Headlines don’t always make it so.

Scary news headlines abounded in recent weeks as the FBI warned against something called “juice jacking”.
Is it really a threat?
No. Not really.
Well, OK, maybe. But that’s a really really big maybe.

Juice jacking
While theoretically possible, “juice jacking”, or the malicious transfer of data while connected to an unknown USB charging port, is both rare and easily thwarted. Most current mobile devices won’t even allow data connections by default, and using a wall charger or USB data blocker also neutralizes the threat.
The warning
The Denver office of the FBI posted a warning on Twitter.
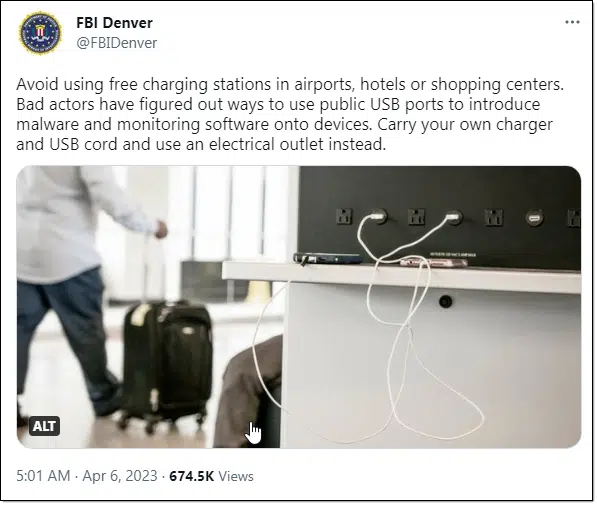
“Avoid using free charging stations in airports, hotels or shopping centers. Bad actors have figured out ways to use public USB ports to introduce malware and monitoring software onto devices. Carry your own charger and USB cord and use an electrical outlet instead.”
The implied threat is that charging your device at a randomly available USB socket could result in malware making its way to your device.
Help keep it going by becoming a Patron.
The tech
Your USB connection is used for two separate functions:
- Power and recharging
- Data transfer, such as to or from your computer
It’s the latter item that is of concern. The concept is that a random socket of unknown origin offering the first could also be used to do the second maliciously. In other words, it could be used to surreptitiously copy your data from your phone or transfer malware to your phone.
It’s referred to as “juice jacking” because they’re supposedly hacking your data while you’re “juicing” (charging) your device.
But are they really?
The reality
This might have been a threat once upon a time, but today’s devices are smarter than that.
To begin with, most require an additional step for data transfer. By default, the device ignores all data, connecting only to power up. You need to take an additional, manual1 step to enable data transfer each time you want it.
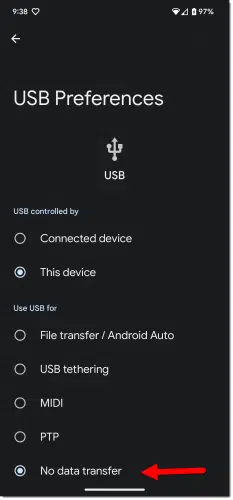
The other reality? To the best of my knowledge, there have been zero reports of juice jacking ever happening.
The protection
There’s no harm in protecting yourself, particularly since it’s easy. There are two approaches.
Use a wall charger2. Anything that plugs into a power outlet is safe to use to charge your device. There’s no data involved.

The other approach is to use what’s called a “USB data blocker“3.

These devices connect only the power connections between your cable and untrusted USB sockets. The data lines never make contact.
Do this
Travel safely. Honestly, I don’t want to worry about this for the reasons I’ve mentioned above, but if you like, using the solutions listed will keep you safe.
Perhaps the biggest takeaway here is not to let headlines scare you — even, apparently, if they come from the FBI.
Want something you can believe? Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.




If you have a phone or tablet that doesn’t default to charging only (all phones and tablets probably default to charging only nowadays) and you don’t want to get a USB condom, you can use a power bank in between the phone or tablet.
“If you have a phone or tablet that doesn’t default to charging only…”
My Amazon Fire uses a really old version of Android; I don’t believe it has any such default.
On the other hand, I’ve never had any occasion to plug into a foreign or wayward USB port.
Still, looking into a USB Data Blocker (I refuse to use that other term!) isn’t a bad idea…
A USB power bank should work for that and you’ll also have a reserve of power if you’re not near a charging station.
INTERESTINGLY, there’s apparently also a need for the reverse — a Power Blocker!:
https://amzn.com/dp/B094FYL9QT
(P.S.: Always shorten your Amazon URL’s! “https://amzn.com/dp/” plus the ASIN will work 99% of the time.)
Does the FBI not have better things to do ? Like solving real crimes ? Just sayin’ …
That is a real crime. They use the information to commit identity theft, drain people’s bank accounts, and other crimes.
re: blocking. Reading the product description says that (paraphrased) it is useful for when the power draw of the connected device causes unintended consequences, for applications such as Raspberry Pi and similar microdevices. It also says that it won’t pass data for iPhones and smart pads that require the power connection, which are most of the devices I’d expect to be connecting to an on-the-go kiosk.