You might not be able to.

Not with 100% certainty, no.
There are some steps you can take to tilt the odds in your favor, though.
First, we have to define exactly what it means to “open” an attachment.

Checking if an attachment has a virus
It’s just not possible to be 100% sure an email attachment is virus-free. To reduce risk, download but don’t open the attachment; then scan it with anti-malware tools, possibly including VirusTotal. Even then, how much you trust the source of the file is key. When in doubt, don’t open it.
Open and download are different
Downloading a file is the process of copying the contents of that file onto your computer’s disk. No action is taken on the file once it arrives.
Opening a file means either:
- Loading the program (like an .exe) the file contains into RAM and following its instructions, or
- Loading the program normally used to access the contents of the file (such as loading Microsoft Word to open a .docx file).
While the former is dangerous — you’re running a program that could be malicious — the latter is also risky since so many of what we consider to be documents are capable of containing what are essentially programs as well. For example Word documents contain a robust macro language that, while designed to be secure, can have vulnerabilities like any other software.
Downloading is safe.
Opening is not.
For example, right-clicking on an attachment and choosing “Save As…” is safe. Double-clicking on the attachment, which will open it, is not.
Scanning the download
So, step one is to download the attachment without opening or running it.
Now you can run a scan on it using whatever anti-malware tool you have.
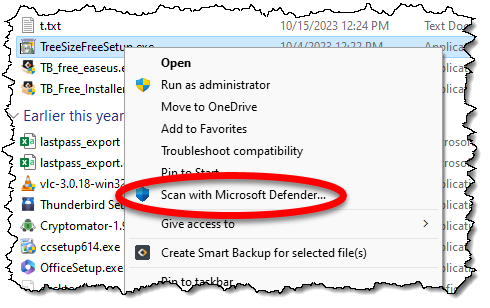
If the file is malicious, there’s a chance that your anti-malware tool will already have scanned the file when you downloaded it. Unfortunately, you can’t count on a lack of a warning to mean that the file is OK. You should still scan it manually.
Of course, if the anti-malware tool reports it as malicious, delete it immediately.
On the other hand, if the anti-malware reports it as safe… you’re not done yet.
Safe isn’t always safe
Here’s the catch: not all anti-malware tools catch all malware. Just because your anti-malware tool reported the file safe doesn’t mean with 100% certainty that it is, in fact, safe.
You can stack the deck further in your favor by using multiple tools. One such approach is to upload what you just downloaded to a service like VirusTotal.
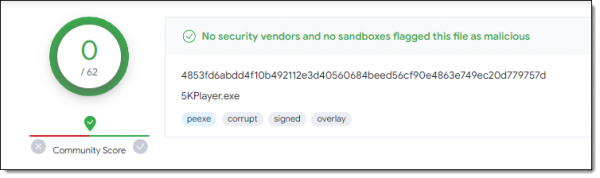
VirusTotal runs the file through multiple anti-malware tools.
And yet, while a “safe” result from that tool is a really, really good indication, it’s still not complete, absolute 100% proof of safety. You just can’t prove a file — any file — isn’t malicious.
It all comes down to trust.
Do this
Do you trust the source of the download? Do you trust the various things you’ve done — from your gut feeling to your anti-malware tools to whatever other steps you’ve taken?
If not, if there’s any doubt, then don’t open that file. Treat it as malicious and proceed accordingly. Depending on the file, it might mean reaching out for help, getting the file from a more reputable source, or whatever else makes you feel more secure about what you’ve just downloaded.
I talk about staying safe and how to do so every week in my newsletter. Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.




Whenever people send screenshots as .docx or .pdf files to Ask Leo!, I don’t open them. I delete those and ask the sender to resend them as image formats, .jpg or .png, for example.
By default, MS Office defaults to not executing macros, but somehow, I still have the habit of erring on the side of caution.
VirusTotal is probably a profit-making site . . . if it offers this service to anyone, for free, how does it show a profit? Do you know? My uninformed guess is that it grabs as much of your personal information as it can, and uses. sells, or probably both, that personal information. If you know, please let us know as well!
Thanks!
I trust ’em. They have an API that they make available for business and commercial use for a fee.
I seldom ever receive attachments in emails. When I do, my rules are as follows:
1. If I know the sender, and I can contact them, I do so to confirm they sent the message with an attachment.
2. If I know the sender but cannot contact them, or they’ve confirmed they sent the message with an attachment (above), I download the attachment and scan it using both Microsoft Defender and MalwareBytes (I may start using Virus Total’s online tool as well now that I know it exists). If it passes all these tests, I take a chance and open it, but only if it is purported to contain information I must have.
3. If I don’t know the sender (or it fails any of the above tests), I delete the message along with it’s attachment. I don’t stop at Go. I don’t collect $200.00. I simply get rid of it and never look back.
My behavior with unexpected email messages is very similar to what I’ve listed above:
1. If I know the sender and can contact them, I do so to confirm they sent the message.
2. If I know the sender but cannot contact them, or they’ve confirmed they’ve sent the message and I trust them implicitly (in either case, there are very few people who meet this bar), I take a chance and open the message, but I NEVER click ANY link in any email message without checking that the URL is consistent with the link’s label.
3. If the message fails ANY of the above tests (especially implicit trust of the sender), or I have any doubt, however small, I delete the message or send it to my Spam/Junk folder. As above, I don’t stop at Go. I don’t collect $200.00. I just get rid of it and never look back – EVER.
I suggest you develop your own set of rules for email (and Internet) use. By following my rules, both when using email and surfing the Internet (essentially, when in doubt – DON’T!), and applying a very healthy dose of skepticism to everything that comes from the Internet (that includes email and any web site I visit), I have avoided contracting any malware since the early 1990s when I downloaded an infected file from a BBS site (prior to the advent of the World Wide Web), even though I do my fair share of ‘surfing’.
My2Cents,
Ernie (Oldster)
Another good idea/method is to use either a sandbox or virtual machine to open attachments.