Reset is the ultimate malware removal. Or is it?

Technically, yes, certain types of malware can survive a reset.
Pragmatically, though, these types of malware are rare, especially if you take a couple of additional steps as you “remove everything”.

Surviving a reset
Most malware won’t survive a Windows “Reset this PC” command, but a few rare kinds can hide in partitions, rootkits, or even firmware. Use “Remove everything,” “Cloud download,” and “Clean data” to make a reset safer. For true peace of mind, start with a clean installation media and wipe the hard drive along the way.
Persistent, resistant malware
I’ll say there are three places malware could, in theory, survive the default “Remove everything” option in Windows’ “Reset this PC” process.
Rootkits
A rootkit is malware that takes additional steps to hide its existence from the operating system. This means that when “Reset this PC” deletes the existing files on a hard disk (or moves them aside into Windows.old), the rootkit could survive to re-infect the resulting clean installation of Windows.
Partitions
Malware could install itself, or a copy of itself, into one of the reserved partitions, including the recovery partition from which Windows will be reinstalled. The “fresh” copy of Windows could then come with malware.
Firmware
Some malware infects the firmware on your machine, such as your BIOS or UEFI. By definition, this is the software that runs on every boot and manages access to certain hardware. It’s not affected by “Reset this PC”.
Help keep it going by becoming a Patron.
“Keep my files” is probably a bad idea
When you reset your computer, one option you select is whether to remove your files.
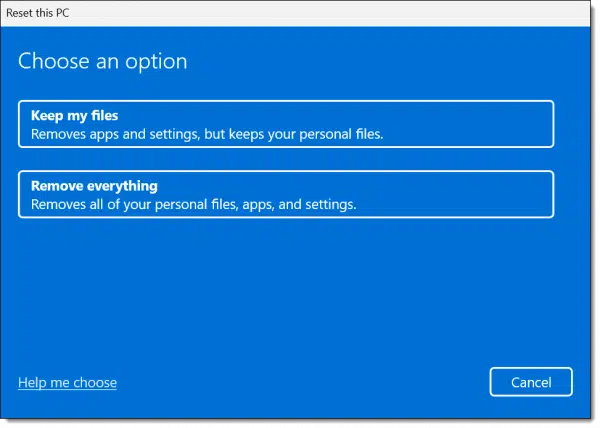
The default is to keep your personal files. Presumably, this means the files in your “Documents” folder and similar locations, but it’s unclear how much is kept. Regardless, if one of those files is infected, then this presents an opportunity for that infection to persist.
So, choose “Remove everything”. This does imply that you’ve got your data backed up or copied elsewhere to restore after the process is done.
“Local reinstall” is probably a bad idea
Next, you’ll be asked if you want Windows to be downloaded or if a local copy should be used.
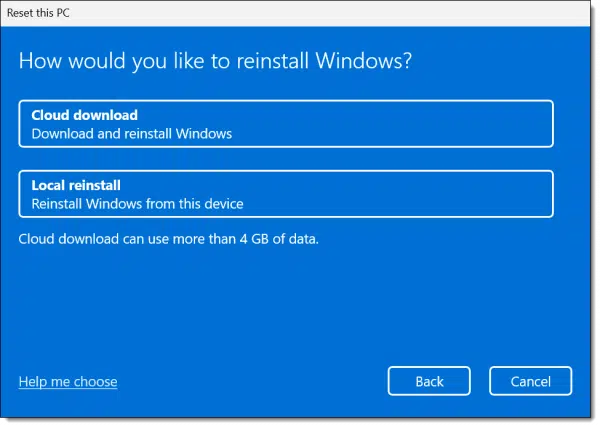
A local reinstall would be faster, but as I noted above, there’s an extremely slim possibility that the local copy of Windows used for this reinstall could have been compromised by malware.
If that’s a concern, choose a cloud download.
“Clean data” is probably a good idea
Next up is a summary of what’s been decided so far.
