Unless you are either lucky or prepared, your options are few.
My morning email brought this question from a friend.
While there are a few straws to grasp at, the odds are not good. The whole point of ransomware is that there’s no easy way to undo the damage. If there were, ransomware wouldn’t be a thing.
I’ll look at the few options you have, and more importantly, how prevention can give you peace of mind.

Recovery from ransomware
Ransomware is malware that encrypts your files, making them unusable. They promise to decrypt the files if you pay a fee (or ransom). You may get lucky and find decryption keys for the ransomware you face in a public collection, but it’s unlikely. Backing up properly is the only sure-fire way to recover from ransomware… next to avoiding it in the first place.
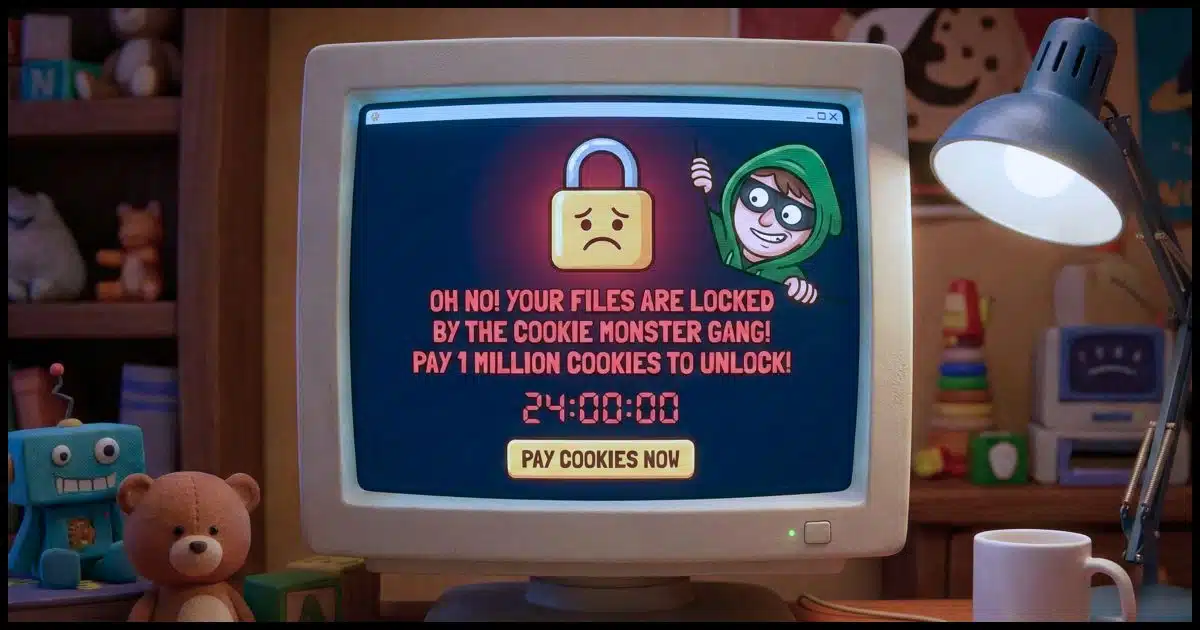
Encrypted by ransomware
Ransomware is a specific type of malware. It encrypts your files so you’re unable to open them, and then offers to decrypt the files if you pay the ransom.
Unfortunately, the technology used — public key encryption — is good. It’s the same encryption technology you and I use to keep our data secure and our internet conversations private.
When done right, a file encrypted using public-key cryptography is essentially unrecoverable unless you have the matching private key.
Needless to say, the hackers do it right. Without the private key from the hackers, it’s essentially impossible to decrypt files encrypted by ransomware.
Help keep it going by becoming a Patron.
Ransomware private key collections
As the threat and impact of ransomware grow, security pros and authorities work to track down the hackers and take down their operations. On occasion, they succeed, and that specific ransomware threat is stopped.
When this happens, the private keys the hackers had are sometimes (though not always) discovered and made available to the public.
