It is absolutely possible for malware to spread through your LAN to your computer.
In fact, I’ve heard horror stories of malware that makes it past one person’s defenses to infect a single machine … and from that machine, move on to infect an entire small business’s network.
In situations like yours, a two-router solution can be a fine approach to protecting your computers. But yes, it can be a little complex to set up, and there are side effects. Fortunately, there are simpler ways to avoid spreading malware.
Some malware travels by network
While most malware these days has to be “invited” in – by downloading and running an infected file, or opening an infected attachment – another, perhaps even older class of malware is still present: the network-based threat.
Network-based malware simply uses your machine’s network connection to probe for other machines on the network, and then attempts to exploit any network-based vulnerabilities on that machine. If successful, the malware can spread from machine to machine simply by using the network connection.
For the most part, these types of malware aren’t as prevalent as they once were. But if you connect directly to the internet without any kind of protection, you can actually see that there are infected machines continually reaching out and probing for other vulnerable machines. These machines – often older, unattended machines that have never been updated or properly secured – are responsible for generating what some refer to as “internet background noise” as they keep plugging away, looking for other vulnerable machines.
Fortunately, protection is simple.
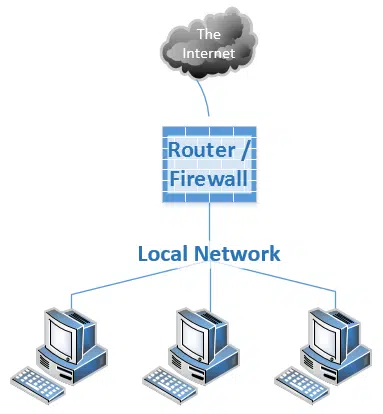
Your router protects you from the world
As I said, the internet is full of infected machines trying to reach any vulnerable machines they can.
Fortunately, your router acts as a firewall to stop them cold. Machines on the internet cannot initiate a connection to a machine on your side of your router; connections can only be made by your computer, outbound.
And that makes all the difference. You only connect to machines you, or the software on your machine, chooses to connect to. By maintaining good behavior, you know not to connect to machines, servers, or sites that want to infect you with malware.
But what happens when someone slips up? What happens when malware is invited in?
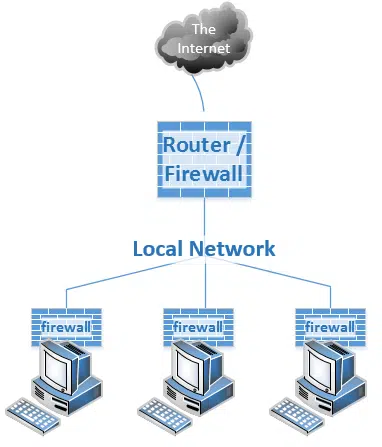
Windows firewall protects you from local machines
It used to be the case that Windows Firewall was something most folks, myself included, recommended you turn off, as long as you were using some other firewall, like your router.
That’s no longer the case, for two reasons.
First, that advice was based on its impact on your system performance. That’s no longer an issue, and Windows Firewall can be left on with negligible effect in almost all cases.
Second, by leaving it on, you’re protected from exactly what brought us here: malware that makes it onto another machine on your local network. Even if an infected machine is sitting right next to yours on the same local network with nothing in between, Windows Firewall is there, rejecting those unsolicited requests.
Your LAN and other machines
Windows Firewall will also protect your machine from other computers that share the “safe side” of your router, like your mother’s. If her computer becomes infected with network-based malware, then your use of the firewall will stop it from reaching your machine.
In fact, that is true if you have any machines on your network that you might not trust, like computers used by children or guests.
In your case, I would recommend that turning on Windows Firewall if it’s not already active on your machine. In fact, on most modern machines I advise turning it on in any case; it doesn’t hurt, and it’s an additional layer of protection.
Other solutions
Help keep it going by becoming a Patron.
While Windows Firewall is probably the easiest solution to implement, there are other approaches that can be used as well, either instead of, or in conjunction with it.
Multiple routers. I actually lay out an approach to doing this in How do I protect myself from my children? By using a second router, you can set up a separate local sub-network isolating some of your machines. With a little help from your ISP (in the form of a second IP address), you might even be able to set up completely separate network.
Guest-access routers. Many WiFi routers now include two network connections: the primary connection to your local network, and a second one for the use of your guests. The two are then completely isolated from one another, sharing only that internet connection. The “guest” network doesn’t have to be for guests – it could be how your children, mother, or other less risk-conscious individuals connect, without putting your computers at risk.
