A friend of mine recently forwarded me an email he received that looked like it had come from me.
Except, of course, it hadn’t. It was a complete forgery, and not a very good one at that.
I am both slightly honored that I’m worth forging, and quite annoyed that someone actually did.
We’ll look at the message and all the clues it contains that make it a fairly obvious fake, and then generalize those clues to help you separate spam from legitimate email.
The message
Here’s a screenshot of the message. (Click on it to make it larger if it’s hard to read.)
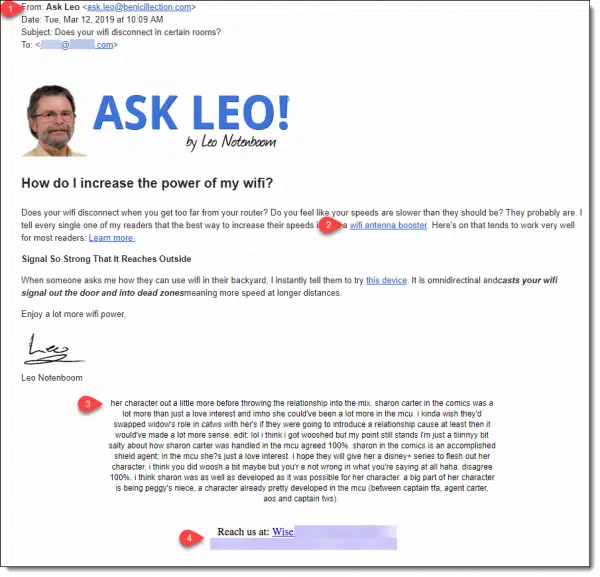
Let’s look at a few items in the message that indicate it’s a fake.
1: The header
If you look at the “From:” address, while it says it’s from “Ask Leo”, it’s not.
The faker manufactured an “ask.leo” email address on a completely bogus domain — a domain completely unrelated to anything I do. As far as I can tell, there’s no website there, either.
Email from me will always be “from” an askleo.com email address, or perhaps an aweber.com (my mailing list service) email address. In rare cases, you might get an email from @pugetsoundsoftware.com, which is my corporate identity.
I have no idea what this fake domain is all about.
Takeaway: Always watch the “From:” email addresses to make sure that they make sense with respect to whomever the email claims to be from.
2: The links
When I hovered over the links in the message, another clue appeared.
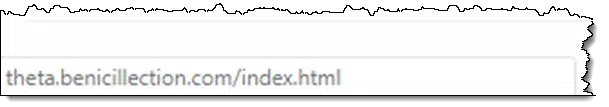
The links all go to a subdomain off of that bogus domain — once again, nothing related to Ask Leo! at all.
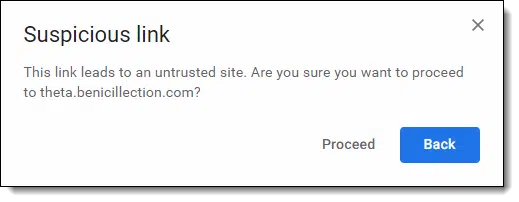
Gmail wouldn’t even let me click on those without warning me.
Links in any of my emails go to askleo.com-related domains, or in some cases, aweber.com domains.
Takeaway: before clicking on links, hover over them to examine where they go, and make sure the destination makes sense. And of course, if your email program warns you that the link is suspicious, don’t proceed.
3: The additional text
The additional text below “my” signature is another giveaway that this is pure spam.
This type of unrelated text — sometimes gibberish, sometimes coherent, but always unrelated — is placed into spam emails to bypass spam filters. The filters look at the text of messages to see how “spammy” they are. If there’s a lot of text that isn’t suspect, the filters are less likely to filter this email as spam.
Takeaway: if a message has a lot of seemingly random, unrelated text, it’s likely to be a spammer’s attempt to bypass spam filters.
4: The contact information
Near the bottom of the message is some contact information. I’ve blurred it out for reasons I’ll explain below, but it certainly wasn’t my contact information and didn’t appear to be related to anything else in the message.
