It depends on the problem you’re attempting to solve.

There’s encryption, and then there’s how you organize what you’ve encrypted. While the two tools both encrypt your data, where they differ is how they organize your encrypted data on disk.

Cryptomator vs VeraCrypt
VeraCrypt and Cryptomator both encrypt files, but they differ in how they organize those files. VeraCrypt bundles data into a single encrypted container while Cryptomator encrypts individual files, making it better for cloud storage. Use VeraCrypt for offline data or entire drives. Remember: “lose your password, lose your data.” Always back up unencrypted files!
The VeraCrypt model
VeraCrypt is what I’ll call a “monolithic” encryption tool. It takes all the files you want to encrypt and places them in a single encrypted file.
You create a special container file (called a vault or volume) using VeraCrypt. You choose how large the volume will be based on the amount of data you want to encrypt. For example, I might have 80GB of data that I want to keep secure, so I might create a 100GB VeraCrypt volume to have a little extra room.
When you create the volume, you assign it a passphrase that encrypts its data. The vault itself, however, is just a large file that, to all appearances, contains random data.
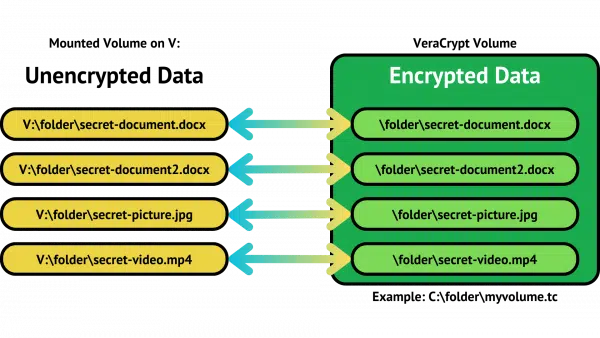
In the example above, drive V: has appeared after mounting the VeraCrypt volume “C:\folder\myvolume.tc”.
The contents of the encrypted container appear as unencrypted files on the V: drive in Windows File Explorer. As long as the container is mounted, the contents are directly accessible to all programs running on your machine. You’ve opened VeraCrypt’s one big encrypted file to access all the individual files inside it.
If you don’t mount or when you dismount the container, all that remains visible is the volume itself — “C:\folder\myvolume.tc” — which appears to contain only random noise.
The Cryptomator model
I call Cryptomator an “incremental” or individual encryption tool. It stores encrypted files as individual encrypted files.
To use a Cryptomator vault, you specify a folder that will contain the encrypted data. The folder itself isn’t encrypted, but rather will contain the individually encrypted files. When you create that vault, you specify a passphrase used to encrypt the data you place into the vault.
Much like VeraCrypt, you “mount” the volume, specifying the passphrase to unlock it. This creates a virtual disk drive that exposes the encrypted contents of the volume in unencrypted form.
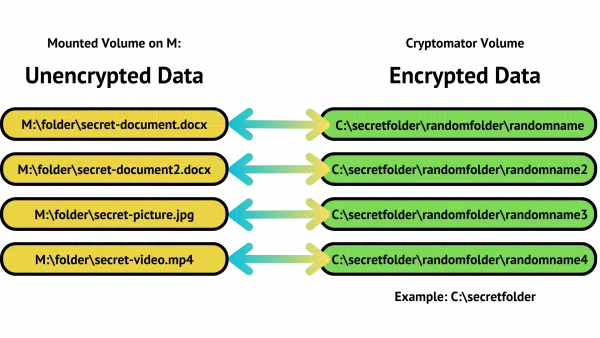
In the example above, drive M: has appeared after mounting the Cryptomator volume “C:\secretfolder”. There is no single encrypted container file holding all the files; the files themselves are individually encrypted, and stored within this folder.
The contents of the encrypted container appear as unencrypted files on the M: drive in Windows File Explorer. As long as the container is mounted, the contents are directly accessible to all programs running on your machine.
If you don’t mount or when you dismount the container, all that remains visible are individually encrypted files with random names organized in random sub-folders.1 Each file’s contents appear as random noise, and the filenames and folder structure are completely hidden.
Help keep it going by becoming a Patron.
VeraCrypt or Cryptomator?
You can use either encryption program, of course, but there’s a big difference between monolithic and incremental storage.
Let’s say you want to encrypt the data you’re about to place in a cloud storage service like OneDrive or Dropbox.
Using VeraCrypt, you place the monolithic vault somewhere in your PC’s cloud storage folder. Now any time anything changes within the VeraCrypt vault, no matter how small, the entire vault is synchronized to cloud storage (and possibly replicated to other PCs sharing the storage2).
If you make any change to a single file, like “V:\folder\secret-document.docx”, then the entire C:\folder\myvolume.tc vault needs to be uploaded. If that vault is 100GB, even the smallest change requires the entire 100GB to be uploaded.3 This can take a long time.
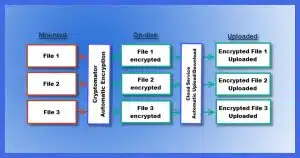
Using Cryptomator, you specify a folder in your PC’s cloud storage folder as the vault. Any time anything changes within the vault, only the files that were changed need to be uploaded.
For example, if you make a change to a single file, like “M:\folder\secret-document.docx”, then only the encrypted file representing that document — “\secretfolder\randomfolder\randomname” — is uploaded, not everything else.
Do this
Cryptomator is a great solution for encrypting files you want to place in online storage management utilities such as OneDrive, DropBox, and many others.
VeraCrypt (or Window’s own encryption program, Bitlocker) remains a better choice for encrypting offline data or entire hard drives, though you can certainly use Cryptomator for this purpose as well.
Important: neither VeraCrypt nor Cryptomator have back-door recovery mechanisms should you lose your password. If you lose your password, you’ll lose access to your encrypted information. I recommend you go one step further and back up your unencrypted data separately.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
Podcast audio
Footnotes & References
1: This is an oversimplification. I believe Cryptomator’s storage is more complex, but the concept remains.
2: Note that this makes it difficult for other PCs to have the same vault open at the same time. Cloud synchronization may either fail or confuse the system that sees the vault magically change while open.
3: This requires a specific setting in VeraCrypt to ensure that the vault’s timestamp is changed whenever a file within it is changed.
4: The “.tc” extension is a callback to the old TrueCrypt, which VeraCrypt replaced. In reality what you call the file is irrelevant.




