When two-factor protects you just a little too much.

It’s no surprise, really, but most software (like your desktop email program) has no way to ask for or enter a second factor if your account is configured to require one.
If you use such a program, you’re not stuck. In addition to two-factor authentication, the industry has a pseudo-standard solution for just this scenario.
It’s called an application-specific password, or “app password”.
Become a Patron of Ask Leo! and go ad-free!

If your email program uses only username and password without the opportunity to use a required second factor, your email service may provide the ability to sign in using what’s called an app password. This password is generated by the service, can only be used by your email program, and bypasses the two-factor requirement.
Some programs just work
Before I show you how to create and use an app password, I need to point out that most popular programs are being updated to use slightly different authentication techniques that actually do allow two-factor authentication to work as advertised.
For example, if you run the Windows 10 or 11 Mail program and add a Google account so as to be able to access your Google email using Windows 10 or 11 Mail, you’ll see the authentication dialog provided by Google, not the email program.
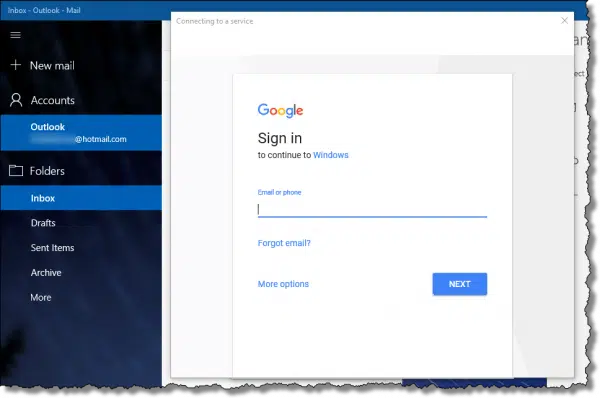
This “delegation” of the log-in step allows Google to ask you for your second factor.
In researching this article, I discovered Thunderbird also now does this, and I suspect that Microsoft Office’s Outlook will as well.
But that doesn’t help those of you clinging to Eudora, which is long out of support, or other email programs for which this approach is not an option.
For you, we need app passwords.
Generating an app password
I’ll use Google as my example, but many services that support two-factor authentication also support app passwords, including Microsoft.
Log in to your Google account online. I’ll assume Gmail as a common starting point. Click on your account icon, and then click on Manage your Google Account.
On the resulting page (not shown), click on Security in the left-hand column. On the following page, scroll down until you find App passwords. Click on that.
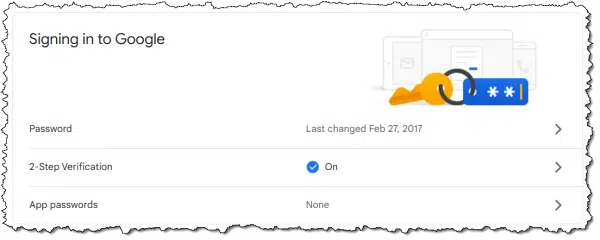
For security, you’ll be asked to confirm your password, after which you’ll be taken to a page listing any existing app passwords (you’ll likely have none at this point) and the ability to generate new ones.
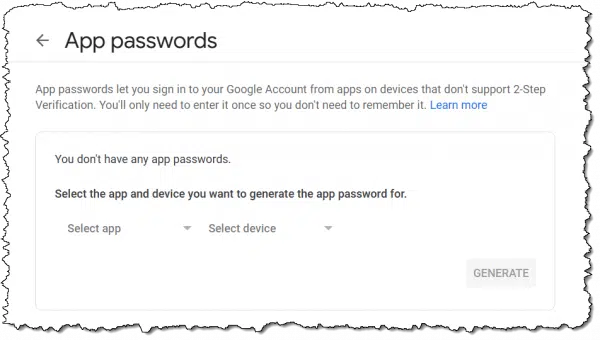
The “Select app” and “Select device” dropdowns have some choices and an option for customization.
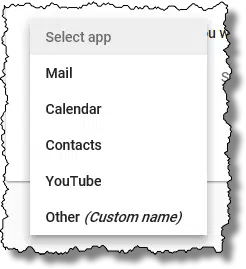
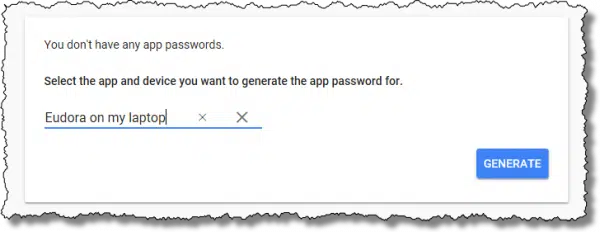
These items exist only to help you identify the app password you create in the future. I’ll choose “Other” and enter Eudora on my laptop.
Click on Generate.
You’ll be presented with the generated password.
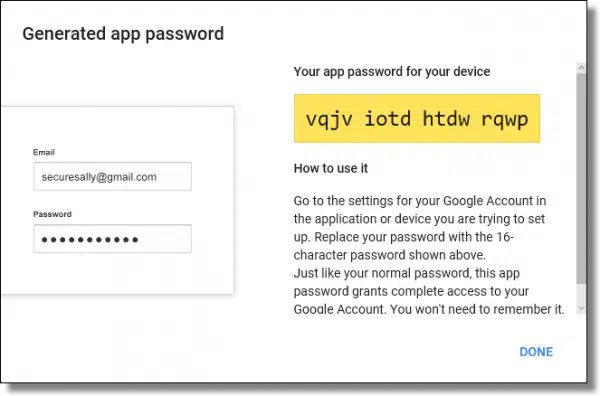
Copy this password some place safe. This is the only time it will be displayed. You can copy/paste it somewhere if you like, or write it down. As soon as you leave this page, you will not be able to see it again.
You now have an app password for your account.
Using an app password
Using an app password is surprisingly simple.
When configuring your email program, or any other program incapable of supporting two-factor authentication, use this password instead of your “real” account password. Two-factor will not be required.
That’s all there is to it.
How can this possibly be secure?
We have a password that, when used, bypasses two-factor authentication. That might seem to invalidate two-factor all together, but it doesn’t. Your app password has several interesting characteristics that make it quite secure and useful without compromising your account.
You use it in one and only one place. In our example above, I could use this password only in the configuration of Eudora, and only on my laptop. If I want to configure a different program or one on a different device, I would generate a new app password for that purpose.
It can only be used for application login. You can’t log in online using this password by entering it at the normal web-based account log-in screen.
It’s long and complex. It’s not a password that can be guessed.
You don’t need to remember it. Once you configure your email program, there’s no need to remember the password or have it written or saved anywhere. Should you find you do need a password for some reason, you can always generate a new app password.
You can revoke it without affecting your other passwords. When you finally stop using Eudora and no longer need the app password you generated just for it, you can revoke and invalidate the password back at your Google account settings.
I expect some providers will subject logins using app passwords to even more scrutiny. For example, using your Eudora laptop app password to log in via a mobile phone could trigger additional account validation requests.
Adding app passwords ends up being a very secure way to use otherwise two-factor-incapable applications.
Revoking an app password
When you stop using the application for which you created a password, you can revoke and invalidate that password so it simply won’t work. You can also do this if you ever have any reason to believe that the password — despite all the attributes above — has somehow been compromised.
Return to the app-password-generation page we started with, which now lists your existing app password(s).
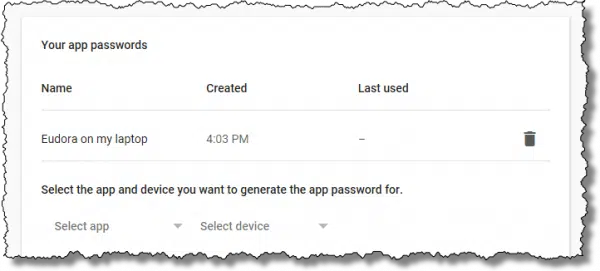
Click on the garbage can icon to the right of the password you wish to revoke, and it’ll be invalidated immediately.
This app password will no longer work.
Do this
Use two-factor authentication wherever possible.
Then, if you’re using a program that doesn’t handle two-factor, you can use app passwords to allow it to continue to work anyway.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.




