Turning off Remote Access does NOT protect you from remote-access scams.
Safer, sure. But probably not as safe as you think.
Remote access comes in many forms, and you’ve only turned off some of them.
Become a Patron of Ask Leo! and go ad-free!

Turning off Windows remote access
Turning off Windows Remote Desktop disables only the Remote Desktop Protocol (RDP). It does nothing about other types of remote access. Software on your machine, including legitimate tools as well as malware, can still allow remote access. Never assume that if RDP is off, all remote access is prevented.
Windows remote access settings
The setting you’re most likely to have altered is the Windows Remote Desktop feature. (Search settings for “Remote desktop”).
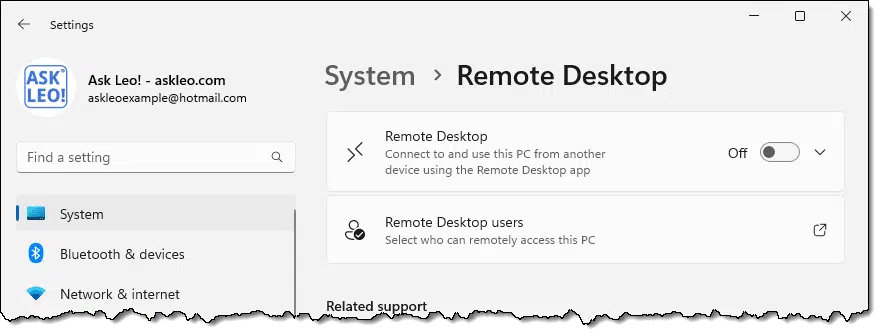
This does, indeed, turn off the ability for someone to connect to your computer using the remote desktop protocol via the Remote Desktop application included in Windows.1
Nifty — though you were probably already protected by your router, which disallows incoming connections anyway.
Besides, none of this disables the ability to access your machine remotely.
There is no setting to do that.
Scammers and remote access
This topic comes up most often when we discuss the so-called “tech support scam” in which individuals call you on the phone claiming there’s something wrong with your computer, but that they will fix it for you and need remote access to do so.
To make that happen, they’ll direct you to a website or a download, at which point you follow a few steps, perhaps enter a code of some sort, and — bingo! — they have the remote access they want.
Even if you’ve disabled Remote Desktop in Windows Settings.
You’ve just bypassed the setting you so carefully set. In fact, remote desktop wasn’t even used. The scammers use any of a number of alternative services2 and protocols that have nothing to do with remote desktop.
The key to remote access
The common thread to the remote access scam, as well as to any legitimate remote access, is that you need to be running software on your computer that initiates the connection.
Your router prevents incoming connections. It’s software running on your computer that allows, or even invites, others to connect. That software comes in many forms.
- Remote access software you’ve installed, such as Team Viewer or Chrome Remote Desktop.
- Remote access software you run on demand, such as conferencing software like Zoom, GoToMeeting or others allowing you to display your desktop in a video conference or give control of your machine to one of the other participants.
- Remote access software you run when getting support from a trusted yet remote friend, relative, or service technician.
- Malicious software. Because malware can do anything.
The key is that the software is running on your computer.
This allows us to make decisions to get safer still.
Do this
The solution is fairly straightforward: choose what to run.
- Disable, or not, Remote Desktop. As I said, your router protects you from incoming connections.
- Choose not to install remote access tools, or choose not to leave them constantly running, loading them only as needed.
- In conferences and online video meetings, only give access to your computer to people you trust.
- Only run remote-access software when requested by people you already know and trust.3
- Do everything you should already be doing to keep your computer safe on the internet and free of malware.
The bottom line is that remote access requires your participation either explicitly, by running remote access tools, or implicitly, by having allowed malware on your machine.
The solution is simple: don’t participate.
Here’s something that’s safe to participate in: subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: The other feature you may have disabled is “Remote Assistance”. This is actually significantly less of a security concern, as you must initiate it. Regardless, disabling it does not disable remote access.
2: Many of which are completely legitimate tools. They’re just being abused by these scammers.
3: A stranger calling you on the phone does not meet this criteria.




Thanks Leo, that`s basically what i was wondering. i know no one, not even you, is ever entirely safe on the internet. but i was hoping with remote access turned off, i would at least be “safe-er”.
Is it safe to leave your computer on when you’re finished using it at the end of the day? Unfortunately I have already let people have access to my computer. They were employees of My computer company. I didn’t like to give them access but sometimes I needed to. So in that case they already have access correct? I hope this question isn’t stupid. Thank you
If you give them a limited guest account, they can cause much less damage because they won’t be able to install programs. I won’t say it’s 100% safe. Nothing ever is but it is much safer than an account with admin privileges.
I’m not sure how to answer your question: is is safe to leave your computer on? It certainly can be, I do it all the time. If you’ve given others remote access you can always revoke it, depending on what technology you used — it could be as simple as changing a password or not running whatever remote access service they use.
About leaving your computer on when you’re not using it: Statistically this is a long shot, but the possibility exists for a malicious remote connection to your network. This can happen when your router or an application on your computer is probed randomly, hoping to find a vulnerability. You’ve heard of all those Windows “vulnerabilities”? Many of these vulnerabilities are about any number of background applications or services running on your system that have open network ports (access points), waiting to accept a connection from the outside. As Leo said, the attacker first needs to get through your router, but the router also has its own remote connection applications, as well as other vulnerabilities. Similarly, your firewall isn’t perfect either and it depends on its settings to stop incoming connections. You might be surprised to know that when you install an application, the application can insert itself as an exception to the rules of the firewall, meaning that the firewall will allow an external connection to that application. Once a connection gets past the router and firewall the attacker can exploit other holes in the system to do damage. As I said, this is statistically a long shot, but possible.
From my side, I used both Microsoft Internet Explorer and Microsoft Edge (As I have Windows-10). I noticed the only times I had the scammers message “Your computer is infected and you have to disinfect it immediately” or something like that, and the only way to get out of the message screen is clicking Cntrl Alt Del, simultaneously to close the program. But it does not come when I use Edge. I therefore suggest that everyone with Windows-10 use only Edge as the browser.
Leo This article really hit home.
I really thought I was a savvy computer person and would never be the victim of a “technical support scam” How mistaken I was — they did not ring me uninvited. I simply mistyped an URL and ended up with my router being hacked. I had no idea it could be that simple – you find a site – top of a google search and it looks legitimate. Perhaps a warning sign was the very prompt offer of technical support,
However when you think the company you are dealing with is legitimate – and they are being helpful and you do have a problem it is so easy to say — yes I will let you load a well-known “tech support” program and assist me
Cutting a long story short – I realised after 5 minutes of technical jargon that this person/company either was after my credit card details or wanted access to my computer for a potential ransomware attack. I had not done the first and there was no evidence of the second – thanks to your “nagging” about malware programs
What they did do though was hack the router so the SSID kept changing. Fortunately, I had a second router and the hacked router was still under warranty.
However, it was a salutary lesson in how vigilant you need to be.
This is a timely re-run of this article for us.
Yesterday the speakers on our laptop had ceased working, and via Windows 11 settings we ran the troubleshooter. It asked to access our speakers, and did indeed fix the issue.
Is there something I need to turn off now, or was that access we allowed a one and done deal?
That should be unrelated to any kind of remote access.