Can the version history tools in the likes of Dropbox and OneDrive still be used with Cryptomator encrypted files? Can they still be used effectively?
In theory, yes, but … it would be exceptionally complicated. You’d be restoring the randomly named files, without a real good clue as to which of your files they represent. You could restore EVERYTHING, but of course that would overwrite the current files.
Can you encrypt an existing HD containing information or is it necessary to make a file, encrypt it and then load the data to it?
Thanks
Whole-disk encryption typically encrypts in-place. The approaches above both have you copying data into encrypted container of some sort.
I checked on the Cryptomator website and there’s a Cryptomator version for both Windows and GNU/Linux, so I can encrypt the files in a folder/directory that I want secured from prying eyes, store them on mega,nz, and access them from both Windows and GNU/Linux. I’m now a happy camper, at least if I can auto-start Cryptomator on login/system start in both OSes. Cool! A new adventure for me!
Ernie (Oldster)
***Update***
I can set Cryptomator to load on startup on both Windows and GNU/Linux. In addition to that, I can have Cryptomator unlock my vault when it starts. That means that the files I put in the vault are stored on mega.nz in encrypted format and that they are accessible by me, decrypted, on demand, in either OS, so I can use them the same way I did before I added Cryptomator to the mix. This is just what I wanted.
I gave Cryptomator a try a few years ago, and I was disappointed with it, particularly since I had purchased a code that gave me access to all the Cryptomator features (such ad a dark mode). Now I’m happy I made that purchase, and I’ll probably make annual donations going forward. At the time of my initial trial, either Cryptomator wasn’t as polished and finished as it is now, or I just didn’t take enough time to learn how to make it work the way I wanted it to (the latter possibility is probably most likely to be true). In any case, I give Cryptomator two thumbs up!
Ernie
It’s interesting. I tried Cryptomator YEARS ago, and walked away disappointed, opting for the now-defunct BoxCryptor instead. Returning to Cryptomator of late I don’t recall what my old objections were, but whatever they were they no longer exist. Very happy with it.
I tried creating a vault using Cryptomator (CP) and copied the contents of a Veracrypt (VC) vault into it. I created the VC vault with a capacity of 40 GB. I wasn’t prompted for a vault size for CP – it appears to default to 930 TB.
I checked and the contents of the VC vault are about 32 GB with free space of about 8 GB. The CP vault shows that the contents are taking 427 GB with free space of 503 GB.
I’m not sure I understand the situation. It appears that the contents of the CP vault are taking up 10X the space. Is that correct?
Also, does the system reserve the entire 930 GB, or is that just the maximum size that CP will allow for a vault?
Cryptomator is just showing you the available space on whatever drive you happened to have placed the vault. It simply grows (and shrinks) based on the files you have in it.
Not sure what to say about the disk usage issue. My Cryptomator data is, for example, 18G in both encrypted, and unencrypted forms.
That’s another advanage of Cryptomator over Veracrypt. Veracrypt requires you to set a fixed vault size. You have to estimate how much space you will need. It it’s too big, you waste all that free space, and it it’s too small, you have to run the Volume Expander tool in Veracrypt which can take several hours if the volume is large.
Would Windows File History pose potential security risks when used with Cryptomator? i.e. if File History runs while the vault is open, could it store unencrypted copies of your files in the backup?
I don’t believe file history backs up mounted vaults.
I simply cannot express how much I appreciate the amount of effort you put into such efficient, brief, yet understandable videos.
I still have a small question regarding protection from ransomware by encrypting the files. Assuming I have my encrypted Hard Drive connected to my PC or Having a network drive with encrypted files on it, while I suddenly download a ransomware on my PC.
Could the ransomware theoretically encrypt my already encrypted files in a way that they are no longer readable for my encryption software?
Macrium Reflect has the Image Guardian feature that blocks editing or deleting the backup file. If you use another backup program without a similar feature, you should copy the backup file to another ddrive that you disconnect after copying.