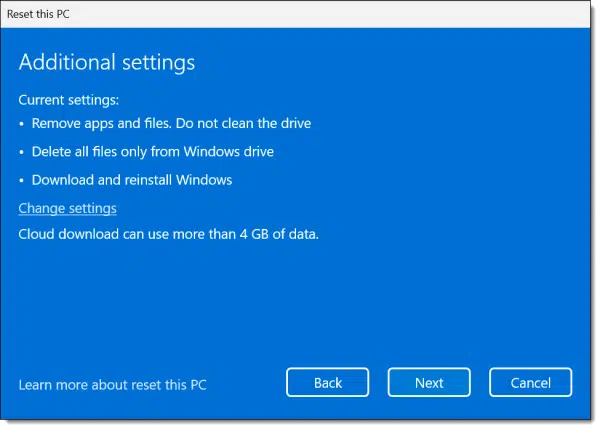
Note the phrase “Do not clean the drive”. We want to change that.
Click on Change settings.
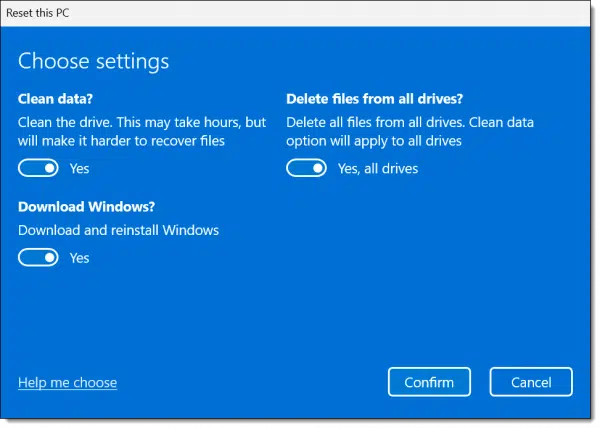
Make sure that “Clean data?” is selected. “Delete files from all drives?” is also a good idea.
But that still doesn’t cover all the possibilities.
Start with an empty drive
The only way to be sure that everything on the hard drive is truly removed is to boot from a Windows Setup disk and reinstall Windows from scratch. In other words, don’t use “Reset this PC” at all, because it relies on possibly compromised software in those hidden partitions.
Even then, there are additional steps to take.
As part of the setup process, you’ll be asked what type of installation you want.
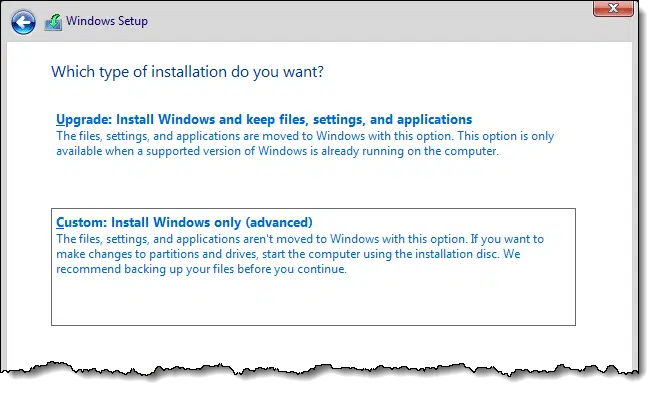
Choose Custom, which presents a list of partitions on the disk.
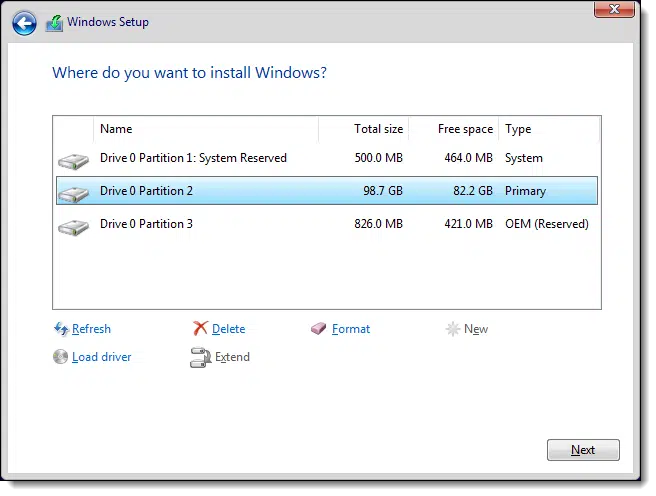
My recommendation is to delete each listed partition (click on each in turn, and click Delete).
