It might be easier, but it’s available only once.

So you’ve set up two-factor authorization for your most important accounts — good for you! Then you realize that if you lost your phone (or whatever device you use for the 2FA), you wouldn’t be able to use it to prove you are you, and you could get locked out of those very important accounts.
In a previous article, I described how losing that second factor for a two-factor authorization (2FA)-enabled account isn’t even close to a disaster. In that case, you go through the inconvenience of an account recovery, disable and re-enable two-factor, and you’re good to go.
If you’re using Google Authenticator-based two-factor, there’s an even easier way — but you need to plan ahead, as the technique relies on something that is available exactly and only once.

Losing your Google Authenticator-compatible 2FA
If you prepare ahead of time, losing your Google Authenticator-compatible device is only a minor inconvenience. Screenshot the QR code or save the secret string during setup and store it safely for future use. This allows you to easily set up on a new device while keeping your accounts secure.
Setting up TOTP 2FA
When you set up Google Authenticator-based two-factor authentication, also known as TOTP (for Time-based One Time Passcode), the process is as follows.
- The account you’re setting up displays a QR code or a longish string of letters and numbers representing a “secret”.
- You use your phone to scan the QR code, or you copy/paste or enter the secret string into the Google Authenticator-compatible application, which then begins showing six-digit numbers that change every 30 seconds.
- You enter one of those numbers to confirm that the relationship has been set up properly.
- You’re done. Two-factor authentication is set up for that account.
Pretty simple, except that after you’re done — in fact, often before you’re done — the QR code or secret string is nowhere to be seen.
And they’re not recoverable.
Help keep it going by becoming a Patron.
Of QR codes & secrets
That QR code often looks like this.
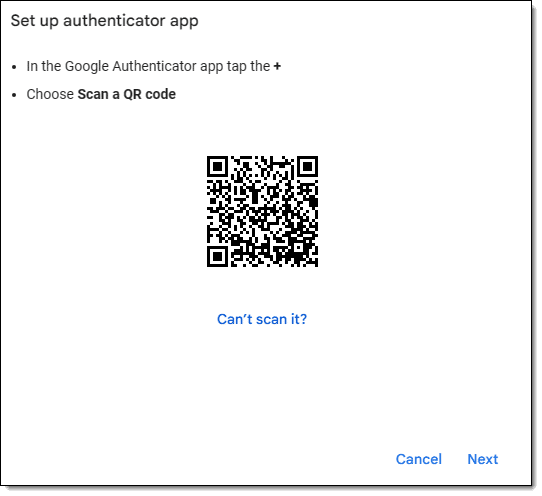
Or, if a string/secret code is shown, it might look like this.
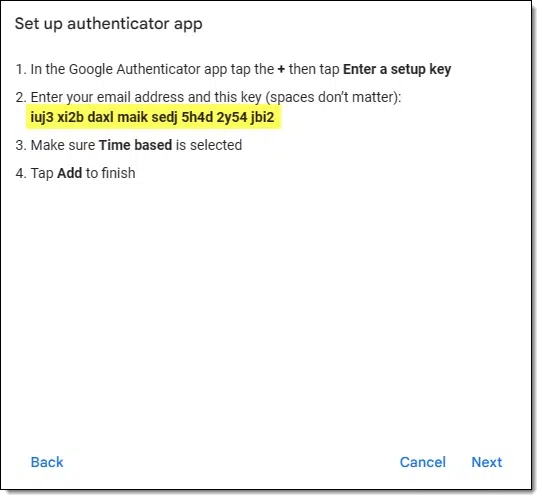
They represent the same thing. In fact, the QR code is just a different encoding of the secret string.
Once set up, that “secret” is a cryptographic number that’s associated with your account. The secret is used to create a six-digit number that can be verified by your account sign-in process to belong to you and only you because you set it up on your two-factor device.
Your one two-factor device: typically your smartphone. The one you’re worried you might lose.
Did I say one? Not if you plan ahead.
One code to enable them all
Here’s the “trick”. While it’s displayed, screenshot the QR code. Or, while it’s visible, copy/paste that secret string somewhere. Or (as I do more and more), do both.
Then continue to set up your two-factor device.
Now, at any time, you can set up an additional two-factor device simply by scanning that QR code you saved1 or by entering the string you saved. It’ll display the same codes as your original two-factor device. Try it — it’s kinda fun to watch.
As far as your account sign-in is concerned, the two devices are indistinguishable from one another. They both display the correct code, so you must be you.
In theory, you could add as many two-factor devices as you like using this same secret code. They’ll all display the same code you need at sign-in time. Any of them will prove you are you.
I don’t recommend setting up a bunch, but I do have some recommendations.
Secret means secret
The reason the code normally disappears after you set up the first device is that it’s a secret then known only to that device. This is the most secure.
If you keep a copy of the code — be it by taking a screenshot or by copying the secret string — you must now keep that information secure. Anyone with access to it could set up their own two-factor device with the code for your account. Obviously, that’s not something you want.
I keep mine in an encrypted location only I have access to.
And I don’t need it often. Ideally, I’ll never need it, but stuff happens — which leads to my second recommendation: don’t set up a second two-factor device until you need to.
Here’s the scenario everyone worries about: they lose their smartphone with the two-factor app on it. No problem! You replace your phone, install the 2FA app of your choice, rescan your saved QR code (or enter the secret text), and you’re back in business, simple as that.
Do this
Save your two-factor setup codes. Either screenshot the QR code or save the secret text string. Whichever you do, store it somewhere secure you can access later should you ever need to.
Hopefully, you’ll never need to, but it’ll make life just a little easier if you do.
Looking for more security tips and safety nets? Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: And yes, that’s a real account QR code in the example you could scan. It’s no longer associated with any account, so it’ll do you no good, but you could.




