My neighbor called me the other day and asked if I could look at his computer. (Something you might well experience yourself 🙂 ).
He’d lost connectivity to his ISP, but more interestingly, his backup machine – a laptop – was acting … odd.
The ISP problem turned out to be the ISP’s problem, and resolved itself the next day.
The laptop, however, turned out to be a different story. When I was done with it, my neighbor asked, “Well, is that an Ask Leo! story?”
Why, yes. Yes it is.
The symptoms
As with any well-used system, the symptoms were somewhat obscured by what could also be normal behavior.
My neighbor’s description boiled down to this: “I can’t get to most sites. Oh, and I think I saw the word ‘redirect’ flash by at one point, could that be related?”
Well, yes, it could be, but that alone is certainly not a symptom of a problem. Redirects are common – when you use a URL-shortening service like bit.ly or tinyurl.com, then you’re using a redirect. An example might be one of my own: https://go.askleo.com/ms redirects you to microsoft.com.
But as you can imagine, redirects can be used for evil as well. So with “I can’t get to most sites” being the major symptom, it was certainly a consideration.
The contributing factor
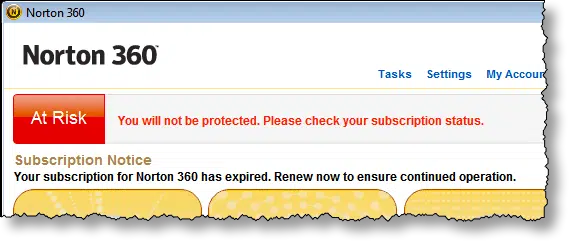
One thing that may have contributed to the problem was that the security suite – Norton 360 – had expired.
Now, it’s unclear just how much or how little Norton does in the expired state, but it certainly didn’t make me feel good about the machine. Ultimately, my guess was that it was extremely vulnerable until Norton was renewed, or until an alternative was installed.
And, indeed, attempting to download an alternative is what clued my neighbor into the problem: none of the sites he was trying to reach would respond.
The evidence of a redirect virus
Whenever I hear about unexpected redirects, one of my go-to places to look is in the “hosts” file. Hosts is a shortcut for DNS lookups – the mapping of domain names, like “askleo.com” to their IP addresses (50.28.23.175, currently). Windows, and indeed all popular operating systems, look at the hosts file for an IP address-to-domain mapping before asking DNS servers for the answer.
As you might expect, what some malware likes to do is change what’s present in hosts. If they can change the IP address associated with, say, askleo.com, then they can cause your visit to askleo.com to actually go to their malicious server instead. Fortunately, this is one of the things that most security software can prevent, and https connections warns you about if detected. Our security software wasn’t running in this case, and of course not all sites are https, and https warnings are, unfortunately, common enough that we often ignore them anyway.
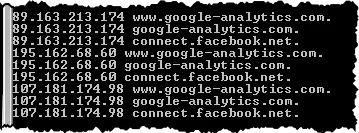
Sure enough, in the hosts file (c:\windows\system32\drivers\etc\hosts) were some absolutely suspicious entries.
What was interesting is that these entries were preceded by dozens of blank lines – almost as if the malicious software was hoping that we might not scroll down if looking at the file, and thus miss these entries.
Coincidentally, I’d just heard of this specific variant a week before.1
Those two sites – google-analytics.com and connect.facebook.net – are two services websites often use to compile usage statistics. For example, all the Ask Leo! sites use Google Analytics, so I can see how many people visit, where from, what pages are the most popular, and more. The Facebook reference, as I understand it, is common when sites use Facebook “Like”, “Share”, or comment services.
All of these references pull in Javascript code behind the scenes to support these desired services.
By modifying the hosts file, malware inserts their own servers into the stream instead of the official servers. For example, instead of downloading the code from Google to collect analytics for a website, who-knows-what was downloaded from the malicious servers and run. (In my neighbor’s case, I believe the malicious servers had already been taken down, and it was the failure to get anything at all that was causing his browsing attempt to fail completely. But I could be wrong.)