I have been using this for years with my Google mail account and an ancient edition of Microsoft Outlook, but I had never understood up to now why this was supposed to be secure. I imagine the answer is this : “It can only be used for application login. You can’t log in using this password by entering it at the normal web-based account log-in screen.”
However, in all other regards, it’s worse, or not better (it seems to me), that my previous setup :
“It’s long and complex.” Well, the password I had before was much longer and much more complex, because I had been using a password manager anyway.
Likewise, the password manager already gave me all those advantages : “You use it in one and only one place”, “You don’t need to remember it”, “You can revoke it without affecting your other passwords”.
I would like to ask confirmation for this : “I could use this password only in the configuration of Eudora, and only on my laptop.”
Does this mean that if I install Thunderbird on my PC, and use the same Google app password than in Outlook, it will fail ? How does Google know that it’s Thunderbird calling, and not Outlook ? Likewise, I now use a desktop PC. How would Google know if I used a laptop, with the same program and the same app password, to access my account ?
All in all, is my present pseudo 2FA setup more secure than not using an app password, but setting up in Outlook, say, a 60-character random and unique password using all available characters in Kee Pass, including non-ANSI ones people never use, which makes for a pretty robust password by itself ?
How if a hacker tried to use a mail client program to break into a Google account protected by an app password ? How would this be more difficult than trying to hack the Web interface ?
As I said in the article my suspicion is that Google places more security scrutiny on logins with app passwords. No, they can’t tell the difference between Outlook and Eudora, and the same password would likely work in both places, but they COULD tell the difference between one location and another, or seeing it from two different locations at the same time (you and the hacker), and consider that EXTREMELY unlikely to be a legitimate use of an app password.
If a hacker DOES get your app password, and none of the red flags get tripped all he has access to is your email. He can’t, for example, change your password as he could on the web interface. He can’t do much of anything other than get your email or send on your behalf. And as soon as you revoke the app password hes out.
I have been uing Eudora version 7.1.0.9 (on a Win 7 desktop PC) to acccess my workplace mail on a Microsoft Exchange server for years. They just implemented MFA and now Eudora won’t authenticate. I created the app password as instructed, but will that work with Eudora accessing the Exchange server and Offcie 365, etc? Or is this just a Google thing?
Thanks for this simply brilliant article, Leo. You’ve really outdone your usual excellence, here.
As a constructively-meant comment, I certainly get the security requirements given today’s dangerous on-line environment, but, frankly, it’s becoming more and more complicated by the day in the search for complete on-line safety. In fact, it’s now becoming quite onorous. And, as this progresses further, what can we expect down the line re. this safety aspect?
Should not the drive (‘scuse pun..) now be to simplify, rather than assault poor computer users?
Just a mention … you keep us perfectly updated as to the latest requirements but, I felt this fact needed to be called out by someone …
Keep up your excellent work … thank you so much!
Oh they’re TRYING to simplify, trust me. The problem is … hackers. Anything truly simple is more easily hackable. What most people don’t understand is the immense size of the problem. So, yeah, it feels more complicated because it is, but it’s needed to protect your account from being stolen by someone else.