You may already be using Bitlocker.
I do use BitLocker.
While it’s safe to use everywhere, I use it only in some places.
Don’t take the fact that I use other encryption tools as well, like Cryptomator, to mean I’m not using Bitlocker. They’re different tools for different purposes.

BitLocker, Cryptomator, and when
BitLocker encrypts your entire disk, making data safe if your device is lost or stolen. I use it on portable devices but leave it off on desktops for easier data recovery in case I ever need it. Cryptomator, on the other hand, encrypts specific files in the cloud. Different tools serve different needs.
BitLocker’s whole disk encryption
While you can use it in other situations, BitLocker is primarily known as full-disk encryption.
This means that everything on your hard disk is encrypted, including all your files, temporary files, swap and paging files, the registry, and so on. When you’re signed in to Windows, this all happens automatically. You use the files in their unencrypted form; encryption and decryption happen as the system writes or reads files to and from your disk.
Note, though, that when you’re signed in, there’s no sign that files are encrypted. Everything is readily available in unencrypted form. It’s only when you’ve signed out, or when the disk is stolen or removed, that encryption makes the files inaccessible to anyone.
Do you know if your BitLocker is on?
The frustrating news is that you may use BitLocker and not even realize it. Normally, if you right-click on a drive in Windows File Explorer, you’ll have an option to turn on or manage BitLocker. If the latter, the state is obvious.
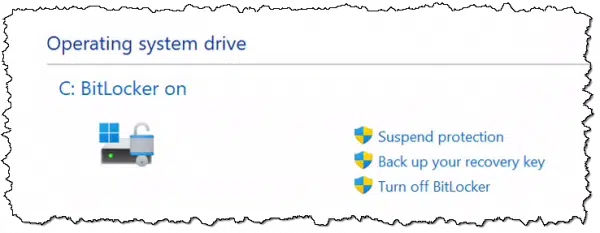
If, however, you’re running Windows 11 Home edition, where BitLocker is technically not available, your hard disk may still be encrypted. Quoting Microsoft:
Device Encryption is a Windows feature that enables BitLocker encryption automatically for the Operating System drive and fixed drives. It’s particularly beneficial for everyday users who want to ensure their personal information is safe without having to manage complex security settings.
When you first sign in or set up a device with a Microsoft account, or work or school account, Device Encryption is turned on and a recovery key is attached to that account. If you’re using a local account, Device Encryption isn’t turned on automatically.
Unlike BitLocker Drive Encryption, which is available on Windows Pro, Enterprise, or Education editions, Device Encryption is available on a wider range of devices, including those running Windows Home.
The highlights are mine.
The only way to see if this encryption has been enabled is to visit the Settings app. Within Privacy & security, look for “Device encryption”. If that setting is not present, your device doesn’t support it. If it is, it may show that your disk is encrypted whether or not you want it to be.
BitLocker: when I use it and when I don’t
My rule of thumb is simple: I use BitLocker on portable devices and turn it off everywhere else.
Here’s my thinking.
Portable devices (like my laptop) are subject to loss and theft as I travel. BitLocker provides an additional layer of protection for all the data on my laptop. My data is visible only if I’m signed in. Otherwise, there’s nothing a thief can do to access what’s there.
Other devices, like my desktop, aren’t subject to the same risk. One thing BitLocker (or any whole-disk encryption) prevents is forensic data recovery. I leave it off because the threat of theft is low, and I’d like the possibility of other forms of data recovery — even as simple as connecting the drive to a different machine1 — to remain.
The only exception: I choose a different, platform-independent solution (like VeraCrypt) if:
- The disk or device was portable.
- I want to be able to access that disk from other operating systems directly. (BitLocker is Windows only.)
So, why Cryptomator?
I also use Cryptomator.
While it is certainly possible to use Cryptomator only locally, I use it specifically to encrypt some data I put in the cloud. I use it to encrypt a single Dropbox folder where I place all my sensitive stuff (although it’s equally appropriate for OneDrive, Google Drive, or any of the other cloud providers that use an app to synchronize files between your computer and their cloud services).
