A useful tool, broken.

A reader recently informed me that Twillio, the folks that own the Authy two-factor authentication app I’ve been using and recommending for years, has elected to stop supporting the desktop application. Authy will be available as a mobile/smartphone app only.
That’s… disappointing.
I went looking for an alternative. I didn’t find one until I looked at another app already on my computer that fits the bill almost perfectly.

Replacing Authy desktop
Although Authy is discontinuing its desktop app, I’ve discovered that 1Password also supports two-factor authentication (TOTP) codes! It already syncs across devices, offering a seamless alternative for managing two-factor authentication.
What is Authy?
Authy is a Google-Authenticator-compatible application that provides the TOTP (Time-Based One-time Passcodes) used for two-factor authentication.
Next to a hardware key such as a YubiKey, this type of two-factor authentication is perhaps the most secure, and certainly the most recommended, form of 2FA.
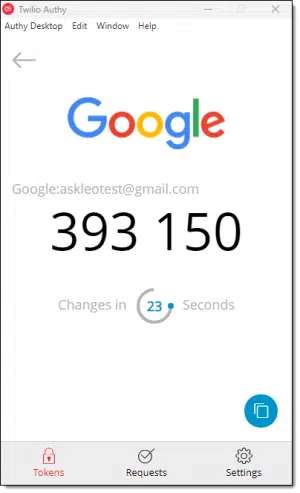
Authy provides seamless synchronization of your TOTP codes across multiple devices. When you set up two-factor for an account using one device, that two-factor is then made available across all the devices on which you have Authy installed.
Until March 19, 2024 that includes the desktop application, shown above. After that, it’s Android and iOS only.
They’re taking away what I consider to be its most useful feature.
But it turns out I already have that feature elsewhere.
Help keep it going by becoming a Patron.
1Password to the rescue
1Password, the password manager/vault I use, supports Google Authenticator-compatible two-factor TOTP codes.
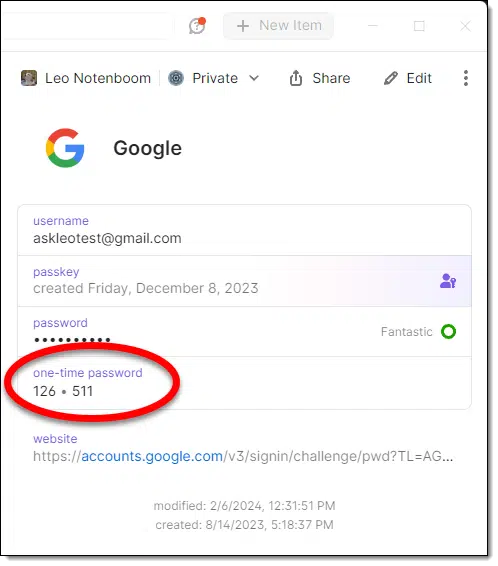
In fact, when signing in to an account on the desktop, in addition to filling in the password for you, 1Password will often automatically fill in the subsequently requested two-factor code. (If not, it’s a simple copy/paste from the 1Password app.)
And of course, 1Password is on all the devices I care about: my desktop computers and mobile devices.
Problem solved.
Setting up 2FA in 1PassWord
There are two approaches to setting up two-factor authentication in 1Password.
For many services, 1Password already knows if TOTP two-factor authentication is available. It’ll simply prompt you to set it up when you’re examining the account in your vault (either mobile or desktop).
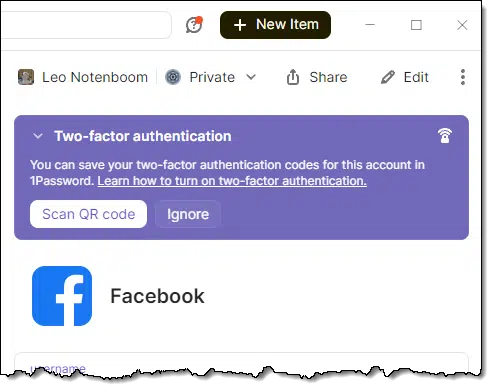
Click on Scan QR code offered in the image above, and:
- On mobile devices, 1Password will open up a camera window to point at the displayed QR code.