The No More Ransom Project maintains a database of known ransomware keys. Quoting their site:
… it is sometimes possible to help infected users to regain access to their encrypted files or locked systems without having to pay. We have created a repository of keys and applications that can decrypt data locked by different types of ransomware.
I emphasized the word sometimes on purpose. There are no guarantees. In fact, in my experience, sometimes should really be on rare occasions.
If your files are encrypted by ransomware, that database is worth checking. In fact, if you haven’t prepared ahead of time, it’s your only option.
Cures for ransomware
The best cure for ransomware is to avoid having your files encrypted in the first place. Remember, ransomware is just malware, and that means using the internet safely. Avoid malware, phishing schemes, and all the other ways hackers get ransomware onto your machine.
The second-best cure is to have a backup. If you find your computer afflicted with ransomware and your files encrypted, restoring them from a backup is the only 100% reliable recovery method — and it doesn’t cost you any ransom.
And since ransomware can, in some (fortunately infrequent) cases, even encrypt your backups, you need to plan a robust solution that allows you to recover. Normally, this means automated daily backups and periodically storing a copy offline, out of ransomware’s reach. Some backup tools have now added additional protection that prevents malware from encrypting backups, so check to see if such an option is available on your software.
Recovering from ransomware
By far, the simplest, fastest, and most reliable solution to recovering files encrypted by ransomware is to restore them from a backup taken before the ransomware took hold. You restore the backup image of your entire machine to its state before the infection, and it’s as if the ransomware never happened.
Hopefully, once restored, you’ll know not to do whatever caused the infection in the first place.
If you don’t have a complete image backup of your machine, but you do have a backup of your data, recovery is possible, although it takes more work. I recommend that you:
- Take an image backup of the infected machine. This is to preserve a copy of the machine in its current state in case you need to recover something from it in the future.
- Wipe the machine and install Windows from scratch.
- Install your applications from scratch.
- Restore your data.
If you have no backup of your data, things are significantly more dire.
Online recovery
In recent years, online storage providers like OneDrive, Dropbox, and others “notice” if a large number of files in your account suddenly change. That’s one sign of potential ransomware at work.
When they notice this, they may offer to restore your files to their state before the massive change. If that massive change was ransomware, this could allow you to recover your files. Remember to:
- Clear your machine of ransomware first so the files aren’t immediately re-encrypted.
- Do so quickly, since the cloud services will only keep your older files for so long before permanently deleting them.
Decrypting ransomware-encrypted files
There’s no magical solution for decrypting a strongly encrypted file.1 If you don’t find the decryption key in a service like No More Ransom, then you’re severely out of luck.
Which leaves the ultimate question: should you pay? Let’s be clear: these are criminals you’re dealing with. There’s no guarantee that they’ll follow through should you elect to make payment. You could be throwing your money away, or you could recover your files. Only you can decide whether or not to pay the criminals’ ransom.
My position is: don’t. Doing so only encourages their criminal enterprise and puts even more people at risk of finding their files encrypted by ransomware.
Instead, learn from the experience. Most importantly, start backing up so this never happens to you again.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: Of course, you may believe that the NSA or other government agencies might feel otherwise. I don’t, but it doesn’t matter: they’re not going to help you here anyway.



Restore from a Backup is about the only solution. The hackers have noted your IP and such, so even if you do get rid of them this time, they will be back. The last time I got into hacker cycle I set up a UNIX box with strong security. Minimum software on it, and use your Windows machine as a client to the UNIX machine.
“hackers have noted your IP….they will be back”
Simply wrong. They may have noted your IP but most people reading these forums have an internet service that doesn’t issue static IP addresses. The hacker will not be back because your address changes every time you are online. Stop trying to scare everyone. Furthermore, I’m an IT professional for 10 years and I have no clue how to do what your suggesting as a solution so how do you think this is helpful to the masses?
@Gabe–I think what Van means is that “some” servers are static, and they do not change the address….by Unix box, I think he means obtaining a Unix based system–such as Linux or BSD, and using Windows as a virtual machine on that system. The issue, however, while there has been a significant growth in Linux based systems (which were traditionally devoid of malware and similar), hackers are only beginning to target Linux. Linux uses open-source software, free to the masses generally. The means that there are numerous software engineers looking at the codes so often that one of them ought to discover any changes and react quickly.
