Extra-destructive malware might call for extra-strong protection.

In a previous article, I wrote about how ransomware is nothing special when it comes to prevention — it’s just malware. The same steps you take to protect yourself against malware are the steps that protect you from ransomware.
Because of ransomware’s devastating consequences, however, many people want additional assurance they’re protected even if they accidentally allow such malware to reach their machine. In particular, two questions come up often:
- What about files stored in services like OneDrive or Dropbox?
- What about backups stored on connected external hard drives?
There are approaches to specifically ease those concerns.

Ransomware protection
Ransomware can lock up your backups as well as your files. Tools like Macrium Reflect and features in OneDrive or Dropbox won’t stop an attack, but they can save your data after one. Stay alert and back up smart.
Protecting your backups
I’m a big believer in regular, automated image backups. Automation requires a destination for the backups — typically an external drive — that is always connected and ready.
The concern is that ransomware might encrypt files on your backup devices as it encrypts your data. This makes the typical ransomware protection advice — just restore a recent backup — impossible.
Macrium Reflect has a feature called “Image Guardian” in its paid version to protect against just such a situation.
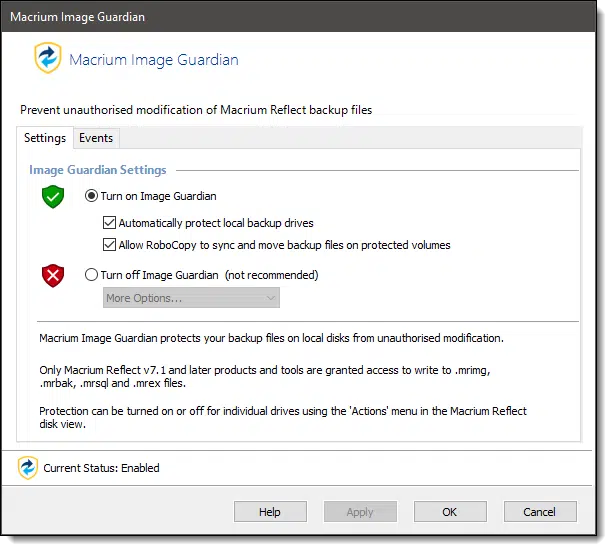
The concept is simple: only authorized applications — Macrium Reflect itself and a couple of very specific exceptions — are allowed to do anything to the backup images.
Even attempting to delete such an image in Windows File Explorer will generate an error and a notification.
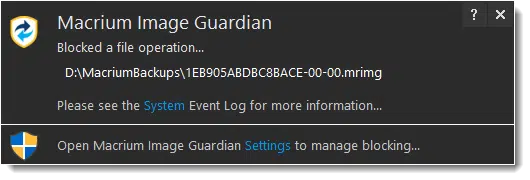
This blocks your backup images from unauthorized modification by malware. (You can delete the file from within Reflect, of course.)
I appreciate this feature because it allows you to safely leave your external drive connected (and your backups running automatically) without having to remember to reconnect the drive.1
Help keep it going by becoming a Patron.
Protecting your cloud storage
Cloud storage and synchronization services automatically back up the files you place in specific folders on your computer to the cloud. For example, if you regularly work in a OneDrive folder, those files are automatically copied to OneDrive.com online each time they change.
This is an effective form of near-real-time backup. Every time you save the file, it’s copied to the cloud, and possibly also to any other computers connected to the same OneDrive account.
The concern here is that ransomware comes along and encrypts your files. Because they’ve changed, those (now encrypted) files are automatically uploaded to the cloud, effectively overwriting your backup.
Both OneDrive and Dropbox have had a form of file history for some time.2 What this means is that if a file has been changed or deleted, you can go to the website and restore the file to a previous version before the change was made. Both also have recycle bins.
This can be burdensome, however, if ransomware encrypts hundreds or thousands of your files.
OneDrive allows you to restore your entire collection of files to a state prior to a given date.
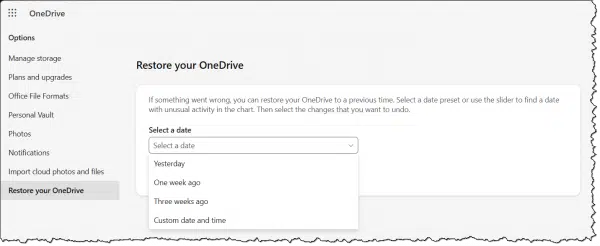
Was your machine infected by ransomware on Tuesday? After you’ve cleaned your machine of the malware, reset your OneDrive to the state it was in on Monday.3
Dropbox includes a similar feature called Rewind in its paid plans.
