because I keep the temperatures in the safe zone. I recommend you do the same, but even if you don’t, TURN OFF THAT SWIPE FEATURE ON CHROME if you have no swipe software on your PC. You will help extend the life of your PC by avoiding needless temperature spikes.
I use Autohotkey scripts to run triggered alert actions. They help.
Old Saying by me: Frugality is Freedom.
Maybe frugality does not equate to freedom, but it can help you preserve the freedom you still have.
I turned that swipe off in my chromium browser in my Debian laptop. Thanks.
I’m using Win 8.1 Pro. I’m logging in as administrator but still there are some files I get the message ” Amin permission needed”
How can I apply your article for my operating system.
See these articles:
How Do I Copy Files When Windows Says I Don’t Have Permission to Access This Folder?
How Do I Run a Program “As Administrator”?
I just turn off UAC every time I get a new PC, by going to UAC and changing it to Never.
Great if it works for you. Not recommended in general, though.
Turning off UAC allows malware to install itself without having to ask for permission. UAC requires all installations and programs that require low level access to your computer to ask your permission before executing. Without UAC, you are vulnerable to drive-by malware attacks.
Item #1. Leo, you wrote:
“…Enable it by running “net user administrator /active:yes” in an administrative comment prompt…”
Excuse me, did you mean to say “an administrative command prompt”?
Item #2. What, if any, difference then is there between this “True Administrator Account,” and simply running a (so-called) “administrator-capable” account with all of its UAC’s turned off…???
Well, that’s embarrassing. Fixed.
I’m not 100% certain on the admin account problem. I’m not aware of any differences, but it would also not surprise me if there were some subtle things.
Leo, in my command prompt area (black screen with small print), it says:
c:users\Sandra>
I tried making my user acct into administrator acct to be able to allow something to be downloaded to my machine that needed an administrator password to allow it. Now I can’t do anything without a password and I can’t figure out how to change it back to what it used to be on the black screen. I am afraid I have made a big mistake but want to know if it can be fixed or will I have to buy a new computer and start all over again or send this one back to factory reset??
If it’s connected with a Microsoft (outlook.com, hotmail.com, live.com. msn.com) Account and you don’t remember that password, you might be able to recover it by recovering your Microsoft Account.
I’ve Lost the Password to My Windows Administrator Account. How Do I Get it Back?
There’s no need to get a new computer unless your computer’s hardware fails or you want to upgrade. If all else fails, you can reinstall Windows and install all your programs from their installation files, AKA the Nuclear Option.
Hi Leo, I have an older laptop that has windows 10 and got myself into a bind. I was trying to enable Outlook, which asked me to create a Microsoft account, which I did, an it looks like Microsoft took over my machine as Administrator! The Only Administrator! I can’t seem to get rid of it and on startup the only login screen that comes up is the Microsoft login screen and NO other accounts. I tried you user admin text at (Windows PowerShell (admin)) but I think because I have to be logged in to Microsoft it won’t allow another administrator or user. Am I dead in the swamp now?
You should absolutely be able to
or
or
Hello again Leo, I tried the PowerShell prompt info again and it worked this time! I may have missed a space or letter the first time I tried it. I then went in and DEFINITELY generated a password like you instructed. Then I went into settings and changed that nasty Microsoft account to a Standard account. The damage may already be done but I removed that sick one-drive app and I can now log in to my machine as my own administrator. This scared the hell out of me and I’m so thankful I found your video Leo, albeit a year old already. I’ll keep watching and be more careful from now on.
Thank You, Norm
Hi Leo,
Where you have “Command Prompt” and “Command Prompt (Admin)”,
I have “Windows PowerShell” and “Windows PowerShell(Admin)”.
When I opt for the Admin, I get the same screen as you, but the top line is simply “Windows PowerShell” above 2nd line “Copyright (C) Microsoft Corporation. All rights reserved”:
Inserted below this is 3rd line: “Try the new cross-platform PowerShell htpps://aka.ms/pscore6”
and then on the 4th line, the letters “PS” appear just before C:\Windows\system32>
When I type “net user administrator/active:yes” and press Enter, I get the following:
“The syntax of this command is:
NET USER
[username [password | *] [options]] [/DOMAIN]
username {password | *} /ADD [options] [/DOMAIN]
username [/DELETE] [/DOMAIN]
username [/TIMES:{times | ALL}]
username [/ACTIVE: {YES | NO}]
PS C:\Windows\system32>” and the cursor is flashing here.
I was flumoxed by this as it seems like Kafkaesque and so I went to Settings and ended up signing in to My Microsoft Account, which set off numerous actions beyond my ken and control and “syncing” Bing across all devices, which was not anything that I wanted to do.
As I have a DELL laptop without an internal optical drive for CDs and DVDs, I purchased a DELL external drive that came with “CyberLink Media Suite 12” disc. When I tried to run this disc, I got a red flag pop-up saying that an ADMINISTRATOR had blocked it for my safety claiming source unknown.
Obviously, it is my own personal computer and I should be the only administrator to make decisions, which brought me to askleo.com.
Since last night I have now become identified as “administrator” within My Microsoft Account, but it is in name only as I am still confronted by the same red flag pop-up when I try to run the CyberLink disc. (Incidentally, when I tried to bypass the red flag and download the software from the CyberLink website, I was instructed (by CyberLink) that it was only possible to do this with a pc with an internal optical drive, and NOT an external one.)
Now, however, instead of “PS C:\Windows\system32>” I am faced with “PS C:\Users\My Name>” and the flashing cursor. When I then went to Settings and decided to revert to “Standard User” instead of “My Microsoft Account” in order to regain my personal independence, I could only do so “forever” and not simply as an alternative user. Microsoft suggests that I should use their AI “CoPilot” to solve my problem and to therefore open live communications with their website. I have no faith whatsoever that MS will help me as they seem to want me to go to their Store if I want software! I just want to act as administrator on my own laptop and run/autorun any disc I choose.
Kind regards
Berkeley
I’ll have an article on powershell/terminal/command prompt soon.
In your case:
net user administrator/active:yes
There should be a space between “administrator” and “/active”.
Hi Leo’s team, I’m kinda lowtech so I have trouble in get admin right. I bought a new PC, I configured Windows 11 Pro, and after some time I switched to a local account, and when I wanted to install an antivirus (Bitdefender Total Security) I noticed that I do not have administrator privileges. I logged in with the Microsoft account (it was configured) but it still does not have administrator privileges. I tried everything but I can not switch to an account with administrator privileges. I have try to use the command “net user AdminNew P@ssword123 / add” and the system said The user or group account specified cannot be found. he user was successfully created but could not be added o the USERS local group.
More help is available by typing NET HELPMSG 3774. and for the command “net localgroup Administrators AdminNew /add“, I recieved “The command completed successfully.“ What do you advise me to do? I only know what to do.
Thank you
p/s: in the cmd it it a line show Microsoft Windows [Version 10.0.26100.1]
looking to set up windows 10 w/admin to keep my son from installing what I don’t want on his system
Right-click the Windoes Start Icon
Click “Settings”
Click “Accounts”
Click “Other users”
Click “Add account”
Click “I don’t have this person’s sign-in information”
Click “Add a user without a Microsoft account”
Enter Username and Password
Click Next
Enter the required information including the security questions
(The next steps may not be necessary if the default is Standard Account)
After creating the account, select it under Other users.
Click Change account type.
Set it to Standard User (not Administrator).