Also, too, one of the biggest hackers is in our own backyard, and it is not only the NSA and sundry three-initialed agencies. It is Microsoft using Windows 10. I have avoided Windows now since 2014 due to their theft of data…one must use as many privacy vehicles as possible, including VM above, VPN, and other DNS changes, plus constant amendments to encryption keys and passwords.
When I check my systems for malware, etc., I always disconnect from both the network and other external devices. Each device must stand alone as one is checking for viruses. Only when one is assured that each device (laptop, desktop, phone, external backups–including cloud storage) is virus-free, only then should one re-connect with the others. After such a virus check, then–and only then–should one immediately backup, remove the cable to/from the backup device, then continue on. If there is a problem, it would only take me a few hours to go back to my original state. Weekly backup should be the norm. IMHO
Absolutely Gabe – not very helpful at all! also if you are tech aware enough to understand and do what he is suggesting even if that was useful then surely you’re smart enough to avoid ransomware in the first place – no?
I know it becomes tedious,but keep banging away at backing up to a system image.I took your advise got a external drive and macrium .I have used that system image several times to not only get rid of malware but to correct some screw up I made that I couldn’t correct.super easy to do and invaluable.thanks leo for
pounding it into my head.
Of all the people I know that have a computer, NONE of them have any type of back ups(except me). If their Hard drive has never failed, it doesn’t exist to them. I no longer tell them to back up, anymore.
It’s very difficult to get people to back up. But one thing you may suggest is that they keep a copy of their most important files on one of the cloud services – like, Dropbox, Google drive, and the like. That will make them start thinking about how many really important files they have!
I have an external back drive that does it automaticaly. But I am thinking what make your external drive not be infected.
Turning it off when it is not being used for a backup or restore.
Before I retired I was a software programmer and then software manager. Backing up for me is a religion.
I find that the easiest way to backup is to use a SATA > USB cable (or caddy) and an external drive.
I do it once a week and with USB 3 it does not even take that long. Current files I backup daily I do have a question however.
Is it true that they will encrypt every drive that is connected to your system? If so, it is a necessity to disconnect any backup. Also is it true that once on your computer they can also access your cloud data?
Here are a couple of articles Leo wrote on that subject:
Should I Disconnect My Backup Drive When I’m Not Backing Up?
Will malware infect the backups on my connected backup drives as well?
That’s addressed here: https://askleo.com/will-malware-infect-the-backups-on-my-connected-backup-drives-as-well/
If I look at DropBox and OneDrive, they both source their data from the C:\Users\MyName\DropBox or OneDrive folders. So before they are in the Cloud, they do reside locally. If that gets encrypted, it will get encrypted in the Cloud service too since it gets automatically synchronized. I’m starting to think that I’m going to burn DVDs (or Bluray discs) of my most important stuff (photos, videos, documents) and store a copy onsite and a copy at my son’s place, which is 20 km away. There is no chance of both our houses burning down the SAME DAY, and if it’s on plastic, the data thieves can’t get at it from the ‘Net. I might start looking for a safe that is rated for CD and USB keys as well as for protecting paper from fire. A lot of safes can’t protect plastic from melting in case of a fire (the temperature at which paper will ignite is 451 F, but plastic will change shape way before that is reached).
I have all my files, movies, documents, etc etc…on 16GB USB’s, and then I have those same files on a TB external drive (Along with a copy of my hard drive). If one goes, I still have a copy of everything.
Yes, yes and yes. Yes they can and will encrypt files on all drives connected to the computer that gets infected. Yes they will encrypt files on your online backup if it is mapped as a share or network drive. And yes you do need to disconnect your backup drive to keep it safe. Sorry, no good news, it takes work to stay safe.