It’s interesting to note that both OneDrive and Dropbox refer to things “going wrong” in their messages. While lots of different things can go wrong, the most likely cause for these features’ appearance and popularity is the threat of ransomware.
Do this
Neither of these features — image backup protection or cloud storage recovery — protects you from ransomware. These features only help after you’ve allowed your machine to become infected, and ransomware has done its damage.
Do not let these features lull you into a false sense of security.
You still need to be vigilant as you protect yourself from malware — of which ransomware is only one type.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: Paid versions of EaseUS Todo now also include a similar feature called Backup Protection.
2: Paid versions of these services may be required to enable these features. The product offerings do change from time to time, so check to make sure.
3: How far back you can reset to depends on your plan. My advice is not to delay.



1. Any Image Backup, may contain a Ransomware Malware that is going to “explode” after 30, 60 or 90 days! You may not discover it NOW, but will discover it when you Restore your Backup which is infected. It makes no sense to continue having “ever connected” hard drives, as you are having an increase in the probability of such attacks.
2. My own advice is having ALWAYS at least three backups of 31, 61, and 91 days old, on separate totally unconnected hard drives, connected only during Backup and Restore.
The difference in data, should be saved separately, daily, to add to what is Restored. E.g. Restoring a 61 days old backup differs from what you have “now” by data that you may add to the 61 old to make it uptodate, today.
3. In brief I would never have continuous connected external backups, and this is a major difference from your recommendation.
And we do disagree. The likelihood of a timed-release ransomware is so small (seriously, have you actually ever heard of or seen one?) in comparison to all the other things that a backup protects you from that it’s way more important to have the backup drives connected at all times so that backups are never overlooked.
And I disagree with you this time Leo… just because you, or anyone for that matter, haven’t heard or seen of one doesn’t (a) mean it doesn’t exist and (b) if it exists it may not have been discovered.
And if it does exist then you could be BIYD and BIYD. So a moot point?
Unfortunately that same logic can be used to “justify” literally anything. Just because I’ve never seen the Flying Spaghetti Monster a) doesn’t mean he doesn’t exist, or b) doesn’t mean he just hasn’t been discovered yet. (We’re getting into “can’t prove a negative” territory.)
There are no absolutes here. No such thing as perfect security — there will always be risk of some sort. I believe there is significantly less risk, in total, to leaving backup drives connected all the time so that backups can happen automatically.
As we’ve both said now, we disagree. Those that follow will see both sides and decide for themselves.
We use Backup Assist the software , this also will protect the backup drive by only allowing access via the software but also undertakes a real time scan for Ransomware , it also backs up to the cloud.
https://www.backupassist.com/BackupAssist/features/cryptosafeguard.php the software allows for scripts to be run prior to and after backup, we backup to Offline encrypted drives. using scripts to bring the drives online and unlock prior to backup and reversing at the end of each backup.
I checked my copy of Reflect, and found Image Guardian already enabled. Apparently it’s the default, but I never knew about it until reading here; thanks!
Reflect backs up to a local FreeNAS server; I’ve never looked into backing up FreeNAS data to the cloud, largely because of my slow DSL connection, but it’s on my list.
Dumb question: When a file is in a cloud folder, is it also still on your computer? If the Cloud storage goes offline, do I have to wait until it is back on-line to work?
Thank you,
Depends on how you use it. It CAN be only in the cloud, but in most cases running the corresponding app (OneDrive, Dropbox, whatever) on your computer can cause all files to be mirrored on the computer as well.
Here at Ask Leo!, the only questions we consider dumb are questions answered by the article the question is being posted on.
At my previous employer we used a backup system from Datto, and they introduced a feature where it would scan for ransomware-like activity in the backups – typically many files having been altered in a short space of time. If they spotted that we’d get an alert. It was early days, and the alerts we got were always false alarms, but it was good to know they were trying to mitigate that risk.
Incidentally, a professional system like Datto generally has multiple point-in-time backups (effectively the “file history” option you described), meaning it should again be possible to retrieve non-encrypted versions of the files. However, these are expensive systems and way beyond most home users.
