And why, when you look, it’s full of errors.
In an ideal world, you’d never care about Event Viewer. In fact you’d never even have heard of it.
In an ideal world, software and hardware would always work. In a slightly less ideal world, we’d be able to rely on Event Viewer for clear and consistent information about our system.
Sadly, we do not live in an ideal or even slightly less-than-ideal world. While Event Viewer can be a source of excellent clues into system failures and behavior, it can also be a frustrating, incomprehensible mess.
And scammers leverage that confusing mess to their advantage.

Windows Event Viewer
The Windows Event Viewer allows you to view the contents of the event logs maintained by Windows. Event logs contain information about how your system is functioning. Event logs are a mess and are intended only for the very technically aware. Event logs are full of errors and warnings even on a properly functioning machine. Don’t let a scammer tell you otherwise.
What Event Viewer Does
Windows has an event log. Intended for software engineers and technicians, it’s a repository of information about how your system is running and what’s been happening.
The implementation is complex, but at the highest level, a log entry includes information like:
- The time of the entry.
- The name of the application or Windows component.
- Whether the entry is informational, a warning, or an error.
- Additional information about the entry.
Event Viewer is the application used to display the contents of the event log.
Help keep it going by becoming a Patron.
Running Event Viewer
There are several ways to run Event Viewer.
In Windows 10 and 11, click the Start button and start typing “event viewer”. One of the results will, not surprisingly, be Event Viewer (as shown at the top of the page). Just click on that.
In all versions of Windows, you can also click on Start and then Run (or type the Windows Key + R), and then type eventvwr and click OK.
Event logs
Depending on your version of Windows and the additional software you have installed, there may be several logs visible.
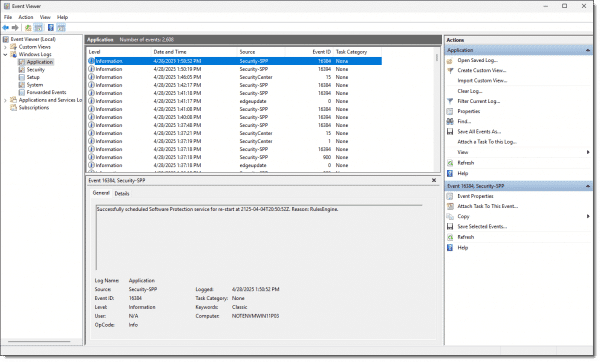
You may want to resize the window, and the panes within it, to make the contents more easily visible.
If you click on the “>” in front of Windows Logs, you’ll find five Windows logs.
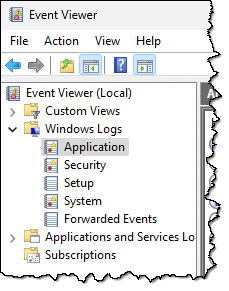
- Application: Applications running under Windows are supposed to log their events here (unless they’ve created their own Event Viewer log).
- Security: Windows logs a host of security-related events here.
- Setup: Presumably events logged by Windows (and perhaps other) setup programs.
- System: The operating system logs its events here.
- Forwarded Events: Events forwarded from other computers. (This is typically empty on home and small-business installations.)
If you click on one of those five logs, you’ll see a window with lots of logged information.
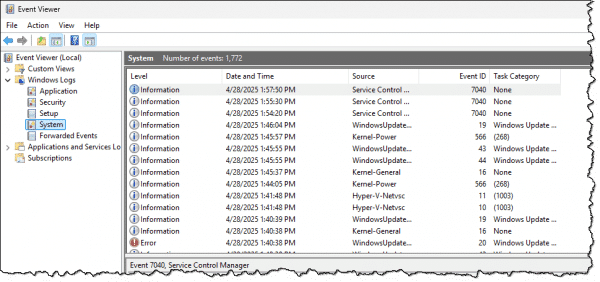
Each line corresponds to one event logged by the system. If you click on one of the lines, the information contained in that event will be displayed in the pane below.
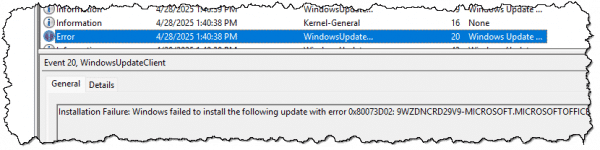
Useful information
Looking at the pane containing information about a specific error can sometimes garner useful information.
As one example, Windows Update logs successful virus definition updates. Normally, you would never need to see it, so burying it in the event log is somewhat reasonable. However, if there’s ever a question, you can come here to see if that’s been happening as it should.
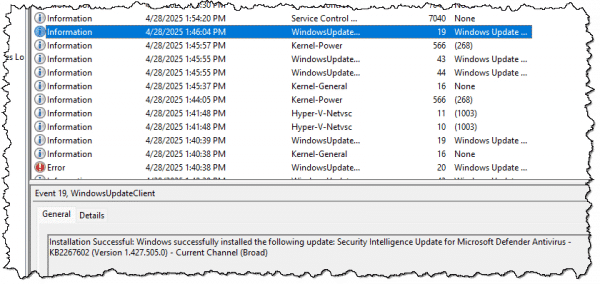
Event log confusion
As you look through individual entries, you can see that things quickly get disorganized and confusing.
- There are no real rules for what makes up an error, warning, or informational event.
- There’s no consistency in the meaning of many of the fields associated with each event.
- Many entries are just numbers that are meaningless to the casual observer.
- There are no enforced requirements that a component or application must use the event log or how much information it should log if it does.
That’s just the tip of the iceberg. The important takeaway so far is this: There’s no consistency in what gets logged or how it’s expressed.
Chaos in the data
Unfortunately, less-than-helpful log entries are common. Frequently, entries are completely indecipherable to normal people, and often even to technical folks who aren’t familiar with the component logging the information.
What’s worse, it’s normal for the Event Log to contain errors.

