Not all encryption is equal, and why you should care.
A recent news story about how Facebook turned over personal chat transcripts in response to a court order highlights why end-to-end encryption matters as much as it does.
Yes, of course, there are privacy issues, and perhaps assumptions we shouldn’t be making when using services provided by large corporations like Meta, Google, Microsoft, and others. This isn’t about that.
There’s a bit of technology you need to understand if privacy really matters to you.
Become a Patron of Ask Leo! and go ad-free!

End-to-end encryption
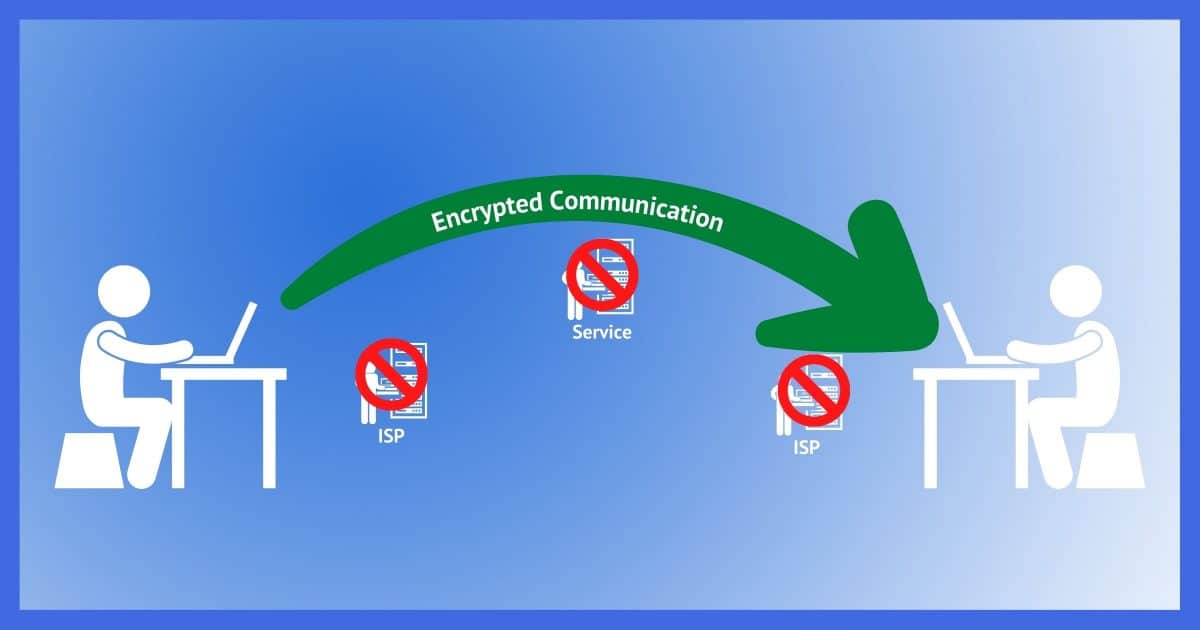
End-to-end encryption ensures that information being communicated is visible only to the individuals at either end and not to anyone in the middle, including the service provider. Given that service providers can be compelled to hand over information to law enforcement, end-to-end encryption ensures they have nothing to hand over. When exchanging sensitive information, make sure to use tools that explicitly use end-to-end encryption.
End-to-end encryption
End-to-end encryption is nothing more than data being encrypted in such a way that it can be seen only by individuals involved in a communication and not anyone anywhere in the middle.
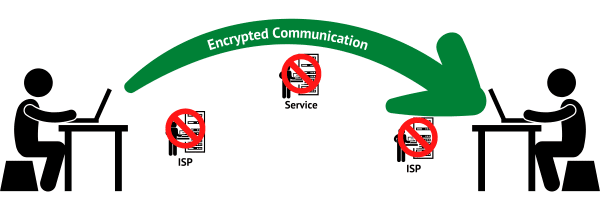
Your ISP can’t see it, the other person’s ISP can’t see it, even the service you’re using can’t see it. All they see is encrypted blobs of random data. The data is visible only at the endpoints.
It’s encrypted from one end to the other.
Facebook would not be able to turn over anything that crosses their server using end-to-end encryption because they couldn’t understand what it contained.
End-to-middle encryption
End-to-middle encryption is quite common.
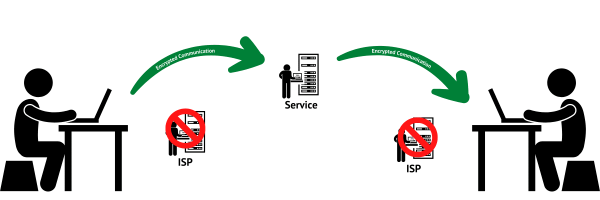
In this scenario, information is encrypted as it’s sent to the service you’re using, where it’s decrypted. It’s then re-encrypted and sent on to the final recipient, where the tool being used decrypts it.
The important thing to notice is that the service in the middle can see the unencrypted information. If you trust them, that’s peachy. If you don’t, it’s a problem.
Why would this scenario even exist?
In a word (or rather, an acronym): https. Https1 is the most common way of encrypting communication between your computer and the services you use. The whole intent of https is to provide encryption between you and the services you use. This protects you from a variety of issues, including your ISP seeing the data you’re exchanging, as well as anyone snooping in on the connection, such as on an open Wi-Fi hotspot.