One final point: On my home PC I try to do a belt and braces by having a continuously-connected backup drive, but then taking separate backups to another drive every few months. If we had a ransomware disaster we’d be able to retrieve our most precious files, albeit with some significant data loss. Not good enough for a business but reasonable protection for a home PC.
I have a secondary internal drive that contains automated daily backups, so of course this stays on all the time. I have set up a calendar reminder to prompt me for weekly and monthly backups. I use one external drive for weekly, and another for monthly backups. These two stay off unless I need to do backup or other work on them. Of course, the weekly and monthly backups have less granularity than the daily, but they cover a longer history, and remain safe. The other thing is, I generally create one full image backup followed by no more than fifteen incrementals. This avoids very lengthy recovery processes, and lessens the possibility that one damage could invalidate the entire set that covers a long time.
Thanks, Leo, for the information RE Macrium Reflect Image Guardian. I’m a Macrium user but wasn’t aware of the Image Guardian feature. I had recently read that backup media should be disconnected ASAP after creating a backup to reduce the potential for ransomware to infect the backup files, and so I had started disconnecting my external backup drive except when backing up. I checked my Macrium settings and found that Image Guardian is enabled, but so is an option within Macrium that allows something called ‘Robocopy’ to manipulate Macrium backup files. What is Robocopy, and should it be enabled or disabled to stay safe?
Thanks for what you do.
For those who believe it’s important to disconnect the backup drive, the best solution, in my opinion, and the one I use is to periodically plug in an external drive and copy my backup drive to that drive. Periodically, in my case is monthly but that’s because all of my personal files are synchronized with OneDrive. You might want to copy your backups weekly or even daily. I also swap out an external drive approximately monthly and leave it at work. This is a safeguard against fire or theft.
Robocopy is a command line program used to backup and/or copy files. It’s safe to leave enabled, though you’re probably not using it so it’s also safe to disable.
Macrium Image Guardian is a great feature, HOWEVER – it doesn’t work if you back up to Network Attached Storage. It only can work if your backups are stored on a Windows PC with Macrium Reflect installed on it.
Even with Image Guardian protecting your backups from malware, it’s good practice to have 2 or 3 backup disks, and habitually swap disks every morning. This protects you from the failure of a backup disk, particularly if your PC gets zapped by a power surge that takes out both your internal disk and your backup disk.
I seem to recall you recommending the free version of Ease US Todo to backup files in the past. I use the paid for version and my backup drive is connected all the time. I suppose I now need Macrium Reflect instead to be sure that I don’t get caught out?
I’m still of the opinion that the risk is small, so I wouldn’t recommend that course of action right now. Besides, EaseUS will probably add a similar feature in the future just to keep up.
From what I understand, Leo’s main concern for not having a connected external backup drive is that folks will forget to plug it in & back up. I take the middle road. I have a repeating reminder set up in my Outlook calendar to remind me to back up. I also have a recurring scheduled backup task in my Macrium Reflect (free version) that is synced with the Outlook reminder for 10 minutes later. I plug in my external drive & the backup happens “automagically.” I then disconnect the drive afterwards. If for some reason I’m not there to connect the drive, the backup fails & I’m notified of the failure plus my Outlook reminder is still active. So when I’m back at the PC I just perform the backup manually. This may not be workable for some or even most people but I’m retired so it works for me.
BTW, this is my 3rd external drive. The previous two were always connected & both failed within 6 months. So I’m reluctant to leave a drive connected all the time even though the platter spins down when idle. This current drive has lasted 3+ years so far using the scheme described above.
Yes, but what is to prevent the ransomware program from swallowing up the entire drive, including the encrypted backup? Your backup file is on the drive, and it’s encrypted, but so what if the whole drive is unavailable to you?
I’d have to know exactly what you mean by “swallowing up”? The backup files are protected from access by Macrium’s feature, so ransomware wouldn’t be able to modify them.
Example: The backup files are encrypted. The backup files are , however, on a disk. The ransomware program prevents you from accessing the entire disk. So even if that part of the disk containing the backups is encrypted, you still can’t get to them because the ENTIRE DISK is captured (I said “swallowed up” which you said you did not understand what that means), it is captured by the crooks, it is taken over by them and held for ransom. Don’t know how to express it any better.
Other than physically stealing and removing the disk drive I’m not aware of a way, currently, for a hacker to capture or swallow up the entire disk in a way that would prevent access to the backup files — not in any “hold it for ransom” kind of way. Sure they could trash the directory or something like that, but that really has nothing do to with the topic of this article — any disks, whether they hold a backup or your primary OS — are at risk for something like that.