And as I’ve said in several responses already, “Yes” is simply too absolute a response. The actual number of ransomware malware instances that ACTUALLY do this is small. Most simply go for known files on the system drive and either ignore backup image files (too large to work on) or external drives or both. Yes, it absolutely CAN happen, but right now the likelihood remains low, in my opinion. It’s my opinion that it’s more important to leave the external drives connected so that backups happen regularly, rather than having to rely on your memory to remember to reconnect them. If anything, I’d prefer to rely on your memory to every-so-often take one of those backup images and copy it to a different drive, disconnect that and save it elsewhere.
Personally, I would format and lose it all before I would pay the bleeps.
I’m with you.
Absolutely Bill.
Good information, but don’t understand one step:
“Take an image backup of the infected machine”
Why would one take an image of an infected machine, and then restore it?
An image “before” the infection, fine, but after? Why?
That’s a just in case suggestion, in case you later find there was some useful unencrypted data on your encrypted drive.
Quoting Leo, “This is to preserve a copy of the machine in its current state, in case it becomes necessary and possible to recover something from it in the future.” Also note where Leo says that the ransomware possibly encrypts part of the machine. You may be able to retrieve some information from un-encrypted areas later.
I would not restore it. The reason to take an image backup is to make sure you have a copy of EVERY file on that machine, just in case, some day later, you realize that in fixing or restoring the machine you deleted or lost a file that mattered. Then you could extract that file from the image.
Hi Leo, Thanks for the article. One comment: I’ve heard some ransomeware will also encrypt any attached drives, mapped drives and/or online storage. So, if people are using these for backups, is it important to remove their connection to your PC when not backing up? Thanks!
That’d be this article: https://askleo.com/will-malware-infect-the-backups-on-my-connected-backup-drives-as-well/
You might want to lOOK at you syntax (wording) here:
“Take an image backup of the infected machine.”
Once it’s ‘infected’ The backup will do no good.
A lot of armatures will read that wrong and wonder whether they’re idiots…or you are.
I’ll reiterate as I said in another comment – this is exactly as I intended. I want you to take a backup image of the infected machine before you begin repair/recovery attempts. Why? So that after you possibly overwrite it by reinstalling or reverting to a previous backup you stand a chance of being able to recover files from it in the future. Specifically you’ll be able to recover any files that were not encrypted by the malware. There’s also an outside chance that perhaps someday the perpetrators will be caught and the encryption keys made available – in which case even saving the encrypted files makes some amount of sense, particularly if they’re valuable.
I’ll say it again: Take an image backup of the infected machine.
It’s exactly what I mean.
DOES YOUR REFERRAL TO AN “IMAGE BACKUP” REFER TO A BACKUP OR A CLONED HD? I HAVE USED ACRONIS TRUE IMAGE ALONG WITH A HD TRAY AND A HD DOCK FOR A LONG TIME NOW AND KEEP AT LEAST TWO CLONES MADE WITH THIS SYSTEM. BOTH ABOUT TWO WEEKS OR LESS OLD.
I TEST EACH CLONE WHEN I MAKE IT TO BE SURE IT WORKS. IF CONFRONTED WITH RANSOMWARE WOULD THESE CLONES WORK? WHILE SETTING THIS UP IS NOT CHEAP IT SEAMS TO BE A SOLID SOLUTION
YOU OPINION PLEASE
An image backup is a copy of everything on your hard drive necessary to restore your system to the state it was in at the time of the backup. It includes all of the file, the OS, and programs and settings from the system. A clone includes all of that plus the free space and empty sectors on the drive.
A clone or an image backup would be equally capable of restoring your system after a ransomware or other malware attack. The essential difference is that an image backup would take up much less space and would take less time to run the backup.
Leo doesn’t talk much about cloning as there is no advantage of cloning over imaging.
I have been turned on to a program called CryptoPrevent, by Foolish-IT. I’ve been using it for about a year now, but I’m not even sure it works. It changes some stuff in the registry which is supposed to prevent being infected by crypto-malware. It came highly recommended though, and it’s really easy to use. Anybody have experience with CryptoPrevent, good or bad? Does it work?
CryptoPrevent is a reputable piece of software. It can protect you against one kind of Crypto Malware. It doesn’t prevent against all Crypto attacks, so you still have to exercise caution on the internet.