Then continue to install Windows normally. Windows Setup will create new partitions and format them as needed.
But even that doesn’t cover everything.
The firmware dilemma
Again, it’s extremely rare, but malware entrenched in firmware is significantly more difficult to remove.
You can try the procedure outlined by your computer’s manufacturer to update your UEFI or BIOS, even if you’re “updating” it to the same version as already installed.
Other devices that could be compromised may or may not have similar procedures for updating or replacing their firmware. The problem here is knowing which are installed on your system, and whether this is an option for them.
There’s just no easy answer when it comes to firmware.
Do this
To begin with, don’t panic.
You could easily become very concerned at this point.
I’ll put it this way: you should never, ever jump to the conclusion that you have persistent malware that cannot be removed.
Never.
I hear from people all the time who are absolutely convinced they have malware that cannot be removed — be it in their BIOS, UEFI, or somewhere else. As long as I’ve been doing this, I have yet to encounter it. Not even once. As I said, it’s extremely rare. There’s always been some other, fixable explanation.
If you really suspect this is the case on your machine, take it to a professional for more detailed analysis before throwing in the towel.
Just because something is possible doesn’t mean it’s likely.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.


Leo –
Hi. Let’s say my PC gets infected today with one of those nearly impossible to remove malware mentioned in this article. But because of your friendly nagging, I have a disk image (of all disks and partitions) that was created one month ago, which I use to restore my PC.
By restoring to a disk image that was created definitely before my PC got infected:
1. Will that definitely (100%) remove the malware from my PC?
2. Or am I subject to the same malware survival possibilities (via rootkits, reserved partitions, firmware) as a user who performs a Reset This PC?
3. Which is more likely to remove that persistent malware: Reset This PC or disk image restoration?
Thanks.
1. 99.9999% yes. (There are no absolutes in this business. )
)
2. You could get infected again however you got infected before, but in restoring the image you are NOT(*) infected.
3. Assuming you know that the image does not, itself, include the infection (i.e. it was created before you became infected) then either will do it. Otherwise, reformat/reinstall, aka Reset this PC, always(*) works.
(*): 99.9999% — there are no absolutes.
You probably did something which got you the malware in the first place. If the malware comes back, you probably did it again.
That’s the most/more common scenario.
I confess, I haven’t read ALL of the article because I still use Windows 7 professional and am still reluctant to up-grade because of practical experiences by both my ex-wife and now, by my new partner with Windows 10. She stubbornly wants to stay with Apple-Mac, after her bad experience with Windows 10.
This is not to say that I am not interested to know if that problem will persist within Windows 7 but I’m beginning to feel like the poor relation. I know that you have largely migrated to Windows 10 but, and I agree with you, Windows 7 and even Windows XP, are still viable operating systems but we, too, need a little help from time to time.
Just saying…
Yeah, I’m with you, Tom. I’ve heard so many bad things about Windows 10 and its continually, incessantly defective updates that supposedly “fix” one problem only to introduce another one, that I’m sticking with Win7 until Microsoft gets its s**t together. MS needs to stop futzing around with adding features and making unnecessary changes, and throw its resources behind fixing the myriad of defects in Windows 10 once and for all.
“…but we, too, need a little help from time to time”. Perhaps. But, you are running a far more reliable OS than W10, so you’re not always running into a mess.
I use Refresh to lock the positions of the shortcut Icons on the desktop when I have them positioned the way I want them. It is frustrating to have them all move to the left of the screen after an update.
Icon Restorer ( https://iconrestorer.en.softonic.com/ ) also works well for getting the icons back where you want them.
Question: Has anyone heard about a diminishing level of malware infections as a result of the pandemic? I ask this because I’ve noticed a significant drop in crank and solicitous phone calls and junk mail. The bright side.
Malware and spam is reported as being at the same levels, but the targets & scams are changing to be more COVID-19 related.
When Reinstalling Windows “bare metal style” just press next after deleting all partitions. Windows knows what to do 😉
Only delete the drive that has Windows on it, some systems may have more than 1 drive.