The preparation
If you know me at all, you can guess my first step.
I booted from a Macrium Reflect rescue disk, and used it to make a backup image of the laptop. Even though we call it them “rescue” disks, many backup tools will allow you to use those disks to make backup images.
This is important for two reasons:
- No matter what I did next, I couldn’t make matters worse. 🙂 If I did, I could just restore the backup image and start again.
- It would allow me to examine the machine in more details after it had been fixed. In fact, the screen shots accompanying this article are taken from the backup image, restored to run in a virtual machine.
The attempts
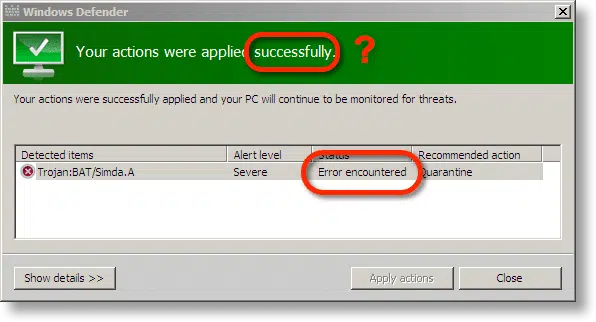
This sure sounds like my article: How do I remove a virus if it prevents me from downloading or installing anything? Indeed, that’s right where I started: by running Windows Defender Offline. I downloaded it on another machine, burned it to CD, booted the laptop from it, and ran a scan.
It detected malware, but failed to fix it.
In fact, I ran it twice, because the first time I didn’t notice that the fix had failed.
Next, I downloaded and tried another stand-alone repair disk from another security software vendor, which also failed (more explicitly this time).
This didn’t bode well.
The cure
Fortunately, that last repair disk also included a command-line interface.
I figured it was time to take matters into my own hands.
All I did was edit the hosts file with a text editor to remove the malicious redirections that resulted from the redirect virus. I have no idea why neither tool I tried was able to do that.
I’d been reluctant to start there, since I expected the hosts-file modification to be a symptom of a larger problem, and I wanted the security software to scan for and correct those issues as well. Apparently not.
Windows Defender Offline then reported the system as clean, as did the other repair disc.
Then I downloaded and installed a copy of MalwareBytes Free on the system, and ran that. It also reported several items – mostly PUPs – which it quickly cleaned out.
Next I rebooted, connected to the internet, successfully downloaded Microsoft Security Essentials, and let it run a complete update and scan. Similarly, I re-ran MalwareBytes, allowing it to update its database first, and it came up clean as well.
Help keep it going by becoming a Patron.
The resolution
To be honest, I have no clue as to exactly how the machine became infected. There are many possibilities.
Similarly, the PUPs that MalwareBytes found could have been the result of random previous installations, completely unrelated to the major infection, or they could have been additional downloads facilitated by the infection.
Or it could have all been something else completely.
We’ll never know.
The machine was left with Microsoft Security Essentials as its security software, Windows Firewall enabled, and MalwareBytes Free for on-demand scans as needed.
The lessons
The reason I share this story with you, beyond it just being an interesting case study in malware detection and removal, is that there are several important take-aways:
- Have a recent image backup to restore to. There wasn’t one in this case, but had there been, the story would have been much more boring: restore from backup prior to infection and get on with life.
- Renew or replace your security suite before it expires.
- Not all anti-malware tools catch, or repair, all malware. While the specific failure I encountered was unexpected2, that something wasn’t fixed is common. Having alternate tools or techniques (or resources, like people to call on) ready can be important.
- And, of course, learn how to Stay Safe on the Internet.
Do at least the first and the last, and you may never need to have a story like this of your own to tell.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!


Ok Leo, you wrote something that caught my eye – one of those “I didn’t know that!” moments.
You said that you used a Macrium Reflect Rescue Disk on your friend’s laptop and used it to make a backup image of the laptop. I got really excited at the possibility that I could do that myself for some friend if the need arose.
ALAS – I could not make it work. I have the Standard Edition of MR and when I put it into another 64 bit machine I could never make it work correctly. let alone do an image of the other machine.