Why Haven’t You Mentioned CryptoPrevent
The author of the CryptoPrevent software has an interesting comment posted in the comments section of the article.
In one corner of the office I have an old laptop (running on XP) which I turn on once a week for a few hours. It syncs with my cloud service and I then shut it down so that I always have a safe place where my files are stored and recoverable. I think cloud service companies should not allow re-encrypting files on their server once they are stored there as they are already encrypted
It’s not a question of the malware encrypting files on the cloud server. Encrypting any files on a cloud server is not technically possible unless the hacker hacks into their server directly. The problem occurs if the encrypted files are uploaded to the cloud server replacing the good file.
Since this software has to execute to encrypt your data, how does it do that without prompting for permission? I had a clicker install a Chrome browser on my computer and I assumed it used Google updater authority to do so (I didn’t click any emails to start it and I don’t have Chrome installed). I actually saw the command boxes briefly pop up when it installed but Security Essentials did not find it until I ran a full scan several weeks later. Sometimes you shouldn’t ignore random command boxes. I was clicking information on a farm equipment site at the time so I suppose they were hacked. The actual files were located in a Local App Data folder. I have since been told that programs can execute from these folders without a prompt in some cases. Java is not installed on the computer. I understand that if you are not logged on as an administrator, these guys shouldn’t be able to execute without prompting for administrator authority. Since I normally use my computer as an administrator, I set Local Security Policy, Software Restriction Policies on the %localAppData% folders to prevent execution out of these folders. I back up important files to an external hard drive, I copy really important files to Onedrive (which is NOT set up to sync with my computer) and my email is all stored on an external Exchange Server. The real question is, how can ransom ware or clicker software install and run on your computer without asking for some authority?
The clicker app was one that installs an invisible Chrome and clicks web sites. I am not sure that it ever executed since the network never loaded up but Chrome was installed. Security Essentials missed it and would only flag it on a Full Scan.
The thing to remember is that hackers and thieves are smart, and they are quite motivated to come up with systems that work for their scams. Yes, being vigilant is a great idea!
User Account Control is designed to block execution of program installation and programs which get access to low level system areas on your machine unless you give that application permission to execute. Unfortunately, like all other security methods, it’s just one more fallible layer of security. The best protection is to have as many layers of protection as is practical. The most important layer is the one between the computer and the chair. Install and use common sense.
Internet safety: 8 steps to keeping your computer safe on the internet
Step 5. Educate yourself is probably the most important step.
Thanks for the info. However much more detail is needed. We need a complete list of ALL programs, no matter how few there may be that can possibly decrypt an encrypted file. And and maybe even more important a way is needed to identify which program did the encrypting.
In my case my client just got infected two days ago, 3-14-2016. In this case the files seem to have been left with their original names and extensions.
In the folders with encrypted files there is an html file named “File_encrypted-read_me.html” this file explains how to pay the ransom. There does not seem to be any .txt files with same message nor any list I can find of the affected files like some ransomware strains use.
Some of these symptoms seem similar to what I seen reference with the new Locky strain, but not all of them. Any help identifying the flavor of ransomware would be much appreciated.
Thanks,
Ralph
There is no list of programs. The hackers could easily have written their own, for example. Lazy ones will use PGP/GPG variants.
I have the same problem, as Ralf, I got infected on 4-5-2016, and the files have remained in their original names and extensions.
I received, a png, txt and an html file explaining how to pay the ransom, and if I don’t pay it by 11th april 2016, the price will be double… this is so strange!.
I would be grateful if any help is provided identifying the problem and getting it solved!!!!.
Thank you!
Adem
Please read the article you just commented on: there is nothing you can do short of paying the ransom (which I strongly recommend you NOT do), restoring your machine from a backup taken prior to the infection (which I hope you have), or reseting your machine completely.
The lesson here: back up back up back up!
Hi Leo
What do you think about Kaspersky ransomware Decryptor, https://noransom.kaspersky.com/
can decrypt encrypted files?!
More friends and me, we have been infected computers with Cerber Ransomware and blocked any file.