Don’t forget
I’d be remiss if I didn’t remind you that none of this replaces good internet safety habits. Specifically:
- Keep your anti-malware tools running and up-to-date. Network-based threats are only one type of malware. The networking solutions discussed here will not protect you from other forms of malware, such as malicious downloads or attachments.
- Be careful sharing files. If you transfer files from one machine to another, you’re bypassing any network protection you have in place. Copying an infected file from your mother’s computer to a USB stick, and then copying that file to your own machine, is a fine way to compromise your own machine without realizing it.
And of course, back up. When bad things happen, restoring to a previous backup is the fastest and most reliable way to remove malware.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!


Hi Leo,
For some inexplicable reason I cannot opem my hotmail/outlook web page to access my emails. I can access them on my phone and my iPad but not my pc.
I am using Win 10 And Mozilla Firefox. I uninstalled Firefox and re installed the program – no luck.
I contacted outlook but want to charge me a fee to fix the problem. I will not agree to paying a fee on the principle that it appears that it is not my pic that has a problem since i can access every other webpage on the net.
Regards Ed.
Ed, for troubleshooting issues like yours, it’s best to consult an active forum where such things are discussed in detail. I recommend the Windows Secrets Lounge: http://windowssecrets.com/forums/. Create an account and post your issue in the “Windows 10” group.
First thing I would try is another browser. Also, what exactly happens when you try to go to outlook.com – what error message, specifically, do you get?
“I will not agree to paying a fee on the principle that it appears that it is not my pic that has a problem since i can access every other webpage on the net.” – It’s likely that the problem does like with your PC – in fact, that’s almost certainly where the problem lies. As Leo said, if you post some additional details, maybe someone can help.
One thing that I really worry about is Cryptolocker and it’s kin. A major reason to have a LAN is file sharing. But Cryptolocker will reach into network attached data shares and encrypt files on other computers on the LAN separate from the infected one. It doesn’t necessarily “inflect” the other computers on the LAN, it just encrypts all their data files. Not good. And … potentially … any attached backup drives! yech.
I feel somewhat relieved that my Windows Home Server 2011 does daily image backups and stores those backup files where they are not normally accessible by user programs. (Yes … that’s right; I did say daily *image* backups. It does by backing up changed sectors, not files. Of course, there was no place for WHS in Microsoft’s vision so they have discontinued it. 🙁 )
So as Leo says … good backups are the answer.
To be clear, only a few – RARE – variants of CryptoLocker currently reach out to anything but the system drive, with internal drives being next. So while CryptoLocker is “scary”, it’s not that scary. (And it’s important to realize that it’s not one thing – there are dozens of different versions.)
Actually, the majority of currently active ransomware – CryptoWall, TorrentLocker, etc. – will indeed attempt infect removable drives as well as network mappings.
Thanks for this very helpful article. I’m curious about HomeGroup sharing. For ease of use our family has set up a HomeGroup, with Document sharing enabled. All computers are Windows 10. Does this expose all the HomeGroup computers to a virus/malware if one of the computers gets infected? Or are we only at risk if we copy a file from an infected computer to another computer?
Best I can say is “maybe”. It does expose the computers to one another in a more direct way, but I’ve not (yet) heard of malware using that to spread.
Your page ‘Can a virus spread over a local network?’ has a section heading of ‘Guess-access routers’ which is a spelling mistake of ‘Guest’ (fat finger or spell checker fault no doubt :-))
Thank you for your pages. They are often referred to in our U3A Online Australia newsletter.
Reply not required.
Fixed. Thanks!
I like to have real examples that illustrate the concepts. For example if you discuss various VLANS or different IP groups showing by example makes it easier to comprehend. As an example I am looking at right now. I am on a specific switch network of the type 192.168.xx.xx it is a private internal LAN I can do my tasks by allocating a static IP of the type shown. If I leave my laptop as a dynamic IP allocation I get a completely different Ip 10.103.xx.xx So I understand that my IP is being assigned by a DHCP Server. This gives access to the Internet.
Could some antivirus spread across from this domain to the 192.168.xx.xx domain?
I think you mean could some virus (not antivirus) spread. Short answer: yes. If you can connect between the two machines in any local fashion, the it’s possible that malware could too.
Interesting. I read that NAT becomes unnecessary under IPv6 because there’s enough addresses for everyone, but then it seems like hackers could directly connect to your IP since you don’t have the NAT indirection. Is that another reason why home networks don’t usually use IPv6?
Perhaps. It’s something I would be leery of, for sure. Right now I think lack of critical mass support of IPv6 remains the bottleneck.