Malware can be found on any drive connected to the system including external drives.
Hello, Leo! The article is good to read, I don’t know if it is related to the malware that adds on my Chrome and controls as a locked administrator or I think a ransomware? But I hope it works when I custom reset my windows 10 ent. Thank you for your additional details. Have a nice day!
If you’re referring to the message in Chrome that Chrome is “Managed by your organization”. That’s just a bug in Chrome that you can’t do anything about. It’s happened to many people including Leo and myself. It’s harmless.
I can’t understand why Goggle hasn’t fixed this after so long.
https://support.google.com/chrome/thread/40022880?hl=en
Hi Leo! I am not sure I fully understand the part about deleting and creating new partitions and formatting. Would it be possible to explain the steps further? I have 2 drives. They are not partitioned. I suppose there must be a system reserved one. If you don’t need any specific partitions, can you just delete all the partitions and leave it as is or do you need to create at least one partition per drive to format (assuming I will be seeing both drives) and Windows will create the other ones it needs. Thank you!
When you install Windows from its own bootable media (DVD or USB), it includes options to reformat the hard disk and also includes a rudimentary partition manager. By default it will set up all the appropriate partitions if the disk is completely empty, which is why I say “reformat the hard disk” implying that the entire disk is erased. Removing all the partitions is indeed one way to accomplish that.
I got attacked by ransomware, how to make sure that i format ‘everything’ when i reinstall windows
First, perform a system image backup of your infected system in case there are any recoverable files.
Next follow the instructions in this article starting with the section titled
“Start with an empty drive”
What is the best way to do a clean install if you have more than one drive? Following the instructions in “start with an empty drive”, I guess you probably can format both drives but I always heard it’s best to have only one drive connected when installing Windows as sometimes it install some files on the wrong drive. If formatting the drive without Windows first by right-clicking on the disk and choosing format, I assume there’s a chance the drive with might reinfect before it gets disconnected. I guess my question is how to get two empty drives at the same time and not mess your Windows installation.
To be clear, “not messing your windows installation” is exactly what a reformat means – it completely empties the drive, erasing Windows.
My pragmatic answer (and the one I’d probably use myself) is to simply reformat and reinstall Windows on the primary drive, and then do a complete anti-malware scan on the other. Malware generally installs itself on the system drive, so erasing that is the goal. Anything left on the secondary drive would be malware installers, which as long as you don’t run them are benign. The malware scan of that secondary drive would hopefully catch and remove them. (Alternately you could reformat the secondary drive at that time as well.)
Actually doing a two-empty drives scenario is difficult, as you’ve surmised. True “sterile technique”, as the medical folks would call it, is complex. The simplest would be to boot from something else like a Linux distribution live DVD/USB, or DBAN, or even a Windows setup disk, choosing the “repair” path and firing up a Command Prompt. In all those cases you should be able to format the two disks. If those aren’t an option, then physically disconnecting that second drive, reformatting and reinstalling Windows, then re-connecting and immediately reformatting the second drive would be the closest. It’s similar to what we did above, but just minimizes the amount of time the system is exposed to that secondary disk.
But as I said, I don’t think that level of work is generally needed.
Thanks for the quick reply! It’s a bit of basic follow-up question but I googled it and couldn’t find the answer. If I wanted go the double format route just to be extra safe and wanted to use the command prompt would Format C: H: work or would I need to do one drive and when it’s done, do the other? BitDefender and Windows Defender aren’t pick up anything on the secondary drive now so I assume it’s unlikely they would pick something up after doing a clean install of the OS.
Format works on one drive at a time. (Note that if you boot using the Windows setup disk and head to command prompt there, the drive letters will be different.)
Thank you for all the information and for the heads up. I looked up how to find the drive letters. And one last question, doing it this way is just as good as the way you suggested in the Start with an empty drive section? The no chance of hidden partition being left behind?
This Format only reformats the visible partitions and leaves the others alone. If you want to blow away all the partitions you’d need to use the FDISK command as well. I don’t believe it’s needed, though.