- On the desktop, 1Password will scan windows visible on the screen for a QR code and automatically process it.
- If it can’t, it will also examine an image stored in the clipboard. You can take a screenshot of the QR code (which I recommend doing anyway), and copy it to the clipboard for 1Password to process.
For accounts that 1Password doesn’t yet recognize as two-factor capable, you can edit the entry and add a One-Time Password.
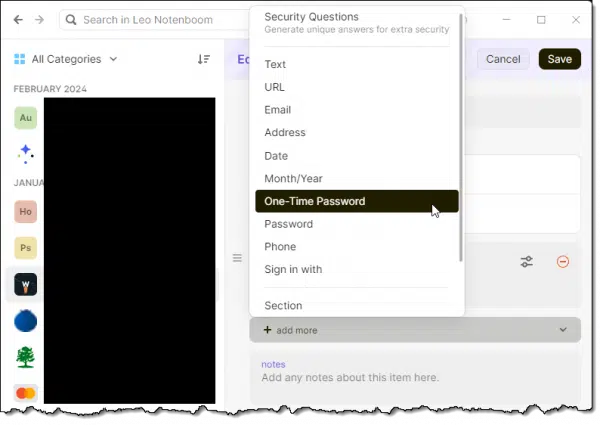
This will then walk you through the same steps as above to scan the QR code1.
Do this
I’ve been slowly moving my two-factor codes out of Authy and into 1Password. Eventually, I expect Authy to have one and only one code in it: the two-factor code for 1Password. I’m OK with that being on my mobile devices only.
If you’ve been using Authy and you already use 1Password, you may want to consider starting the move now. If you’re using a different password manager, check with them to see if they have this on their radar at all. The demise of Authy desktop may motivate them to do so.
Be sure to subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: 1Password will also let you enter the text code if scanning the QR code isn’t working or available.





I read your article on Authy & 1Password. I am 80 yrs old & wish I could do what you suggest. I know it asks for 2 codes on some things I do on my phone. Didn’t know it could be done on my desktop too.
What type of tech should I find to help me put this on my computer.
I have read askleo for many years.
The premium versions of Bitwarden also have a built-in authenticator. It also allows users to either scan a QR code or enter a text code.
Excellent. Thanks for the info.
Here’s a great solution for this issue if you use an iPhone download the cloud control panel from the Microsoft store it has 2fa code support now. for google phones, you can use the Chrome password manager to sync between devices that also supports 2fa as well
I’ve opted to use Yubico Authenticator:
https://www.yubico.com/products/yubico-authenticator/
since I already own several Yubikeys that I use to unlock my password manager (Password Safe https://pwsafe.org/ ) and I wanted the option to be able to access my 2FA codes from my PC and from my Android phone.
Yubico Authenticator is available for Windows, Linux, Android, iOS. The initial QR code secret keys that are used to first set up an online service, are stored on the Yubikey, rather than in the app.
I didn’t like the idea of not having my 2FA codes backed up or solely based on a single smartphone. (And of course, when I first set up Authy, I didn’t know to save the secret keys for most of the accounts and in any case, Authy doesn’t have a secret key export function to make it easier to migrate to another app).
If anything happened to my phone, I would need to run out and spend a wad of $$$ to replace the phone (and make a snap decision as to which phone to buy as the replacement), right when I might really need to access my 2FA codes for logging into online services. But since I can’t migrate secret keys from Authy to a new app, I’d be hooped.
Of course, I could perhaps buy a second inexpensive phone to use for 2FA backup using another app such as Aegis and set it up, but that still entails more expense and reliability concerns (I figure a phone is more likely to fail than a Yubikey). And since I hardly use my cell phone for very much (I do most of my online activity on my PC because I like using a full-size monitor and a real keyboard), I can’t really justify the expense of having more than one cell phone.
I just spent the past couple of days setting up four Yubikeys (redundant copies, one of which is always on my key-ring) to work with the Yubico app. I’ll see how things work out going forward.