I tried with System Restore, but it just was affected by malware and can not restore files !
Now is not a decrypter for Cerber to Kaspersky,but maybe in the future will make one to decrypt-unlock all files !
It cannot decrypt ALL ransomware files. Only those variants for which the keys have been discovered. So it may, or may not, work.
Leo… as easily how encrypted in a minute tens of thousands of files, in the same way it should
as IT specialists to decrypt !!! so we can say that IT specialists they are less intelligent that hackers ?!!
The encryption methods used are very likely off the shelf encryption algotithms adapted for criminal purposes. Those algorithms produce encrypted files similar to what the military uses. It’s not that the hackers are smarter than the experts. That’s just the nature of encryption.
Mark Jacobs…I was not referring to the nature of encryption,
but if specialists IT are more intelligent than hackers
who created Ransomware Cerber, how is it that after a year failed to make a decrypter
for a restore files affected millions of computers worldwide.
I mentioned the nature of encryption, because it is key to the issue of ransomware. If it were possible to crack ransomware encryption in a year, that would mean any and all encryption would be easily crackable.
Because that is the nature of encryption, as Mark stated. Good encryption simply works that way.
Mark …you really think someone stood for years
just to create a virus encryption for different extensions ?!
Let’s be serious ! and not invoke on other reasons !…
today is made CRACK easily to almost any new program appeared
on the market.
No only that passed months when he appeared this virus
but this Cerber Ransom infect computers in present !
around the world…and the autorities,what i do ?!
I don’t understand exactly what it is you’re saying, but just saying “it can’t be” doesn’t mean it can be. It IS the nature of encryption that done properly hackers can do it and in such a way that it cannot be reasonably cracked by current technology. Getting frustrated about it won’t change the way things work.
Leo…ie you’re telling us that there is not technology
for decryption Cerber…but someone or hackers have
such technology !!! How is that possible?!
Any machines,program created by man can be
changed, adapted, copied,cracked etc…
I hope that people with good thoughts
to repair soon these harmful effects.
Lulian, you are not understanding encryption. The difference is not between how intelligent IT specialists are and how intelligent hackers are. The difference is between encrypting and un-encrypting. It’s very easy to encrypt a file (a stupid hacker, or a stupid IT specialist could do it very easily).
On the other hand, if a file has been properly encrypted then it can’t be un-encrypted using today’s technology without the password… no matter how brilliant the hacker or IT specialist may be. There are things such as brute force attacks and blind luck which may help a hacker find a password, but short of that, good encryption locks up a file.
The technology exists – we all have easy access to it. What we DO NOT have, and that they do, is the decryption KEY. It’s like having a lock on your door for which you do not have the key. The lock is the technology that you cannot break. Unless you have the key. When you pay the ransom, the hackers give you the key.
I think I’m beginning to understand what you’re getting at. Standard encryption if done with a long enough key is uncrackable by all but the most sophisticated 3 letter agency level crackers. You can even download and install software that effective. The creators of ransomware can decrypt the files they encrypt in the same way that you would be able to decrypt and encrypted files you created because they have the keys they used to encrypt the files in the first place. They wouldn’t be able to decrypt any files created by other hackers because they wouldn’t have the keys.
Leo & Connie…no safe deposit box from the world,
is not safe !!! can be craked, after some time.
Any thing created by man can be deciphered,
copied,because they were made with human tools,
not extraterestrial.
This ,,miracle,, key can not be kept in secret,
since demanded ransom money, and then gives
the key those in need…!!!
So impossible, can become possible,
due to circumstances,facts !!!
As you wish.
After being attacked I found out that “zip” files were not affected. So maybe importent files could be saved in a “zip” file, to be opened again after an attack.
Unfortunately, this isn’t always true. Ransomware encrypts whatever its programmer tells it to encrypt, so that’s no guarantee they won’t encrypt zip files. I use 2 methods to allow recovery from ransomware which I’ve been using long before ransomware was a gleam in the eye of hackers. Dropbox and some other cloud storage programs keep copies of all changed files for 30 days, longer if you pay extra. In addition, I copy my backup files to other removable disks which I only attach at backup time.