What might I have been doing wrong or does the edition you have allow this feature and the Standard does not?.
Without knowing what happened when you tried I have no way to say. To the best of my knowledge, it should work.
Leo, I have three machines 1) desktop running Win 7 Home Premium 64 bit 2) laptop running Win 7 Pro and 3) an XP machine. The desktop has Macrium Reflect Standard Edition, the laptop has Macrium Reflect Free.
I had a number of Macrium Reflect Rescue Disks which I had made over time. I took one made on the desktop and tried it in the laptop. It would not boot because it came to a point where a dialog window popped up saying that I needed drivers for USB, USB, and Network Controller. It hung at this point and would not proceed.
This disk was made from the Std edition 5.2.6526 using Win PE 3.1. I had another made on the Std edition 5.3.7299 using Win PE 3.1. It acted the same on the laptop as the other.
OK, I said. I went back to the desktop and using the Std edition made a rescue disk using Win 5.0. It was some better on the laptop in that it did not need USB drivers but still needed the Network Controller driver. It hung.
So, my experience says that a rescue disk will not work unless all necessary drivers for the target machine are on the rescue disk.
Now, going the other way, I updated the Free version on the laptop to 5.3.7299 and created a rescue disk using Win PE 5.0. This disk will successfully boot the desktop and will indeed allow me to make an Image Backup of the desktop using the Macrium Reflect Free rescue disk made on the laptop.
Let me note that none of my rescue disks would boot the XP machine in any fashion.
Based on this experience, I am concerned that your implying that you can use a Macrium Reflect rescue disk on another machine is not correct.
A rescue disk is a bootable CD or DVD with generic drivers which should be enough to allow you boot the machine and copy the information from the backup image to the hard drive. I don’t believe it gets any drivers from the machine that creates the rescue disk. This should work in the overwhelming majority of cases although there may be a rare case where it doesn’t work.
It would seem that the Macrium Reflect rescue disks I have are more specific to the machine which created them. Or, perhaps, they are a function of the “version”. The rescue disk made using “std” and Win PE 5.0 on the desktop will not boot the laptop. However, the rescue disk made using “free” and Win PE 5.0 on the laptop will boot the desktop and will offer to make an image.
Could it be that Macrium is doing something to protect the “pay” software.?
No. But you can check – download the trial and create a rescue disk with it and see.
My sense is that the rescue disks created by Reflect cover 95% of all machines without needing to be generated on those machines. There are edge cases (PCs can vary dramatically), which would require extra drivers or steps or more.
I’m concerned as well. My experience is exactly the opposite of yours: every disk I’ve ever created has worked in every machine I’ve tried it on. The bottom line is that it pays to test the scenario before you need it.
Leo, I realize you non longer recommend Acronis True Image, but I wanted to mention that I have had 100% success using TI “rescue” disks (from versions 2011 through 2015) both imaging and restoring many computers. There have been no extra divers needed unless a “hardware independent” restore was attempted (i.e. to a different machine than the one from which the original image was made), and even then the restore often succeeds with no additional drivers used.
was this attack done by a frenemy? if so, it shouldn`t be too hard to figure out who did it.
if it was done by a pro, what good would it do them to put it on one machine?
if it can be done in mass applications, more people should be complaining.
it just sounds to me like the person who owns the machine did this to themselves somehow.
Leo is always saying when it comes to malware we are the weak link.
Thank you for the step by step instructions on how you investigated and fixed the malware problem.
Leo!
Used anti-malware software and after opening the host file contained:
“This hosts file cured by. . .
So I imagine this software different from Microsoft would fix this difficulty.
I do not understand what is suspicious in the host file entries shown.
How can you tell that it is directing traffic to Facebook and Google analytics and that these are not legitimate entries? How does simply being directed to these specific sites cause a problem?
Follow the IP addresses listed and you’ll see that they do not go to the site specified. Like, connect.facebook.com for instance: it does not go to Facebook but sends his computer to this other server instead. I recommend not to follow them all and have your anti-malware running when you do!