I’ve been using the Yubico Authenticator for a couple of years now. Yubico has a desktop version available from their website and recently published an app in the Microsoft Store. There is also one in the Google Play Store for Android phones if you have a NFC capable Yubikey.
I keep copies of the codes for my Yubikeys in a text file and when I make Yubikey backups it is just a matter of copy/paste for setting up the keys. Most websites will have a code under the QR code when setting up the authenticator app or will display one if you select can’t read the QR code.
Dear Dave B thank you so much for being another person who does not ‘use their mobile handset for much’. There are SO many people who can not use a handset – they are too small, the touchscreens are very difficult to use, if you have dexterity or vision challenges of any kind. Not to mention how expensive these so called ‘smart’ telephone handsets are! You can go to a library to use a computer but there are no mobile handsets available in a library.
Hi Leo, nice article!
I use A LOT of 2FA and find this decision, just like you, a disappointing fact.
However I can understand some technical reasons why. As a programmer, the most concerning item is security. In older Authy-versions for desktop it was possible (with a simple hack) to retrieve the TOTP-secrets in a Chrome-browser (ASCII and QR). I took advantage of the hack in that way that I was able to BACKUP all my totp-secrets. With those codes I made my own personal version of Authy-desktop.
Anyway, it is always good practice to backup the original totp-secrets (by clicking on ‘i have no QR-code scanner’ and copy the shown text in a safe place before scanning it with the mobile device.
I Hope it contributed a little 😉
I find it extremely annoying being put into the practical impossibility to sign up for certain services …
I am only using a desktop computer, without any mobile device at all.
As such, I don’t understand why there is no normal, simple way to be able to access your own accounts, on any type of service.
One simple example: without 2FA, I am not able to connect my desktop Outlook application to access my Gmail account …
Or … somebody already just wants to get rid of us … the “non-mobile” users …
very sad …
When implemented correctly, 2FA should only have to be verified once per device. Then the website should recognize that device when you access it from that verified device. That device becomes your second factor. Many sites use cookies. It usually asks if you want them to remember that device. Unfortunately, some websites don’t do it correctly, and if they use cookies, wiping cookies will require 2FA verification again. And some websites set cookies to expire after a time.
To access your Gmail account when 2FA is turned on, you need to either reconnect the account (one time, it’ll ask for 2FA), OR use a “app password” generated for you at the security settings in the Gmail account.
Dave – I use Yubikeys as well and got tired of all the steps to get a TOTP code. Find key, insert or tap to phone (twice) or laptop, type in 4 digit access code, touch key, then get code. Started using TOTP with my Bitwarden premium acct. as their TOTP codes are right there with the account logon info and password. Is there something ‘m missing? I like Yubico Authenticator but the hassle factor pushed me to BW.
Who doesn’t have their cell phone right next to their computer keyboard at all times? I have only used the Authy cell phone app for years, Android and iOS. Never thought about a desktop version for one second, so I for one will not miss it, never needed it.
I have to admit, until I read this article, I had no idea putting an authenticator on a PC was a thing. I only use my phone.
Claude “Who doesn’t have their mobile right next to their computer?” Sorry to hear you are totally unaware of disabled people who can NOT use mobile handsets!! Or the people who can NOT afford the $1000 for a handset that must be replaced when its battery dies, plus the $700 per year or more to connect it to the internet. Computers are available in libraries. People just forget, until they become disabled or unable to afford all these so-called ‘smart’ telephones, which cause so many problems!
https://help.roboform.com/hc/en-us/articles/115002729512-Enabling-Two-Factor-Authentication-2FA-for-your-account
That looks like it’s for your Roboform account, not the sign-ins you store in Roboform.
Dear Dave,
You ave convinced me that I should be using two factor authentication after many years of resisting and complaining about the whole idea. It made sense to me for banking but not for all the other web sites. I use Sync-cloud Sticky Password Premium on my Windows 10 PC and my iPhone SE (6) and after reading your excellent articles I am almost ready to go with Sticky Passwords system which uses the Google Authenticator installed on the mobile phone and desktop. Current versions of both and both devices using the same time zone (kind of important.)