A note to this: Yes, it’s possible for ransomware to encrypt the files in your dropbox. However, Dropbox itself keeps a backup of all your files that you can access fairly easily.
That’s what I meant by “Dropbox and some other cloud storage programs keep copies of all changed files for 30 days,” Go back enough generations (in most cases probably only one) to recover the good versions of the files.
It all depends on the specific ransomware. Some could affect .zip files.
you can help me to decrypt my file
my file have
FILENAME.xlsx.id-20492BE3.{email address removed}.xtbl
Sorry, we can’t. Read the article.
Question, why Internet companies who profit of millions of dollars
annually from subscribers, do not have firewall, antivirus, antimalware,
advanced threat protection,etc to filter what comes on the network
so not reach directly to subscribers,viruses, malware etc.
As people may well find this article when looking for a solution, it really should be updated to provide them with accurate information.
“A file encrypted using public key cryptography is essentially uncrackable, unless you have the matching private key. And needless to say, the hackers do it right.”
Actually, hackers very often do it wrong and include flaws in their code enable security researchers, usually at antivirus companies, to work out how to break the encryption. Consequently, the researchers are able to create decryption tools, which are always made freely available, that enable people to recover their data without needing to pay the ransom. There’s a whole slew of these tools hosted at No More Ransom Project which a collaboration between Europol’s European Cybercrime Centre; antivirus vendors such as Emsisoft, Kaspersky and Bitdefender; as well as various other groups and organizations.
https://www.nomoreransom.org
It may also be good to include some actually useful advice – which this article doesn’t currently contain – as to what to somebody should do if they’re impacted. For example, firstly, they shouldn’t let an antivirus product delete the ransomware executable as, without this, security researchers may not be able to work out what encrypted the files and, consequently, also be unable to work out how to decrypt them. Secondly, they should seek advice not from you or this website, but from an antivirus vendor – you know, the actual experts in this stuff – who’ll be able to advise them on the best way forward. Many antivirus companies are willing to provide no-cost help to both customers and non-customers alike.
Just wanted to vote for DON’T PAY THEM!!! $$$. My son’s Father in law is an engineer and he got nabbed. It can happen to anyone although perhaps some aforethought, education and experience should help. I received some of this early on in my computer life when I started selling online. Anyway the ‘rest of the story’ is that he did pay, they strung him along, he paid some more, they strung him along, he NEVER got anything back!!! Just a little story reminiscent of Paul Harvey’s “The Rest of the Story” genre. Does anyone remember him?
Addendum. I didn’t mention the $ range. It was in the $4k range.
Hi Leo;
My girlfriend opened a file and had all her files encrypted and had the html file that told her where to pay to get the key. She was devastated as this encrypted her entire masters program. She didn’t back-up her files (which she regularly does now). What I did find helpful was all your articles on malware, spyware, ransomware, etc.
The one thing that I did find about this attack is that it must have been a lazy hacker. When the files were encrypted, the original files were deleted. Therefore, all the original, unencrypted files still existed on the hard drive, in their original format. I first created a clean boot USB drive, and then copied over the deleted files to another drive. Then I installed every anti-spam software I could find (recommended by you). I then spent days, installing, processing, cleaning, deleting. Once I was sure that there was no more malicious programs on the computer, I started to delete the encrypted files. Once they were deleted, I ensured that I found them and deleted again, so that no presence of them ever existed. Finally, I had to restore all the files (several thousand of them) back to the hard drive.
She was lucky in that I could restore her computer without wiping it clean. This might be a process that others can use too.
She was VERY lucky to you have you helping! Well done!
“ Wipe the machine and install Windows from scratch.”.
Will Microsoft supply a download at no extra charge, bearing in mind that hard copies no longer supplied by them?
Depends on the version of Windows, but for Windows 10 they already do: Where Can I Download Windows?
The download is free. Where Can I Download Windows?
If you have Windows 10, the downloaded OS should activate automatically. If you have an earlier version, you’d have to have the activation key. You can run the Magical Jellybean Keyfinder or Belarc adviser to find your key before reinstalling Windows.