If you have a specific technology you can reference I can comment more, but right now this seems more of a thought exercise. As a real risk it seems miniscule and not something I would want people to be worrying about.
I think his analogy is a bit unclear. What I think what he means by haul away the safe is to encrypt the entire backup drive. Ie. not hauling away the safe but putting all of the smaller safes into one big safe which he holds the combination to. Macrium ImgGuard will still protect the backup.
Imagine a safe that is 100% burglar-proof. Not even Jimmy Valentine could open it. My money is inside, it is absolutely guaranteed safe. The crooks come in to get my money, but in no way can they get my money, because it’s in the safe. But wait. The crooks remove the safe itself! Haul it away. Even if they still can’t open it, as far as I am concerned, the money is gone! Now think, money = encrypted backup and safe = disk. Is this all still unclear?
Funny analogy. A friend of mine had a safe stolen out of his business for that very reason. It was hauled away and blown up off-site. But in the case of encryption, the safe can’t be hauled away if it’s protected bi ImgGuard or something similar.
Image Guardian is a great feature and out of the box (v7+) it’s enabled. Did IG change my backup strategy? No. I’ll continue to swap external drives every few months, and keep one in a safe in a steel outbuilding far from the house; protection from disaster like fire (annually in the Alaskan interior) or simple burglary (much less likely with wildfire for security). Will I lose data? Yes. Do I care? Of course. But a few months is OK for me. Everybody will address this issue differently, given myriad factors from the quantity of data produced on a daily basis to paranoia. Stepping back – the comments are focused on levels of security in everyone’s backups, so folks are backing up … that’s great! If your data is ransomed you have a recovery method. If your PC and attendant hardware is stolen or destroyed are you prepared?
Hi
my backups are encrypted by Acronis True Image 2020. I do this to restrict access to the backups. If anyone tries to open the backup file they are asked for a password.
Your article has intrigued me. I thought access to encrypted backup would be denied to software as well – am i wrong?
(I appreciate that the answer may be specific to the characteristics of the backup software used)
thanks
Bob
Encrypting a file yourself does nothing to prevent someone else coming along later and encrypting it again to deny you access. So, no, this does NOT protect you from ransomware. It protects you from someone being able to examine the contents of your backups.
Does Acronis block you from manually deleting the backup? The way ransomware or any encryption works is: It creates an encrypted copy of the files and wipes the originals. Macrium Reflect ImageGuardian protects the backup against deletion. The ransomware would create an encrypted version of the backup but it would be unable for it to delete the backup.
No. You can use file exploiter to delete the encrypted back up file. 🙁
Dude, have you tried deleting an Image Guardian protected file? Even with full administrator rights, Macrium Image Guardian still blocks deletion
One question that hasn’t been mentioned here is what is the greatest vulnerability (& how is malware introduced?) Pebcak – You are the weakest link. I’m 80 & a retired IT Manager. I ran departments for 40 years. The key thing about any program is that it has to be loaded by the OS e.g. a program in the OS (Word, Excel or whatever). The most common route was via an end user who didn’t save an attachment & scan it before opening it with an application , or put in a floppy disk without scanning it (later a USB). I don’t doubt there is some malware out there that can use a running program at OS level & maybe piggy back, but those situations are rare & manufacturers of software e.g. Microsoft are getting better at not creating such programs &/or fixing when they are discovered via 3rd parties. At a personal level, I eat my own dogfood. I’ve been using computers both in business & personally for 50+ years & never had malware. I have been using Macrium Reflect Home for about 8 or so years (Guardian is on by default & I have made sure it works, not by introduction of malware but by using anti malware s/w deliberately when backing up).
The only time I had to really rely on Reflect was after Microsoft released a really crap update to Windows 10 & I had to restore my whole system. Great discussion though & it will make me review what I’m doing so I can reduce my risks even further.
I have two USB connected HD drive adapters for backup data and images. One is always connected while the other is in a fire resistant safe. If they are swapped frequently enough the data and images will be recent enough to make minimum the return to “normalcy”.
The USB adapters are powered from 120 volt wall warts so further protection would be to power the adapters using batch controlled power switches so they are only on while doing the actual backup/images. Of course that would require that the power and backup/images are controlled by windows batch with the added benefit of being automatically run at ones choice of time, even when one is sleeping.