The encryption is between you and the service you’re using, but no further. The service can see what you’re up to. Sometimes that’s necessary. Making a post on social media, for example, requires that the service have access to what you want to post. In other cases, it’s enough encryption as long as you trust the service.
It’s more than the service
As our Facebook users learned, it’s not always about trusting the service. Regardless of how you feel about Facebook specifically, this issue transcends service providers.
It’s often about the laws, rules, and regulations the service providers operate under. In Facebook’s case, it didn’t matter whether they wanted to provide the information or not; they were legally compelled to.
So, do you trust the government entities that regulate the provider you’re using? And if your conversation crosses jurisdictions — be it a city, state/province, or country boundary — do you trust the regulators at both ends? Any of them might compel information disclosure.
With true end-to-end encryption, there’s no information for the service, or anyone else in the middle, to see or disclose.
The solution
If it matters to you, the solution is to use an end-to-end encrypted service.
While there are supposedly plans for Facebook’s messaging service to be end-to-end encrypted someday, that day is not today. Clearly Facebook currently has access to all your Messenger messages.
WhatsApp, also owned by Facebook, highlights its end-to-end encryption.
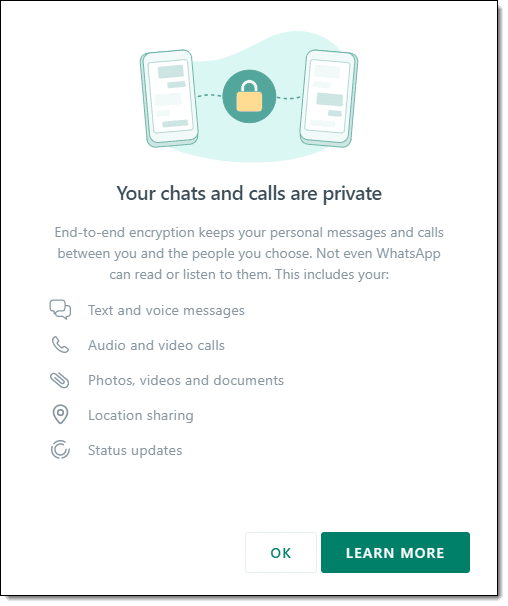
Tools like Telegram and Signal also highlight this feature.
Not a solution: VPNs
VPNs do not solve this problem.
A VPN encrypts everything, but only as far as the VPN provider’s servers. Using the Facebook Messenger example, which is not end-to-end encrypted, here’s what happens with a VPN.
- Facebook Messenger encrypts the data to send to Facebook.
- Your VPN encrypts the data again to send to the VPN server.
- The VPN Server decrypts its layer and sends the data — still encrypted by Facebook Messenger — on to Facebook.
- Facebook decrypts the data. At this point, the messages are visible to Facebook.
- Facebook encrypts the data.
- Facebook sends the data on to the Facebook Messenger recipient.
- Facebook Messenger decrypts the message on the recipient’s machine.
- The recipient can read the message.
The VPN provided an additional layer of encryption and security, but only between your machine and the VPN service’s servers.
Do this
If your privacy truly matters, then it’s important you know how the tools you use work, and choose one with an appropriate level of privacy and security.
Personally, I use Facebook Messenger all the time, but I have no expectation of privacy. If privacy matters, I use Telegram.
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.




Leo, you wrote:
“With true end-to-end encryption, there’s no information for the service, or anyone else in the middle, to see or disclose.”
Well, actually, yes, technically there is something to see or disclose: the encrypted data.
This doesn’t usually matter, but, it may be of concern if:
1. You’re using low-level encryption, or a broken encryption algorithm; or
2. The interceptor is the CIA, NSA, DHS, or some similar agency with specialization in cryptanalysis (“code-breaking”).
Ordinary law enforcement might be able to decrypt the message if your algorithm is low-level or broken (I wouldn’t trust ROT13 very far, for example), but even this is doubtful. With decent encryption they can do nothing. If they think the matter important enough, they might pass it on to one of the agencies above — but other than that you shouldn’t have to worry.
Just do be aware that the interceptor or seizure authority does receive something. Whether that “something” is of any use to anyone is an entirely different matter.
1. Solution: use good encryption. even 7Zip has high level encryption.
2. If a 3 letter organization tries to crack your messages, your problem is way beyond the scope of this article.
“If a 3 letter organization tries to crack your messages, your problem is way beyond the scope of this article.”
Heh. Yep!
I could never understand why Facebook Messenger is taking so long to implement end-to-end encryption. They’ve been doing end-to-end encryption on WhatsApp for years. I know changes like that aren’t trivial, but Meta is worth over half a trillion-dollars, the 7th richest in the world. It surprises me that for such a huge corporation, their website is the buggiest I’ve ever used.
They’re only paying attention to half of “move fast and break things”.
Interesting article. How safe is it to use eMule, with the encryption box ticked? Can anyone ‘see’ what the traffic consists of?
It should be fine. Most people run into problems with what they’re sharing (copyright violations) rather than how they share it. Encryption would presumably hide what you’re downloading, but I’d recommend sticking to only legal stuff to start with.
Am I missing something? Isn’t the service that applies the encryption, Whatsapp or whatever, capable disapplying it?
No. The encryption is done on your computer and the computer of the person you’re texting or talking to. Encrypted data leaves your computer and stays encrypted as it passes through Meta’s servers ans is decrypted on the recipient’s computer.
But surely the service knows what encryption algorithms have been applied and so are in a position to disapply them?
All Microsoft sees is bits and bytes. They don’t analyze the contents.