Perhaps it made the message look a little more official, but it — like everything else — was bogus.
Takeaway: do look at the contact information at the bottom of emails you receive. Not only is it required in bulk email campaigns, it’s another clue you can use. If it doesn’t make sense because it’s unrelated to anything in the email, that’s another sign you might be looking at spam.
Items you don’t see
Help keep it going by becoming a Patron.
Me being me, I dug a little deeper than I’d expect most people to look.
The email headers you don’t see clearly indicated that this was spam. SPF and DKIM information — technical data used for just this purpose — had clear “Fail” indications.
The headers also indicated that the email had been sent directly from the bogus domain hosted on a popular shared-hosting site.
When I clicked on the links (don’t worry, I did so safely 
And of course there are things only I would notice: improper use of my trademark, the writing style, and even the formatting looks nothing like the messages I send.
What we can infer
Even though the email originated at the website of the bogus domain used throughout, we can’t confirm conclusively that the domain owner is at fault. There are two valid scenarios:
- The domain owner is at fault and is not very good at hiding his or her tracks.
- The domain owner’s website has been hacked, and someone else entirely is running this fake operation without his or her knowledge or consent.
I suspect the latter, but there’s not enough data to prove it. Had there been an actual website at the domain, perhaps we could make a few more conclusions. That there were subdomains involved (“theta”, in the examples) might support the domain owner’s complicity.
The contact information at the bottom? Very likely some innocent third party (hence my obscuring it); just something added by the spammer to make the message appear more legitimate.
Dealing with fake “Ask Leo”
As we know, “from’ spoofing is easy and rampant. There’s little to be done about that. (Technically this isn’t that, since they didn’t actually spoof my email address — just my name in the From: line.)
But blatant impersonation takes this to a whole different level.
So far, I’ve:
- Contacted the hosting service
- Contacted the registrar of the bogus domain
- Contacted the listed owner of the domain
As I write this I’ve not heard back from any of them, which is not surprising.
Depending on any responses, additional incidents that come to my attention, or additional information that comes to light, I may or may not take further action.
I do expect whatever happens next to cost me money.
At a minimum, the impostor did us a little service: their fakery provided us an example of things you can watch for to distinguish spam from legitimate email.
Thanks?
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!




Your use of the initialisms “SPF” and “DKIM” sent me scurrying to DDG. Ah, I see. What exactly did you do to make those authentications? How do I use those protocols to determine if mail isn’t authentic?
It’s …. complicated. 99.999% of the time it’s something your email provider does for you and it’s nothing you need worry about.
Only if you own the domain you’re sending from (as I, for example, own askleo.com) do you need to concern yourself. For SPF it’s a DNS entry, and DKIM depends on the email software on your mail server being used to send your emails.
Excellent article, Leo, for which many thanks.
When I receive a suspicious message and if I feel inclined and have the time, I search the “hidden” headers. Accessing these varies between e-mail clients but is relatively straightforward in Outlook. Over many years I’ve learned to copy IP addresses and input to a LookUp service to find out more. The results can be both fascinating and illuminating. Looking up the IP address in the last occurrence of a line which starts…”Received: from” often tells me from where the message originated.
“The redirect included someone’s affiliate link, so had I purchased the device, the spammer would have made a buck or two. (The shopping site seemed legitimate, but I didn’t dive too deeply into it.)”
Did you consider (if the shopping site was actually legitimate) letting them know the affiliate code of the spammer? That is against the rules of the legit sites.
I actually did think about it but elected not to. It wasn’t a site I recognized, so any contact of any form would only increase my personal exposure. My guess is that the site was legit, and that contacting would have been at worst ineffective, but by that time I’d already spend enough time on the problem.
I frequently encounter a similar scenario that isn’t quite the same: I get an email from a friend or mailing list; it’s legitimately from the person and includes a link to something like “You won’t believe what these cute Corgis do.” The link is on a Web domain that I don’t recognize. I assume that my friend/list manager has viewed the video and suffered no ill effects, but it’s possible that a bad actor loaded software on their machine that they don’t know about … yet. Should I just delete the message and reply with a noncommittal “haha”? What if I really REALLY wanted to see the cute Corgis?