Just Thinking if you are running the latest version of UBUNTU then you have the encrypting file system so if your have created your public keys which should either 4096 or 8192 bit keys then you should be safe. One other thing if You have GnuPG and Seahorse installed then it should be possible to use the encryption key to recover the decryption key by importing the encryption key and then syncing to try and recover the decryption key, not sure but it should be possible.
What ???
I’m not understanding how this could possibly work. That you have an encrypting file system is irrelevant. When ransomware encrypts, they use their own public/private key pair, so you would still be unable to decrypt, or recover their encryption key.
They can still encrypt your encrypted file!
Yes, that’s an important point. There have been a few comments from people suggesting encrypting your files to keep them from being encrypted by malware. This simply won’t work.
Ahh, the beauty of sandboxing.
About ten years ago I had multiple screens pop up (on my Widows XP machine) that said my files were encrypted and that I had to pay to get a key.
I looked at the screen and said “you wanna bet?”
I couldn’t even close, or exit, the windows that popped up.
Press and hold the power button to force a shutdown, start it back up, and all is good again.
The beauty of the sandbox.
I believe most of the articles that Leo writes are for the average and below average computer users. Or, he does as much as possible to make it understandable for every computer user. We appreciate that. On these terms, comments made on this forum should be made as simple as possible so every user can benefit from them. We have to remember that the majority of the people that reads these articles are just average or below average computer users.
Being a total novice I would ask a question betraying my ignorance. That is if you had an unencrypted file and it (the same) in encrypted form could you extract the key from the encrypted version? If so is there software to accomplish this?
Not if they are doing encryption correctly. A good encryption algorithm is very complex and designed so that it wouldn’t work. It’s not like those Jet Jackson decoder rings.
No. Not with modern/proper encryption algorithms. With poor algorithms it can be If I recall correctly, it might even be the reason WEP encryption for Wi-Fi is so easily broken.
i am infected with ransomware that have a .diysw extension!
Any help for that?
crypted all my photos and videos
Read the article you are commenting on.
Just thinking if you run Linux plus GNUPG and have the Seahorse application can you not import the Public RSA key into Seahorse and have spit out the Secret RSA key and finally use your encryption decryption package with the recovered Secret RSA key to recover your encrypted documents.
Unless you have the secret key, the ransomware program used to encrypt the files to, you can’t get in. If there were any other way to get in, all encryption would be crackable.
The public and secret keys cannot be calculated from one another. (SOME secret keys package their public keys within the same ‘key’, but they remain two separate things.)
So no, you can’t import a public key and somehow spit out the corresponding secret key.
Is it not true, Leo, that quite a lot of the “Ransomware” malware might not actually ENCRYPT your files, but might just “relocate” them by changing the pathway and name to a new “location” on your system? Just because the “bad guys” tell you your files are encrypted does NOT believe they in fact are, nor that you should believe them. They are, after all, liars and thieves, are they not?
I’ve never heard of any malware that simply relocates files.
Ransomware encrypts files. Otherwise, there would be dozens of articles on how to recover from ransomware by searching the disk or running Recuva.
Hi Leo, been with with you for decades, spent 14 years in BC and my soul never left! Alas, my carcass is now far removed…
Backups and images, the daily bread and butter of living on the net, no doubt about that. Daily routine, slavishly observed and fortunately so far not needed. Yet there are some paid for antivirus programs (Emsisoft, Bitdefender etc.) that offer, and often even guarantee, a recovery from successful attack. Do you know, or think, that promise is realistic?
Great thanks for the ‘accident warning’ – ever so real but alas too late for me, I spent 5 month in virtual isolation for lack of preparation. Oh well, life goes on.
Regards and Best Wishes Jeremy
I wouldn’t rely on that guarantee. Unless you have a backup, there’s no sure way to recover from malware. An antimalware program can remove the malware and restore things back to normal, but only in some cases. We recommend using Windows’ Defender which come preinstalled and automatically activated.
Recomdations for the best backup software
I recommend either Macrium Reflect or EaseUS Todo.