Most information I find about using Fdisk are for Linux systems. To use in a Windows system, is the correct way to fully wipe the hidden partitions to select disk / clean / create primary partition / select partition / active / format fs=NTFS label= drive label and then assign a letter? Also, after formatting the two drives that way, is it safe to shut down the computer to disconnect one drive before the windows installation? Thank you.
My approach would be to use FDisk to remove all partitions. If you’re about to run Windows Setup, then let Windows Setup re-create them. Heck, if you’re about use Windows Setup you can use it to remove and then re-create the partitions. See above where it says “Choose Custom, which presents a list of partitions on the disk.” You can then manually delete the partitions in that interface before installing Windows.
I do understand it might be overkill but I’m about to install a password manager and I’m a bit anxious about making sure my computer is clean first. So basically, I could delete the partitions and format both drives using the custom method? That sounds a lot simpler than using Fdisk. I assume after I formatted both drives, I can stop the process and shut down the pc to unplug a drive. Then turn it back on and continue where I left off.
Oh and just to be clear, this isn’t a quick format, this will take hours right? Or can you choose?
Well, like the entire process I suspect a full-format is overkill, but quick format will do. Honestly, I’m not sure if there’s a choice at setup time. (It probably defaults to quick.)
Unless you are giving the computer or a hard drive away, a quick format is just as good and would isolate any malware so that it wouldn’t be a threat.
Oh from searching on your website I assume a complete anti-malware scan would mean a full Windows Defender scan and perhaps a Malwarebytes scan?
Whatever your anti-malware tool happens to be, but yes, “complete” scans, making sure they include the drive in question.
So, I have hp wolf security, and the file is “isolated” from my pc. If i reinstall windows, will the malware infect my pc?
If you have a copy of the malware file visible to your computer, it might be able to be activated again. Isolating them in an antimalware quarantine folder is usually safe. If you need to keep the malware for further research, it’s safest on a USB flash drive or encrypted. Be careful with that USB drive. If you plug it into your computer, it might auto-execute if your system defaults to running executable files from a USB drive. Unless you are a malware researcher, just delete it.
Since I don’t know what “isolated” means I can’t be 100%, but I a reinstall generally erases the entire hard disk and everything on it, so I’d expect that to be erased as well.
I run a political Facebook page for Convention of States. As we approach the election my computer has been hacked. I have tried everything and am starting to wonder if I need a new computer. I purchased Windows 11 Home Edition which doesn’t allow remote connection. However, I have found the files for remote connection, phone hook-up and more. Bitdefender told me to make a report to Cybercrimes. They hacked into my system and changed my firewall rules. They aren’t hiding either. When I blocked them momentarily with Bitdefender, the next day I was blocked from logging into my router Dashboard. We have discovered they mirrored my accounts and I believe they even have hacked into my printer to monitor what I am printing/scanning. I am so frustrated. I caught a large upload in the background and was able to copy their remote sign off and a few screen shots of commands before they deleted them. Do I need a new computer?
You do not need a new computer. At worst you simply need to wipe that one, and reinstall Windows from scratch, making sure to do everything you can to keep it secure and locked down from the start. https://askleo.com/my-computer-is-infected-with-malware-should-i-just-throw-it-out/
Another thing to watch out for. When you back your data up before reinstalling, be careful you don’t copy any executable files from the backup unless you are 100% sure they are safe.
Here is a list of executable files.
.exe
.com
.bat
.msi
.dll
.cpl
.scr
.vbs
.js
.wsf
.pif
Files with these extensions don’t necessarily contain malware (most are safe), but hackers can include malware in any of these file types.
This must be an old “Ask Leo” as the replies begin in 2020. When the advice is “boot from a Windows Setup disk and reinstall Windows from scratch” …. I ask myself who has a Windows Setup Disk anymore? I think the article needs to be updated to “Windows Media Creation Tool” or some other reference.
Which is what you use to create … a Windows Setup Disk. (And I do mean creating a optical or USB disk to boot from.)
You can get the .iso file to creat a Windows Setup disk.
https://askleo.com/download-windows/
Unless I missed something, you may have omitted an important step here: a full scan for malware before backing up your files.
Otherwise, you could go through this whole reset exercise, restore your data, then inadvertently open a file or run a program that infects you all over again.
Ooops.