I’ll say that again: it’s completely normal for the Event Viewer to show entries that are marked as “Error”, even on a completely healthy system.
I’ll even say that an event log without errors just doesn’t happen.
Applications — including Windows itself — commonly log inconsistently, log things that are meaningless or misleading, or fail to log events correctly or at all.
As I said, it’s a mess… which is why scammers love it.
Scammers leverage confusion
Event Viewer has become a key component of the so-called tech support scam.
You get a phone call from someone telling you they’re from some important-sounding company or service you use, and that your computer is causing problems. Then they direct you to Event Viewer. They have you look at an event log and show you it has errors in it.
Because it does.
I said it earlier and I’ll say it again:
On a machine that’s working well, Event Viewer will still be full of errors and warnings.
The scammer knows this. The scammer also knows you likely don’t know this (at least not until now), and will instead believe that Event Viewer is confirming their claim that you need their help to “fix” your machine.
It’s a scam. Your machine is fine. The event log always has errors in it. Hang up on the scammer.
Is Event Viewer any good at all?
First, remember that the event log is meant for software engineers writing and debugging their software and technicians trying to diagnose what’s going on with your machine when it really does have a problem. For people who know what to look for (and more importantly, what to ignore), it contains valuable data.
Do this
Curious? Go ahead and browse around in Event Viewer; it doesn’t hurt to look.
Just don’t jump to conclusions and don’t panic when you see lots of warnings or errors. Every properly functioning Windows computer will have them.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.



I never let the scammers get that far. As soon as they tell me they are from [company or service name here], I call them liars, tell them I take care of my stuff, and hang up. If I start to get more of these calls, I may have to start trying to take up more of their time, just for grins . . .
Ernie
I fell asleep next to my laptop which was on the bed next to me and it was powered on and online. When I woke, I saw Chrome browser had crashed during my sleep (like it has been doing lately) and for some reason Event Viewer was up on the screen. I had never seen nor used Event Viewer before so I came here to find out what it is. Why would it be up if I didn’t call it up? Has somebody hacked my computer? Nobody has physical access to the laptop except for myself. Could my pillow or blanket accidentally have pushed some keyboard combination that would of brought it up? I run Windows 10, but not with the last update as I didn’t have enough room on the harddrive to download it and Kaspersky free. Thanks Leo for your input on this matter.
No way to know, really. I think it unlikely to be a sign of a hack, though.
This week I had an unsolicited phone call from a woman who said she was a Microsoft Engineer.
I knew, of course that she was not and I was ready for the fun that followed.
I have an old PC that only has a system disk, with nothing on it except the system files.
I also have a clone of that disk, which I keep as a backup.
I have a land line telephone near the old PC
She told me there are lots of errors on my PC, caused by viruses and hackers !
And she got me to display the Event Viewer (EventVwr) to prove it.
I pretended to be shocked and she told me to go to http://www.[removed].com
A warning popped up that this site is commonly used by hackers.
After upsetting her with this news, she then asked me to download ALPEMIX
After getting a UserID and Password from me, she then had control of my PC.
The cursor was moving about as she desperately tried to find something useful.
She then asked for my email address, but I told her I don’t use email anymore.
She insisted that I must have an email address, but I told her I couldn’t remember it.
At this point a man started talking who claimed to be the chief engineer.
He raised his voice and shouted “DO NOT TOUCH YOUR COMPUTER”
But that only prompted to click a Restart shortcut that I have on the desktop.
He soon worked out that I was just wasting their time.
He told me that my grandfather was sitting next to him !
Then after some more nonsense he accused me of trying to be clever.
Then the line went dead.
Later I formatted the drive and restored the system from the clone.
I wonder how these people manage to sleep at night.
Later that week I had three more calls from “Microsoft”, all trying to “help”.
I made one silly mistake at the start of the last call.
I told the woman that I’d already had a call from “Microsoft” the same day.
She immediately dropped the call and they haven’t tried again.
Meanwhile, I’ve set up an email address, which I can give to the hackers.
I hope this will keep them on the line longer. I’m ready !
Thanks very much for your great article Leo.
Your statement, “It’s completely normal for the Event Viewer to show entries that are marked as ‘Error,’ even on a completely healthy system” was reassuring to me. My newly built computer has been functioning fabulously until a couple of days ago when it apparently was shut down improperly. Upon attempted reboot nothing worked, the power or reset buttons were inoperative. From past experience I learned that when a computer is shut down it’s not really off until the power supply is disconnected from 110V which apparently resets everything. I did this, and the power button started functioning again. It took two additional restarts to get things up and running normally.