I learned to keep a copy of the codes when I started using Yubikeys. Yubico has an authenticator app that provides TOTP codes that work with the Yubikey. It works by opening the app, selecting the service you are logging into by double-clicking it, then touching the Yubikey to generate the code which then can be copied.
Each of the Yubikeys I use need to be set up individually with the app. By keeping a copy of the QR code or secret code, I can have backup Yubikeys that work.
I prefer the Yubikeys as it means I don’t need a phone to log in. There is an Android version of the Yubico Authenticator that works with a NFC capable Yubikey and phone. The Yubico Authenticator can be downloaded from Yubico or found in the Microsoft Store.
I have noticed that most websites that use authenticator apps for TOTP also have an option to add a second authenticator/device for 2FA as a backup means.
I did the same thing as you regarding setting up 2FA on multiple Yubico Yubikeys and for the same reasons, by saving the 2FA secret codes and manually configuring the additional keys.
Also, what distinguishes the Yubico Authenticator app (and the Android Aegis 2FA app) from all other 2FA authenticator apps is that they display the secret key and time step generated by the online server and contained in the QR code during 2FA setup. Most other 2FA authenticator apps don’t display this information, including Google, Microsoft and Authy.
I had a problem trying to setup 2FA for my email billing account. The online server did not display or have an option to display the QR code secret key. Subsequently, no matter what I did the server kept telling me “invalid code” when I first entered the newly generated 2FA code in Yubico Authenticator (and Aegis Authenticator) apps while setting up the account for 2FA.
Eventually, I noticed something in the either the Yubico app or the Aegis app that I hadn’t initially paid attention to: the Yubico app showed the time-step used by the online service for its TOTP (and this is buried in the QR code). Yubico/Aegis was showing that my email billing account was using 60 sec. for the time-step, instead of the usual 30 sec. used by most online services. I manually changed the time step in the Yubico app to 30 sec. during another 2FA setup attempt and voila! – I finally managed to get 2FA setup and working for the account. I contacted my email service provider and they confirmed their QR code was being generated with the wrong time step, which they corrected.
I found a couple of RFCs online that specify how TOTP 2FA is supposed to work and from what I read, there is nothing that says an online service must use a 30 sec. time step – it can be anything – but from what I’ve experienced, all the online services that I’ve setup TOTP 2FA for, all use the default 30 sec. time step interval.
If it hadn’t been for the Yubico Authenticator (and Aegis Authenticator) apps showing me the TOTP time step interval contained in the QR code, I would still be pulling my hair trying to setup 2FA for my email billing account. I’d even contacted Yubico and done a few diagnostic things on their temporary account web site, to no avail, when I was trying troubleshoot my email billing account. Yubico Authenticator and Aegis Authenicator apps saved the day.
I have a question about the scenario you describe, which is: I lose my phone. I get a new phone. I scan the ‘secret’ QR code (or copy/paste the string) I saved from when I set up the authentication app the first time into the new authentication app (activating it) on my new phone, and I’m all set. What about the authentication app on my old phone? What if it’s ‘found’/stolen by some savvy miscreant? Does ‘activating the authentication app on my new phone deactivate the one on my old phone, or if the person who ‘finds’ my old phone can gain access to it, can they also use my old authentication app to access any accounts I have stored on it? I know the likelihood of this ever happening is incredibly remote, but if the old authentication app could/would still work, is there a way to disable it, if for no other reason than to ease my mind. I haven’t had to deal with anything like this yet, but I’d rather think ahead than wish I ad after the fact.
Ernie (Oldster)
Activating it on a new phone does not DEactivate it anywhere. The service has no idea you’ve changed anything, you’re just able to continue to provide the correct 2FA code using your new device.
Remember, it’s two factor authentication. The thief/finder would need to also know your password.
That being said, since we leave our devices signed in frequently, I do recommend changing passwords.
That’s what I thought. I simply wanted your take on that detail. Thank you. I neglected to remember that the 2 in 2FA means I still have control over my password if I lose my second factor device.
Ernie (Oldsterz0