This ensures that should someone ever gain access to my cloud storage, they would not be able to view the contents of those securely encrypted files.
And, yes, this has the odd side effect of having those files doubly encrypted when stored on my laptop hard drive:
- Once by Cryptomator.
- Once by BitLocker.
There’s no harm in this little bit of redundancy.
Do this
This is only semi-related to this article, but please:
- Understand whether your hard disk is using BitLocker (or “device”) encryption, as shown above.
- If it is, make absolutely certain you have your recovery key securely saved.
Ultimately, whether you need BitLocker whole-disk encryption is a decision you need to make based on your own risk assessment. My rule of thumb above is a fine start, but your needs may be different.
My guideline for Cryptomator is a little clearer: if you’re putting anything you’d consider sensitive data in cloud storage, encrypt it. Cryptomator is a fine tool for that.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: This is technically still possible to access if you have the BitLocker recovery key, but it’s an added complication that I see no real reason to take on.




This is interesting. My work laptop uses BitLocker and I have to put in a PIN to unlock it before it will boot. So I assumed my personal laptop was not BitLockered. After following what you said, I see that indeed my personal laptop is encrypted. So, as I understand it, the key to unencrypting is signing into Windows, correct? Which means that when I travel, it’s not just good enough to lock the laptop but I should actually be signing out of Windows, correct? Or is it only encrypted when it is powered off?
If you shutdown it’s encrypted. I can’t say for sleep or hibernate, though you can force a signin requirement on both.
The key is that the data on the hard drive is ALWAYS encrypted. It’s only when logged in that you can see it in unencrypted form.
Veracrypt can encrypt a drive, and is cross-platform. I’ve been using that on some KEY USB sticks. – I can access the data in Windoze, AND Linux.
Given the soon to be lack of ongoing support for Windows 10 I’ve been trying Linux and finding (with a few exceptions) it meets my needs. So programs that work cross platform are of value to me. I’m not aware whether it’s possible to use ‘Bitlocker’ on a usb device on a Linux system. Hadn’t thought to even attempt it, as VeraCrypt has been working well for me for years.
I’ll have to check out Cryptometer.
Thanks as always for your pointers and advice!
I do exactly what Leo does with BL and CR. BUT…I do have one issue with BL…the total lack of support. CR has a very active forum and I usually get a good answer within a day or two of posting a question (thankfully very few). It is monitored by people who really know the tool and can help troubleshoot.
BL on the other hand lands you in a vast wasteland if you get in trouble. I encrypted a portable drive and later formatted it. Now I can no longer get BL to work. I get a strange message about “bands cannot be not enumerated” that NOBODY seems to be a able to answer or resolve. Microsoft support is MIA so that drive remains unencrypted (bummer). I’d love to get BL back on it but no luck so fare.
This item prompted me to revisit my Cryptomator set-up, and I’ve discovered I’ve been doing it wrong. I’ve been putting unencrypted files into the encrypted drive Cryptomator created when I set up my vault, so they didn’t get encrypted. I now understand that I create a ‘vault’ by letting Cryptomator create its folder on my local machine, then when I unlock the vault, and make it available, a new virtual ‘drive’ appears in File Explorer. This virtual drive is where I’m intended to place files I want to be encrypted. Then, if I want to sync my vault ‘to the cloud’, I can sync the vault folder created by Cryptomator with my cloud service. This concept is so simple, I’m a bit ashamed that I misunderstood how I should set up and use a Cryptomator vault. If all this is unclear, I apologize. If you have any questions, please ask away, and I’ll try to answer correctly,
Ernie
Is cryptomator safe and secure enough to save sensitive documents like scanned copies of birth certificates, passport, life insurance policies etc in onedrive?
Please kindly reply Leo. I watched all your YouTube videos but still hesitating on trusting to put such sensitive documents on cloud.
I have multiple physical back ups but need cloud back up in case I need to access such documents on the go using cryptomator ‘s android phone app.
Than you in advance.
Jay W
I believe it is, and in fact have exactly those documents placed there.