What Leo forgot to mention is that you would normally expect the hosts file to not contain any entries at all — just some comments about how to edit it. If you find any entries in the hosts file at all, and you didn’t put them there, that tends to be a pretty major red flag (though note that some legitimate software, e.g. VPN clients, may use it — it’s not a guarantee of infection).
The fact that they are listed in the hosts file at all is the problem. The should not be there, there should be no need for them to be in the hosts file. That name-to-number mapping needs to be done properly by the DNS system as needed. Hosts overrides, this. For most people the hosts file should be close to empty.
John,
What do Macrium Reflect authors say about this?
For what it’s worth I have a Windows 8 desktop and when it boots from the MR rescue disk created by the same computer, it will boot, analyse the hard drives then display:
“You may need to load drivers for the following devices in order to backup/restore.
Ethernet controller, Network controller, USB controller.
Yes to load drivers, No to continue.”
The boot and backup works fine whichever I select (and I’ve done a restore).
My older desktop is Win7 and it’s MR rescue disk doesn’t display any message. Same version of MR 5.3.7220
Does “FlushDns” command solve such a problem. It could be done either by elivated command prompt or using some tools like the free efficient “Complete Internet Repair” by Rizonesoft.
No. The hosts file overrides DNS.
I bought the Norton anti virus several years ago, for a desk top with Vista OS. After a time, when renewal came up, I couldn’t afford to renew, so bought McAfee instead. I have tried several times to delete that Norton and have been unable to, and, even though it is not, supposedly, active, I notice from time to time it seems to be monitoring something, and I’ve tried to delete it, but it won’t work. When I tried to delete McAfee about a year ago and switched to AVG Free, I didn’t have any problem, but Norton just will not go away. That desk top crashed a couple days ago and all efforts have failed, so this is not a pressing problem, but I just thought if others have the same problem, your expertise may be helpful. Was going to do the factory image restore, but don’t have the disks made and, due to the computer repairman putting my old XP drive in there, it won’t let me make them. He did that so I could save my pictures and documents, so it was a great thing at the time. BTW, love reading your advice. Thank you. As for that desk top, it will run in safe mode, so if I find a way to get the disks, even if I have to call the repair guy to remove the XP, I’ll be able to “revive” it. But can’t afford to buy them.
You might try the Revo Uninstaller.
http://ask-leo.com/how_do_i_remove_uninstalled_software_leftovers.html
http://ask-leo.com/revo_uninstaller_uninstall_things_that_wont.html
The anti-virus companies all have removal tools on their websites to get rid of remains of their own anti-viruses that are left over after an uninstall,
as always all is difficult for an 80 year old i AM INFESTED WITH Google re-direct and tried all avast scans including boot scan, all spybot( I scraped my weekly pension to buy spybot anti virus including deep/rootkit ( also cant get to spybot forum because dashlane fires in the wrong password) also Malware bytes scans. Also paid precious pennies for Avast’s grime fighter (each time used, after two grime fights, computer froze and had to be crashed and each time computer was slower and problematic). Still have the Google infection and only heaven knows what else the anti virus/malware cannot discovr, still runs sloswer than a snail….no matter wat. I also have gone through all the ramifications of HP investigation ( the ones you get to from shutdown then escape ) no difference. Tried add ons I only have Google, google toolbar, dashlane Bing ( disabled) and have tried disabling all betimes. I have posted on yr site befgoe no reply i am reg for yr letter but ye wont send me yr ten ways to speed up slow computer possibly i have tried them but????….al i n allk I am losing faith even ion yourself and I have read your newsletter for years its is too rambling you need to post simple do this instructions at the end of all thed stuff sorry about critisisms but at end of my tether
I bought an Sapphire RX 460 NITRO 4G, came home and tried to install it. Got the card installed,connected the power connection from the power supply.
Had power to my card,fans ran.lights on. but no video,also tried a GTX 1060 same thing…after a lot of research and troubleshooting,I discovered that those cards need to turn off the csm portion of UEFI for them to run. Where do I find this?