I am 80 1/2 years old so I will proceed somewhat slowly rereading your article and the information provided by Sticky Password and Google Authenticator several times as well. Before proceeding I would be interested in any cautions or bad reports about either Sticky Password or Google Authenticator that you may know of, from your use of either, or your readers use.
Thank You,
Eric T.
Paxton, MA
Hi Leo
Yes,I was trying to set up Authy desktop 2FA and vexingly noted its looming demise. I set up2FA from my Roboform account which now autofills the 2FA codes and allows log-in to the chosen account.
Incidentally, the Google 2FA, unlike Authy does not time-out the “Enter Pin” screen after leaving it. This is the reason that I replaced Google 2FA with Authy. Please correct me if this is no longer so.
Will the codes from your mobile app still work for desktop know you won’t be able to copy and paste but to me that would be better than having to redo all web sites that i have set up on authy.
I haven’t had any experience with that, but there are a couple of comments here from people saying manually copying the key from their phone works for them.
I have used Authy for a long time and did not even think about if there was a desktop version or not because I always have my Iphone on me with Authy installed and its so simple to get the six digit code in the Iphone and enter it into the desktop application whether it is a browser, mail app, browser extension or whatever.
Hi, why wouldn’t you put the Password Manager’s 2FA in the Password Manager, i.e. why leave it alone in Authy?
Chicken and egg. You need the two factor code to open the password manager, but you can’t get the two factor code until the password manager is open.
(I mean, save the QR code or what not for safety, fine, but you’ll need a separate app to actually display the TOTP when you need it.)
Thanks for the info.
Just as I was going to sign up for Authy, for a way to access 2FA logins in case I lose my phone, I discover it’s going to disable the desktop App. I am primarily a computer user and while I have a smartphone, I have misplaced it and was not able to access my Password Manager nor any of my 2FA accounts.
It seems that many students at McGill University in Montreal don’t have phones (only Laptops) and have been using Authy as way to securely gain access to their accounts.
McGill’s IT dept. has also flagged this issue and posted a suggested fix, which involves installing the Zoho OneAuth Authenticator which is also capable of both desktop and phone 2FA.
Here is the link to that site, which has some detailed information.
https://www.mcgill.ca/it/channels/news/important-update-authy-being-discontinued-vendor-after-march-18-install-oneauth-continue-355536
Here is the link to OneAuth which lists its features and compares it to the other top Authenticators.
https://www.zoho.com/accounts/oneauth/authenticator-app.html
Zoho OneAuth sounds promising if their software does what it says. The fact that McGill recommend it is a big plus. It would be good to hear from users of Zoho OneAuth here.
Thanks for sharing this about Authy Desktop’s EOL.
I am a little surprised at your 1Password suggestion though. Functionally I realize that 1P can store the one-time passwords very well. However, doesn’t storing the one-time passwords for a given login in the same place (1P) as the user+pwd for the same login defeat the point of using a one-time password to begin with?
Thanks for your thoughts on this.
Already wrote on that topic: https://askleo.com/isnt-putting-two-factor-codes-in-my-password-vault-less-secure/
Note that the article incorrectly states that Authy will no longer work (“..As such, after this date, you will no longer be able to authenticate using the Authy application from your desktop computer.”..). It simply states the app is no longer supported. I just used it on my desktop on mar20, and it is fine.
Roboform now acts as a 2FA authenticator similar to 1Password.
https://help.roboform.com/hc/en-us/articles/4416928099213-How-to-use-RoboForm-as-a-2FA-authenticator-for-other-sites-and-apps
Hi!
I’ve found 2 possible free replacements: one is the Authenticator addon for Firefox (currently version 6.3.5) or KeePassXC (version 2.7.1 is the last to work on MacOS 10.14, if needed).
There’s something to be aware of, though: Authy Desktop.app 2.5.0 continues to work! Provided you accept the warning when you launch it…
I don’t know how (in)secure it is to keep on using it, as they all rely on Google-Authenticator service anyway, or am I mistaking something?
It’s safe. It’s just that if there will never be any updates to it. If something in Windows changes such that the app stops working, that’s it.