If the return address of the email (not the displayed name) really is theirs) I would consider asking them what it was.
In addition to the true email address (these usually come from some spam address), the fact that it mentions a specific breed of dogs that you are interested in is a good sign. The malware people don’t usually get specific since that is a give away to people who do not have that interest.
Honestly, it depends on the specifics. If you don’t trust the destination, don’t click. Simple as that. You can’t really assume your friend has even sent the mail, unless it’s clear that it’s a topic your friend would really, honestly, email you about. Their machine may not be compromised, because they may simply not have sent the mail at all — it could be nothing more than spam.
Hi, Ask lEO , sorry for the fake emails from fake Ask Leo Com.
How to be sure, if one is oening your lilke fake site and browse to the suspicious sites
The technical information you provide may give an idea of the problem, but for not savvy technical persons, this would be difficult to understand. Anyhow, glad that you immediately brought tthis to the notice of your all email contacts.
Thanks , if any solution is there to applyl , please say. Please also , include a para on this on every news letter in future, as this email may have been missed and marked as read by users.
Thanks
That was an easy one to detect. There are plenty of much more devious phishing attempts around. Sorry you were so targeted.
Did you also contact the company that was selling the antenna, since they theoretically could identify the person who would make that “buck or two” from the sale had you clicked it?
Thank you Leo for this post. Do you think the spammer just sent fake emails like this one randomly to everyone or if they actually have known who subscribed to ask leo newsletter and sent these emails to subscribers specifically? Thanks.
I don’t believe they know who’s subscribed. That would actually require a data breach that has not happened. This is typical spam sent randomly that just happened to hit a friend of mine.
I’m a subscriber, and I didn’t get the fake email.
Yeah, it wasn’t sent to subscribers. It was just random spam. The bad news is that it’s probably still being sent out. This article is a warning for what to watch out for in general but also if you receive specific email, you’ll know it’s a scam. This one might be able to fool a Newsletter subscriber or two who are used to getting newsletters from Ask Leo!
Hi Leo,
You mentioned contacting the domains/service.
That didn’t increase your exposure?
I wouldn’t expect so.
Thanks for the article, I’m very sorry this happened to a good website like this one. I might have even fallen for this, since have recently been researching ways to speed up my router, inasmuch as my Internet service is only 768kb, although it is most affordable and a price-protected plan, and it works reasonably well for my needs. (This issue might indeed be a subject for a future Ask Leo article, as I understand that a good percentage of the US population is stuck with Internet speeds similar to mine …).
I occassionally get an email from my bank that is not from my bank. Pay attention to those headers. Although the bank that I use is somewhat large it is not a well known bank by any means. Jerks that put these emails out know that it is a lot like going fishing (phishing). Sometimes you get a bite sometimes you don’t but it is the big fish that you are trying to catch that makes it worth going fishing in the first place.
Another clue for me would be the misspelling in the body (if you already mentioned it, sorry, I probably didn’t read the article closely enough).
“Here’s on that works . . . “
I usually get the following- an email message from someone who hasn’t emailed me (or actually talked to me) in ages, or else, I keep getting “invites” from someone who is on facebook (this after I had already deleted my facebook account). I told the latter person that they’ve got something weird going on with their account, but they don’t do anything about it, so it usually ends up in Ye Olde Spam Box. The former emails happen and it looks like it’s from the person(s), but I’m guessing some virus hacked their address book and started sending stuff to everyone they’ve ever emailed.
I can’t find anything about a facebook virus (I eschew facebook for numerous reasons) online.
Leo, you mention hovering over the link to see where it’s really sending you. This can be done on iPhones (and I assume Androids) by touching and holding the link. After which, a menu screen will open and allows you to view the hidden address. HTH!
I’m a bit surprised that by now, spam filters haven’t been programmed to recognize the gibberish in spam. So far, it’s up to the spam filter between the chair and the keyboard to recognize and mark these as spam. The computer users’ discernment is a major component in defending against spam, malware and phishing.